Hacking tools allegedly developed by the National Security Agency (NSA) were being used in the wild by at least one APT long before the Shadow Brokers released the now-infamous trove of U.S. cyberweapons, new analysis suggests.
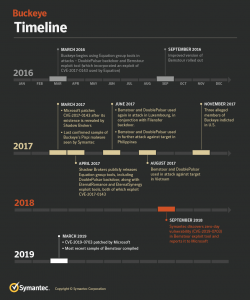
According to researchers at Symantec, an attack group affiliated with the Chinese government known as Buckeye (a.k.a. APT3 or Gothic Panda) was able to commandeer a Windows zero-day and other tools from the NSA-linked Equation Group, which it used in attacks starting in March 2016. Those attacks continued through to Buckeye’s apparent disappearance in 2017 (three of its members were indicted in the U.S.) and beyond, with evidence of the tools being used well into 2018. Researchers said they weren’t sure if Buckeye passed the tools off to another outfit or if it continued operating longer than they originally thought.
In any event, the findings mean that Buckeye was carrying out espionage activity using allegedly U.S.-developed tools at least a year prior to the April 2017 Shadow Brokers leak.
“Variants of Equation Group tools used by Buckeye appear to be different from those released by Shadow Brokers, potentially indicating that they didn’t originate from that leak,” Symantec researchers said in a posting on their analysis, released Monday. “Based on the timing of the attacks and the features of the tools and how they are constructed, one possibility is that Buckeye may have engineered its own version of the tools from artifacts found in captured network traffic, possibly from observing an Equation Group attack.”
Or, perhaps Buckeye was able to hack the Equation Group server, or recruit an Equation Group member or associate to its cause, Symantec said.
As for the zero-day (CVE-2019-0703), it remained in the shadows until it was found and reported by Symantec to Microsoft in September of last year and finally patched in March. It allows for the leaking of information and can be exploited in conjunction with other vulnerabilities to attain remote kernel code execution, the researchers said.
Buckeye Before Shadow Brokers
In late 2016, the Shadow Brokers group attempted to auction off what it claimed was a deep well of cyberattack weapons lifted directly from the NSA. It didn’t have many takers – presumably because the claim to have such a cache of tools seemed far-fetched – so the group released some samples on a progressive basis, before dumping a huge tranche online in April 2017. Those tools in the final dump included the DoublePulsar backdoor, the FuzzBunch framework, and the EternalSynergy, EternalRomance and EternalBlue exploit tools.
The latter of course is best known for its role in the devastating May 2017 WannaCry outbreak.
Symantec researchers found via a forensic analysis that beginning in March 2016, Buckeye began using a variant of the DoublePulsar spyware; the APT delivered it to victims using a custom exploit tool called Bemstour that was specifically designed to install DoublePulsar. Bemstour itself was delivered to victims via a known Buckeye custom malware called Pirpi – which led to the attribution.
“Bemstour exploits two Windows vulnerabilities in order to achieve remote kernel code execution on targeted computers,” the researchers said. “One vulnerability is [the previously mentioned] Windows zero-day vulnerability discovered by Symantec. The second Windows vulnerability (CVE-2017-0143) was patched in March 2017 after it was discovered to have been used by two exploit tools—EternalRomance and EternalSynergy—that were also released as part of the Shadow Brokers leak.”
The variant of DoublePulsar used in the first attacks performed by Buckeye was different to that leaked by the Shadow Brokers, according to the firm.
“It appears to contain code to target newer versions of Windows (Windows 8.1 and Windows Server 2012 R2), indicating that it is a newer version of the malware,” the team said in the analysis. “It also includes an additional layer of obfuscation. Based on technical features and timing, it is possible that this obfuscation was created by DoublePulsar’s original authors.”
The purpose of all the attacks was to acquire a persistent presence on the victim’s network, in keeping with espionage tactics.
Interestingly, Buckeye was never seen using the FuzzBunch framework, which is designed to manage DoublePulsar and other Equation Group tools, in its attacks.
“This suggests that Buckeye only managed to gain access to a limited number of Equation Group tools,” according to Symantec.
What Happened to Buckeye?
What happened to Buckeye is a bit of a mystery.
Buckeye’s history goes back to 2009, Symantec said; it specialized in espionage on U.S. corporate targets. In May 2017 the group, already widely believed to be a China-based threat actor, was directly connected to the Chinese Ministry of State Security (China’s equivalent of the NSA) by Recorded Future.
“Our conclusion is, that for the first time, we have been able to link with high confidence a threat actor with the Chinese MSS,” Samantha Dionne, researcher with Recorded Future, said at the time. “In the past the assumption was APT3 was related to the MSS. But, there has never been enough information to make the connection. Now we can make that determination.”
Activity involving known Buckeye tools ceased in mid-2017, after which some of its members were indicted. But the Bemstour exploit tool and the DoublePulsar variant used by Buckeye continued to be seen after that, in conjunction with different malware, according to Symantec – specifically, the Filensfer backdoor.
Filensfer is not associated specifically with Buckeye or any one group, and has been seen used in targeted attacks since at least 2013, according to Symantec; so, researchers aren’t sure if Buckeye passed the baton onto a different threat group, or whether it simply changed tools and tactics. It’s possible that it abandoned it’s known signature approaches in order to better operate under the radar.
“Development of Bemstour has continued into 2019,” the researchers said. “The most recent sample of Bemstour seen by Symantec appears to have been compiled on March 23, 2019, eleven days after the zero-day vulnerability was patched by Microsoft … However, aside from the continued use of the tools, Symantec has found no other evidence suggesting Buckeye has retooled.”