UPDATE: Twelve seemingly legitimate Chrome browser extensions installed by more than 180,000 users are injecting advertisements on 44 popular websites.
According to a Barracuda Labs report, the extensions can be found in the official Chrome Web Store. They advertise themselves and operate as games but also require permission to access “your data on all websites,” so that they can inject advertisements into the user’s browser on any website that person visits. All of the allegedly spammy extensions are registered to the same developer organization: www.konplayer[.]com.
Threatpost attempted to reach out to the people responsible for developing the extensions but was not able to. It appears that some of Konplayer’s extensions have been removed from the Chrome Web Store.
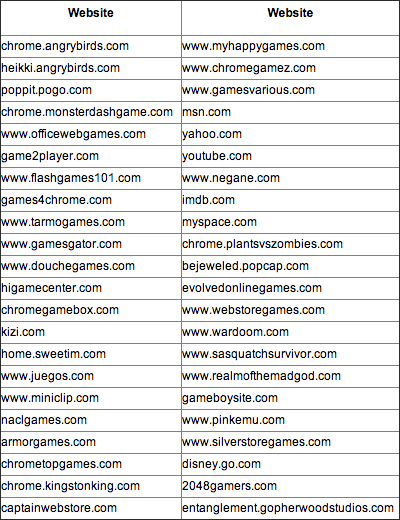
You can see a list of affected websites in the following graphic:
The malicious JavaScript responsible for injecting advertisements isn’t contained directly within the extensions themselves. Instead, the extensions contain a reference URL to www[.]chromeadserver[.]com, which contains the malicious JavaScript. As Barracuda Labs research scientist Jason Ding notes, that domain is made to appear as if it is owned and operated by Google but, of course, it is not.
Barracuda Labs then downloaded and decoded the JavaScript contained on URL referenced above. At first the code seemed benign, but a closer examination revealed that it was responsible for injecting banner advertisements into empty spaces in various positions on popular websites visited by users that had downloaded one of the spam extensions.
In an interview with Threatpost, Ding explained that the permissions sought by these extensions are unnecessary considering that actual purpose of the extensions. Furthermore, the extensions constitute a violation of Google’s terms of service because they mislead users about their purpose. Unfortunately, Ding claims that Google does not have a good way of policing for spam in their Web Store.
“If an extension advertises itself as a game, it should NOT ask for any extra permissions,” Ding told Threatpost. “In most cases, it only need to redirect users to the targeted game websites (which has the game or more games). Or it can ask for the permission for a specific website that the game was hosted at, not the permission ‘Access to data on all website’.”
Ding continued:
“Some other extensions do need the ‘Access to data on all website’ permission, such as the Ads Block extension: of course, it need such permission, so it can remove ads (html elements) for all the websites you are browsing.”
The code used by these extensions is similar to the code used by a group of scammers examined in a prior report issued by Baracuda Labs. Ding believes that the group responsible for Konplayer[.]com is the same group that once distributed their malicious extensions from Playook.info.
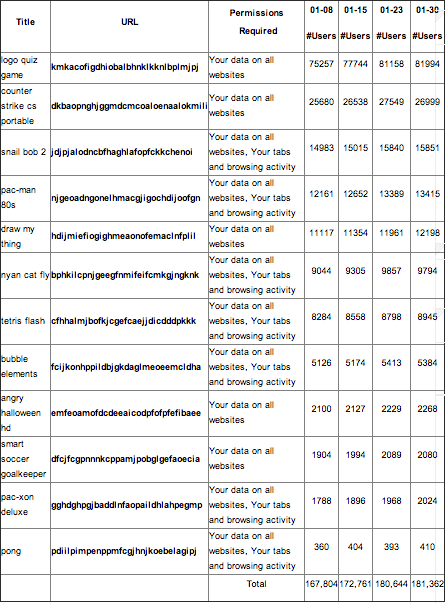
The graph below contains the names of the allegedly malicious extensions: