Researchers are encouraging developers who use Magento to remain vigilant about securely configuring their sites, as attackers have been embedding credit card swipers in sites running the open source e-commerce platform.
The swipers, or scrapers, are bits of malicious code that collect credit card numbers, login details and other information and forward it to attackers. While criminals have been targeting sites running the platform for months, they’ve only just recently started embedding that information in obscure image files.
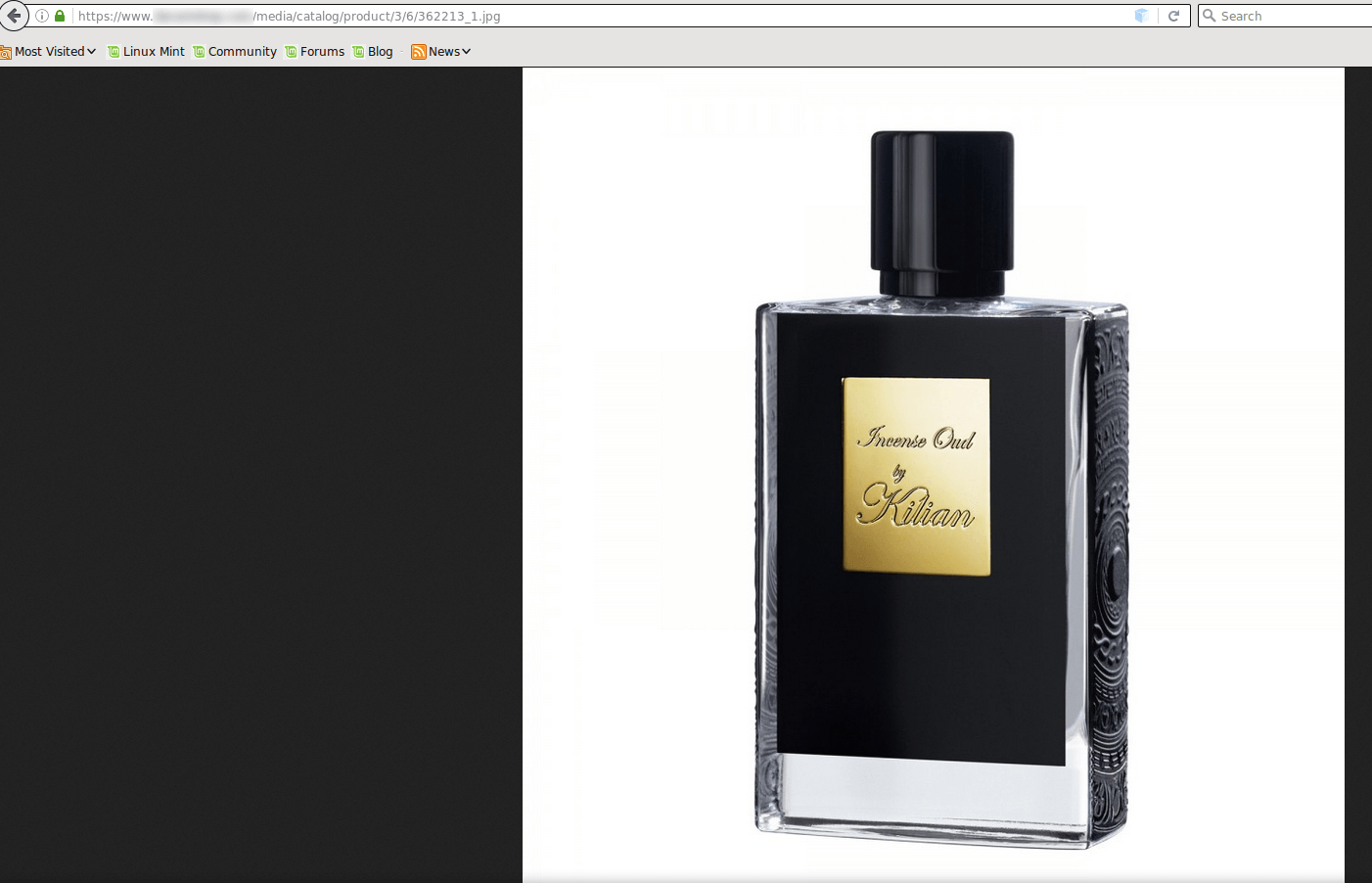
In an even more confounding twist, in one recent instance an image that was hiding stolen credit card numbers was legitimate and publicly viewable, meaning an attacker wouldn’t even have to go to the trouble of accessing the site to get the information. They could simply view or download the image from the affected site.
While a cursory scan of the affected site came up clean, Ben Martin, Remediation Team Lead at the security firm Sucuri, eventually discovered the swiper code, along with the image file that stores the stolen credit card details, nestled in a Magento core file, “Cc.php.”
It’s rare for the image file to actually contain a real image, Martin wrote in a blog post on Monday; usually users receive an error when they try to access image files storing data. In this case, the image not only worked, it was also of a product, a perfume, being sold on the site.
“Most website owners would be none the wiser if they came across this image and opened it to make sure it worked,” Martin wrote in the blog.
It wasn’t until he scoured the image’s source code (see below) that Martin discovered it was composed of stolen credit card numbers. Most of the victims were based in the United States but some cards belonged to customers in Japan, Turkey, Saudi Arabia, and Vancouver, Canada, according to Martin.
“… No one really suspects an image file to contain malware. This gives the attacker a secret place to store data,” Martin wrote, “If the attacker had chosen to store the stolen credit card details in a simple text file then it might be easier for someone to discover it and take steps to remove the hack.”
Martin said Sucuri deleted the image so no one would be able to download it going forward but it’s unclear how widespread the credit card swiper threat is; Sucuri did not immediately return a request for comment.
When contacted about the research on Tuesday, a spokesperson with Magento said they didn’t believe Sucuri contacted the company about the issue, but stressed it wasn’t a Magento-specific vulnerability.
“The attacker injected their malicious code into our legitimate Cc.php file, which indicates the site is not following Magento security best practices and specifically doesn’t have proper/secure filesystem ownership and permission setting,” Magento said.
“Our investigations of recent malware reports, like the one highlighted by Sucuri, haven’t revealed new attack vectors. Instead, attackers are taking advantage of existing, unpatched vulnerabilities, poor passwords, and weak ownership and permission settings in the file system.”
Attackers have long used steganography, the art of concealing messages – or in this case credit card numbers – in data.
Last month Microsoft patched a vulnerability in Internet Explorer and Edge that was being exploited by a malvertising campaign and using steganography to obscure its attacks. The group AdGholas, hid code in JavaScript filtering code, which used an API to read a PNG that went on to extract more JavaScript.
Magento, which powers roughly 240,000 online stores and was owned by eBay until it was sold last summer, has been remained an appealing target for attackers over the years.
Earlier this year a specialized strain of ransomware, KimcilWare, was encrypting web shops that used the platform. Once installed, attackers were encrypting website files and demanding Bitcoin payment – between $140 USD and $415 USD – for decryption. Magento said at the time that it believed the attackers weren’t singling the platform out in particular, but “more general web server vulnerabilities.”
Magento pushed out patches to address a handful of vulnerabilities – none related to the issue uncovered by Sucuri – last week. Those updates included fixes for a critical remote code execution vulnerability, a SQL injection vulnerability, and a trio of stored cross-site scripting vulnerabilities in its Enterprise Edition and Community Edition of the software.