Ransomware continues to elevate itself as perhaps the most worrisome crossover threat affecting consumers and businesses.
Already this week, we’ve had an update to the dangerous Cryptowall family of malware that includes new encryption features making that strain of ransomware harder to decrypt. This news came on the heels of a summer-long adoption of Cryptowall in particular by the virulent Angler exploit kit and other less prevalent malware toolkits.
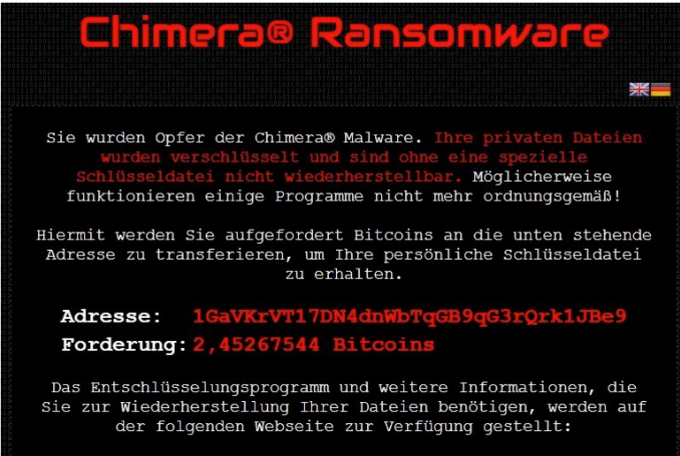
Now comes another expansion of the ransomware threat from Chimera, malware that’s primarily targeting companies in Germany, not only encrypting files and network drives, but also making veiled threats to publish encrypted data online if the extortion demands are not met.
The Anti-Botnet Advisory Centre, or Botfrei, published a note about the Chimera update this week. Chimera has been in circulation for two months, spreading via links in business-related emails.
“Several variants of sender addresses try to target specific employees within a company and they have one thing in common: within the email, a link points to a source at Dropbox, claiming that additional information has been stored there,” Botfrei’s report said. “The users get asked to download these files from there.”
If the user clicks on the link, the Chimera malware downloads and begins encrypting locally stored data and seeks out network drives connected to the compromised computer. All the file extensions are then changed to .crypt.
Once the victim reboots, they’re greeted with the customary ransom note demanding £630 (about $685 USD) to be paid in Bitcoin. The note also promises to publish the personal data and photographs stored on the computer online if the ransom isn’t paid.
“At this point, there is no evidence whether personal data has been published on the internet or not – same as we haven’t heard of a case where the cybercriminals have released the data after paying the 630 EUR in Bitcoins,” the Botfrei report said.
This is a new twist for ransomware campaigns, most of which just encrypt data locally and promise to deliver the private encryption key unlocking the captive data. It’s rarely stolen, or copied elsewhere.
Clearly, ransomware authors aren’t sitting still. This week’s Cryptowall update, dubbed Cryptowall 4.0 by researchers at Bleeping Computer, has gone a step beyond where its predecessor had by encrypting not only locally stored data but also file names.
“I’m surprised more don’t it; this makes it significantly harder to recover files except for paying the ransom,” said independent researcher Nathan Scott, who analyzed the Cryptowall 4.0 sample with Bleeping Computer. “If you try to do a forensic data recovery, the files show up with these weird names and the user doesn’t know what file is what. No one knows any structure in files any more.
“The only way to regain your data is a complete backup,” Scott said. “If you don’t backup, the only way to get the data back is to pay the ransom.”