For the last month, attackers have used a combination of phishing and typosquatting to carry out a campaign aimed at stealing Bitcoin and blockchain wallet credentials.
More than 100 phony Bitcoin and blockchain domains have been set up so far, many which mimic legitimate Bitcoin wallets. Most of the sites were registered on May 26 and more continue to pop up daily suggesting the campaign is still in the early goings.
Artsiom Holub, Dhia Majoub, and Jeremiah O’Connor, researchers with OpenDNS’ Security Labs, traced connections between IP addresses, name servers and Whois indicators over the last few weeks in order to determine the scope of the campaign.
Cyren, an Israeli cloud-based security firm, spotted the first signs of life from the campaign in early June when it observed the domain blocklchain[.]info spreading through a pay-per-click advertising scam via Google AdWords. If a user was tricked into visiting the site – a replica of the real deal – and actually logged in, they would have handed their Blockchain credentials over to attackers.
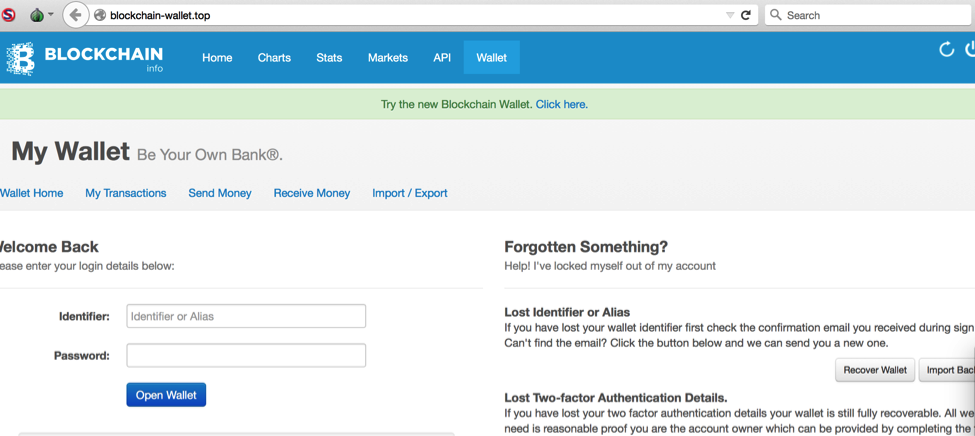
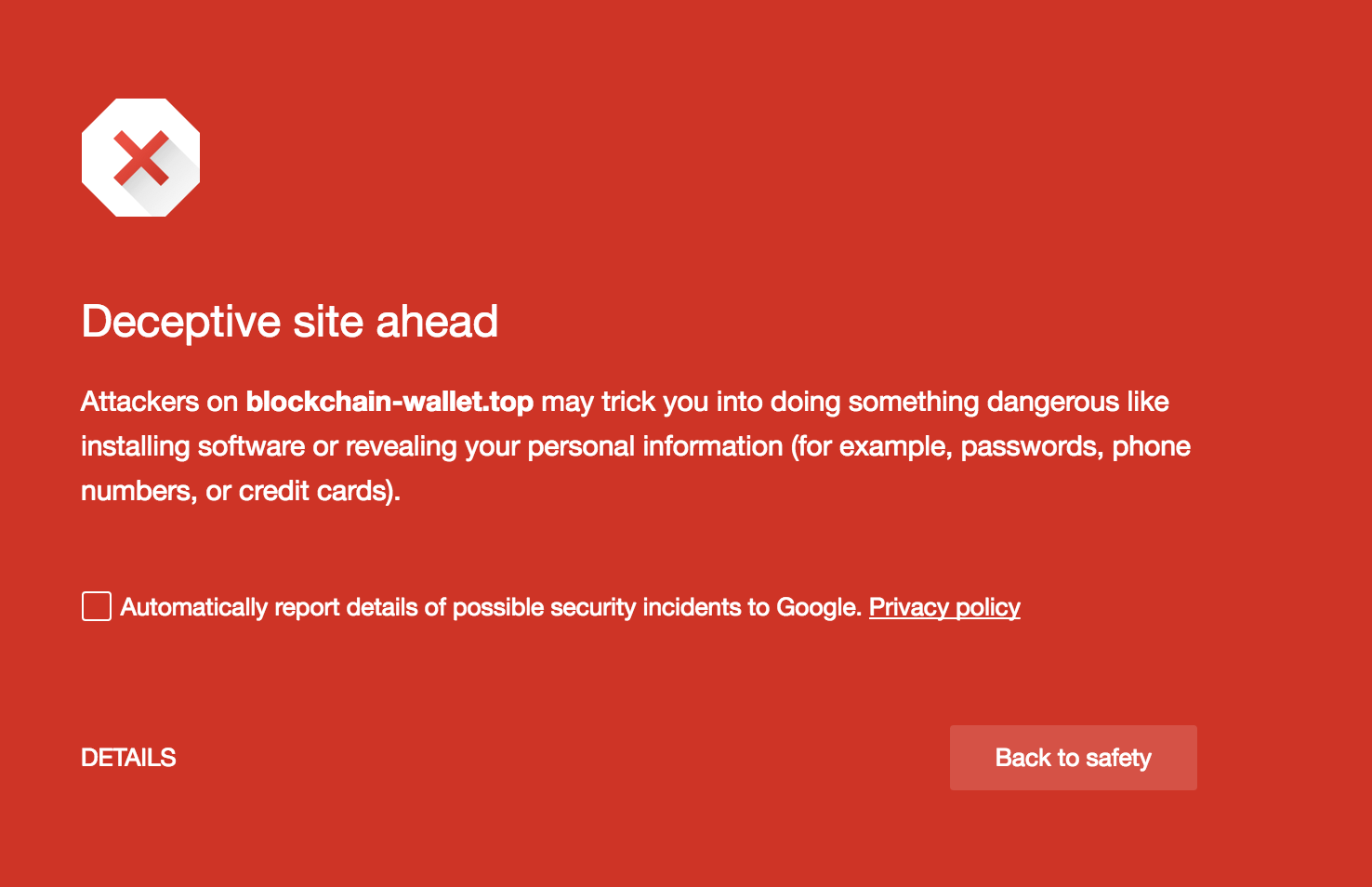
A day after Cyren posted its research, OpenDNS went further down the rabbit hole and noticed a phishing attack at blockchain-wallet[.]top. Like the site Cyren found, the one OpenDNS found looks startlingly similar to the actual Blockchain.info site, the popular transaction database for Bitcoin. The site, which even shares the same logo and teal-colored navigation bar, is still active but Google has since branded it as a deceptive site, warning users attackers may be using it to get users to reveal personal information.
OpenDNS detected a similarly obfuscated URL, blolkchain[.]com connected to the same IP a few days later, on June 13, which prompted researchers to look into the IP and similar IPs in that range. They found dozens of suspicious looking sites, including multiple Blockchain spoof sites like blokchain-wallet[.]info and localbitcons[.]com.
Bitcoin addresses have to be Base58Check-encoded in order to avoid confusion between similar looking characters like capital “O” and the number zero. As the researchers point out, that’s why the phishing domains they found rely so heavily on typosquatting, or when Internet users input a website address into a web browser, make typographical errors, and get brought elsewhere.
