In a report released Thursday the Federal Bureau of Investigation and the US Department of Homeland Security implicated Russian hacking group Fancy Bear in attacks against several election-related targets.
According to the Joint Analysis Report, the hacking group Fancy Bear, believed to have ties to the Russian government, used a combination of techniques ranging from spear phishing, spoofed domains and malware to harvest credentials in order to gain access to accounts controlled by a political party.
Attacks against U.S. targets came in two waves starting in the summer of 2015 and as recently as November 2016, according to the report. The FBI-DHS implicates Russian intelligence services who allegedly initiated the attacks via Fancy Bear, also known as APT28 and Sofacy.
The 13-page report (PDF) said attackers “masqueraded as third parties, hiding behind false online personas designed to cause the victim to misattribute the source of the attack.” It said hackers aimed “to compromise and exploit networks and endpoints associated with the U.S. election, as well as a range of U.S. Government, political, and private sector entities.”
In June, researchers at Crowdstrike implicated Cozy Bear in hacks against the Democratic National Committee. Crowdstrike said Cozy Bear has also been behind attacks against the White House, State Department and Joint Chiefs of Staff, as well as numerous organizations in critical industries around the Western world, Central Asia and the Far East.
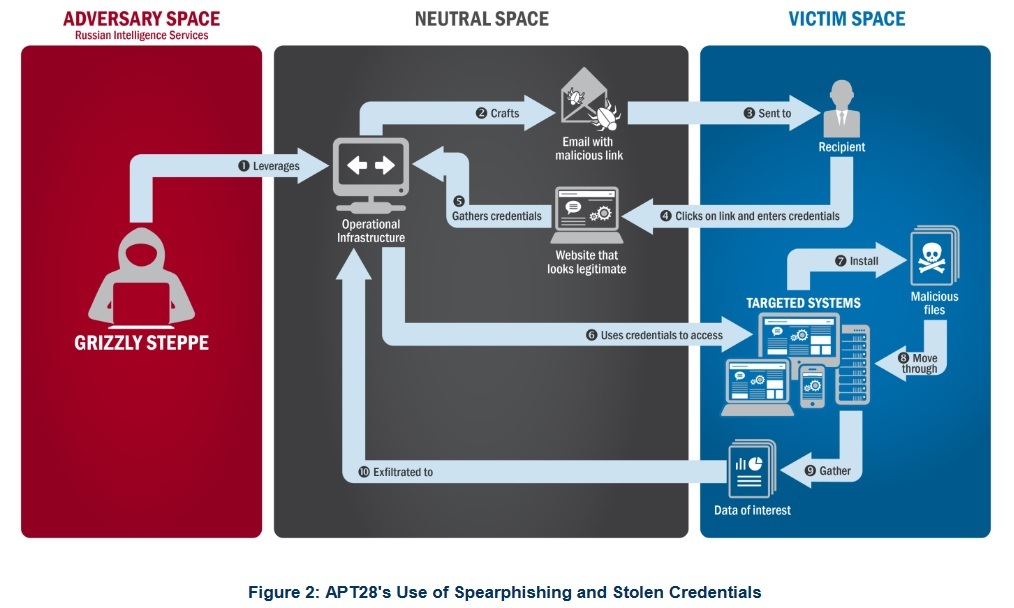
According to the FBI-DHS the malicious cyber activity, it designated as Grizzly Steppe, began in April 2015 and included a spear phishing campaign that targeted over 1,000 recipients.
“APT29 used legitimate domains, to include domains associated with U.S. organizations and educational institutions, to host malware and send spear phishing emails. In the course of that campaign, APT29 successfully compromised a U.S. political party,” according to the report.
The spear phishing campaign lured at least one victim to download a file that contained malware that “established persistence, escalated privileges, enumerated active directory accounts, and exfiltrated email from several accounts through encrypted connections back through operational infrastructure,” according to the report.
In the spring of 2016, attackers were again successful when they tricked a spear phishing recipient to change their password through a fake web domain controlled by the attackers. “Using the harvested credentials, APT28 was able to gain access and steal content, likely leading to the exfiltration of information from multiple senior party members.”
The report said information obtained from those attacks was released to the press and publicly disclosed. The report does not single out the DNC, however Crowdstrike and several security firms report that it was the prime target.
Spear phishing attacks continued even after the November 2016 election, according to the report. The FBI-DHS warned that further unconfirmed attacks may have occurred and might be related to the IP addresses and file hashes associated with attackers. Attacks may have targeted vulnerabilities such as injection flaws, cross-site scripting and server vulnerabilities, according to the FBI-DHS.
Mitigation and protection against present and future Fancy Bear attacks include backup, risk analysis and vulnerability scanning and patching.
The report has received mixed reviews. Congressman Jim Langevin, co-founder and co-chair of the Congressional Cybersecurity Caucus, praised the report in a statement: “By releasing formerly classified threat indicators, the Department of Homeland Security and FBI have exposed Russian hacking infrastructure.”
Noted cyber security expert Jonathan Zdziarski took to Twitter to publicly call the report overly simplistic.
Correction: an earlier version of this story incorrectly referred to Cozy Bear as being another name for Fancy Bear.