Hackers stole credit and debit card information from millions of consumers who have shopped at Saks Fifth Avenue and Lord & Taylor stores. Parent company, Hudson’s Bay Company, confirmed the security breach on Sunday, stating that customer payment card data at certain Saks Fifth Avenue, Saks Off 5TH and Lord & Taylor stores in North America are impacted.
“HBC has identified the issue, and has taken steps to contain it,” the company said in a statement. “Once the Company has more clarity around the facts, it will notify customers quickly and will offer those impacted free identity protection services, including credit and web monitoring. HBC encourages customers to review their account statements and contact their card issuers immediately if they identify activity or transactions they do not recognize.” HBC did not respond to specific questions about the scope, timeframe and location of the breach beyond what was listed out in its statement.
The breach was first highlighted by cybersecurity firm Gemini Advisory, which linked the stores to stolen information recently posted on the dark web by hacking syndicate JokerStash, also known as FIN7. On March 28, JokerStash announced the sale of over five million stolen credit and debit cards, said the security company.
“Several large financial institutions have confirmed that all tested records had been used before at Saks Fifth Avenue, Saks Fifth Avenue OFF 5TH, a discounted offset brand of luxury Saks Fifth Avenue stores, as well as Lord & Taylor stores,” the company said in a post.
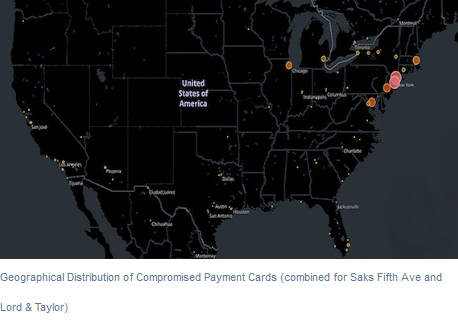
Gemini Advisory said that it appears that all Lord & Taylor and 83 US-based Saks Fifth Avenue locations have been compromised, and the majority of stolen credit cards were obtained from New York and New Jersey locations. Gemini Advisory estimated the window of compromise to be May 2017 to present.
“As of this writing, only a minor part of compromised records have been offered for sale, with approximately 35,000 records for Saks Fifth Avenue and 90,000 records for Lord & Taylor,” said Gemini Advisory.
Despite its massive scope, credit card information is the only data that appears to be impacted by the breach, at least thus far – Saks Fifth Avenue said in a statement that there is no indication that Social Security or Social Insurance numbers, driver’s license numbers or PINs have been impacted.
HBC also said that the breach only impacts North American stores, and there is currently no evidence that other brands that it owns – including Hudson’s Bay, Home Outfitters or HBC Europe – were impacted.
JokerStash revealed the release of stolen information from Saks Fifth Avenue and Lord & Taylor in a batch of compromised records called BIGBADABOOM-2.
JokerStash has had a long streak of successful high-profile breaches, including Whole Foods, Chipotle, Omni Hotels & Resorts, and Trump Hotels. All these breaches were point of sale (PoS) system hacks that used malware to infect the PoS terminals and carry out the attack.
JokerStash is also known as FIN7, was identified in March 2017 by researchers at FireEye in a series of fileless malware campaigns focusing on financial institutions and government agencies. The group has since then evolved its attacks to target restaurants across the US, using fileless malware to seize system control and install a backdoor to steal financial information.
FIN7 is also closely associated with the Carbanak group, which is notorious for stealing as much as $1 billion from more than 100 financial institutions in a string of attacks. Last week, the suspected leader behind Carbanak was apprehended, according to the European Union Agency for Law Enforcement Cooperation.
POS breaches overall have been on the rise as of recent, with fashion retailer Forever 21 in January confirming a breach from 2017 resulting in the theft of credit card data belonging to an undisclosed number of customers. Meanwhile, in October Hyatt Corp warned customers of a credit card breach in 41 of its hotels.
However, Gemini Advisory said that the “potential damage to cardholders could be significantly higher in the latest hacking attack” because, unlike shoppers who frequent more affordable retail locations like Forever 21, banks may not be able to identify unusual shopping patterns in shoppers who frequent more high-end stores such as Saks Fifth Avenue.
“However, cardholders who frequently shop at luxury retail chains like Saks Fifth Avenue are more likely to purchase high-ticket items regularly; therefore, it will be extremely difficult to distinguish fraudulent transactions from those of a legitimate nature, allowing criminals to abuse stolen payment cards and remain undetected for a longer period of time,” said Gemini Advisory.
Gemini Advisory did not respond to a request for comment regarding its intelligence behind the breach. However, the company said in its blog post that “this recent breach once again emphasizes the importance of a transition to the more secure EMV POS terminals in retail operations. Although many large retailers managed to migrate entirely from older generation magstripe terminals to EMV in 2017, several nationwide chains still have not done so.”