“From these examples, it’s clear the attackers have a solid understanding of protection mechanisms used by Bitcoin addresses and are trying to defeat them,” the researchers wrote Monday.
Looking at the IPs further the researchers discovered they all shared a provider that’s had three different names over the last year and has been previously called out for hosting what OpenDNS refers to as “criminal and toxic content.” Three anonymous offshore hosting companies have utilized the company’s IP space to peddle child pornography, child modeling, fake merchandise, and a smattering of phishing sites, Blockchain and iCloud-related.
Originally Ecatel, the service used to be based in the Netherlands before it changed its name to QUASINETWORKS and moved offshores to Seychelles in December 2015. It changed its name to Novogara in April of this year.
Researchers cross-referenced hosted domains and Whois registration for the IPs to identify six different emails used to register – and still being used to register – blockchain spoof domains
“Investigating IP space, name servers and Whois indicators sheds light on how frequently criminal actors recycle their infrastructures and resources, and makes evident just how heavily they rely on bulletproof offshore hosting providers to deliver their malware and phishing campaigns,” the researchers said in a blog entry.
OpenDNS said it blocked the malicious IP ranges for its customers and that going forward wallet companies should strengthen their security in order to prevent phishing and typosquatting attacks similar to ones used by the campaign.
The news comes at a time when interest around the cryptocurrency is burgeoning. Bitcoin’s price has skyrocketed over the past several months, a trend many have tied to an influx of ransomware. When victims are hit by the ransomware attackers usually demand payment in Bitcoin. In situations like this users are often supplied with instructions on how to purchase Bitcoin using a credit card in exchange for a decryption key.
The cost for keys runs the gamut from low to higher figures. For instance the ransomware RAA, discovered last week, asked users for as much 0.39 BTC ($ 250) while another strain of ransomware, Black Shades, uncovered earlier this month, only asked users to pay up 0.07 Bitcoin, or $30, to unlock their files.