The bloom is on the criminal cryptomining of computer resources and the reason is obvious – it’s lucrative. One cryptomining gang tracked by researchers over the past six months minted $7 million with the help of 10,000 computers infected with mining malware.
The rise of malicious cryptomining isn’t a shocker to anyone following cybersecurity. However, what is startling is the rise in the use of sophisticated and complex techniques that some groups now use. Many cryptomining groups have adopted hacking techniques and tools typically only seen by sophisticated APT threat actors.
In a report released Monday by Kaspersky Lab, researchers profiled three groups of cryptominers that represent this new breed cryptojacking criminals. Following the same huge growth arc as ransomware, these groups are quieter by nature and unlike in-your-face ransomware bullies, are more apt to quietly leach CPU cycles while remaining hidden on a client PC or inside the datacenter, said Anton Ivanov, a researcher at Kaspersky Lab.
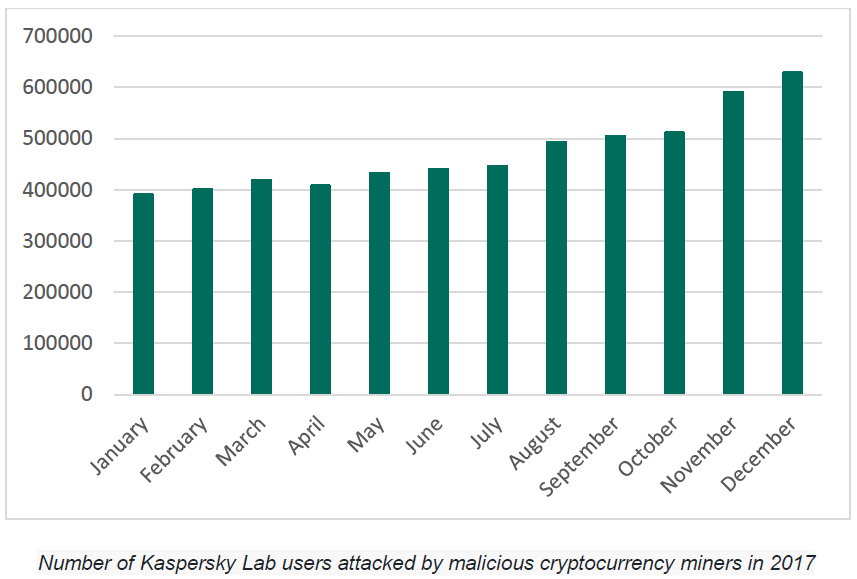
Researchers estimate 2.7 million users were attacked by malicious miners in 2017. That is up 50 percent from 2016 (1.87 million), according to the report that is planned to be presented later this week at Kaspersky’s annual Security Analyst Summit.
Individuals and businesses are becoming cryptojacking “victims as a result of adware, cracked games and pirated software used by cybercriminals to secretly infect their PCs,” researcher authors note. “Another approach used was web mining through a special (JavaScript) code located in an infected web page. The most widely used web miner was Coinhive, discovered on many popular websites,” researchers said.
10,000-Strong Botnet Built For Cryptojacking
Identified only as Group One, this gang of cryptojackers profiled by Kaspersky commanded a botnet of about 10,000 machines ranging from consumer to corporate PCs and servers that were stretched across the globe. The only prerequisite for targeted systems, researchers said, is that they had unpatched vulnerabilities susceptible to exploits such as the EternalBlue.
“They are mining Monero and using their own custom cryptocurrency miners,” Ivanov said. “And for persistence, they are using sophisticated techniques such as process hollowing and manipulating Windows’ system Task Scheduler.”
Process Hollowing is when an attacker creates a process in a suspended state and later replaces the process image with one that the attacker wants to remain hidden. Kaspersky said, that this is the first time it has seen this technique used in mining attacks.
Abusing the Windows’ Task Scheduler is also a way to cloak malicious software on computers. In similar attacks using the Task Scheduler technique, mining software is cloaked on targeted computers by the attacker who gives malicious miner programs benign names of typical Windows start-up applications such as diskmngr.exe, taskmngr.exe and svchost.exe. The mining software is then set to launch each time a computer starts via modifications made to the computer’s Task Scheduler or auto-run registry keys.
Criminals Scout Out Victims Ahead of Attacks
The second group of cryptomining hackers differentiate themselves by going to great lengths to specifically target types of users with Monero miners.
An examination of the malware used by Group Two, by Kaspersky, revealed hard-coded information in the Power Shell scripts. They contained specific information pertaining to the endpoints targeted in the attacks. Researchers said this indicates prior access to the targeted networks.
“It’s clear the threat actors had conducted reconnaissance on victims to determine who to target and who not to target with miners within an organization,” Ivanov said. This helps to avoid planting cryptocurrency malware on a system administrator or security officer’s computers. “This type of person could easily detect something is wrong very quickly,” he said.
This group used a private mining pool, so it is impossible to understand how much Monero coins they have made. “As this miner targets huge organizations and uses sophisticated techniques, it makes us believe that we can compare it with WannaMine miner which earned $3 million,” Ivanov said.
For Sale: Miner
Criminal crypto miners behind Group Three are unique because they didn’t use the build kits they made, only sold them online. According to the Kaspersky report, the kits were based on a custom script that mined Monero advertised on the Dark Web and places such as private Telegram channels geared toward hackers.
The build kits offers a would-be cryptojacker full customization of the malicious mining software from designating what percentage of the CPU to tax to going dormant when the victim launches a process-intensive game, so as to avoid detection.
“These kits are built to exist in systems for a long time. For a regular user it will be very hard for them to realize that they got infected,” the researcher said.
In its report, researchers said once-dominant ransomware attacks are quickly being usurped by cryptocurrency malware attacks. “This is confirmed by our statistics, which show a steady growth of miners throughout the year,” the report stated.
“Ransomware hackers were using the same tricks when they were on the rise,” according to the report.