A new report from the SANS Institute warns that the push to digitize all health care records along with the emergence of HealthCare.gov and the general proliferation of electronic protected health information (ePHI) online will only exacerbate the security problems faced by those that store sensitive health care data. In other words, the report says, health care critical information assets are poorly protected and already compromised in many cases.
The “Health Care Cyberthreat Report” suggests that a compliance nightmare looms on the horizon and – more concerning yet – that the health care industry is now facing more exposure to attacks than ever before. The findings are particularly troublesome when you take into consideration that the health care industry has had a sordid history with IT security.
Sensitive health care information was never really all that secure to begin with. Health care data breaches were commonplace long before President Barack Obama signed the Patient Protection and Affordable Care Act into law. In fact, the SANS Institute opens its report with the stark and startling statistic that 94 percent of all healthcare organizations admit they have been the victim of a data breach at some point. That is an incredibly high number and, like all data breach statistics, it fails to account for those companies that have been breached and aren’t fessing up to it or just don’t know about it yet.
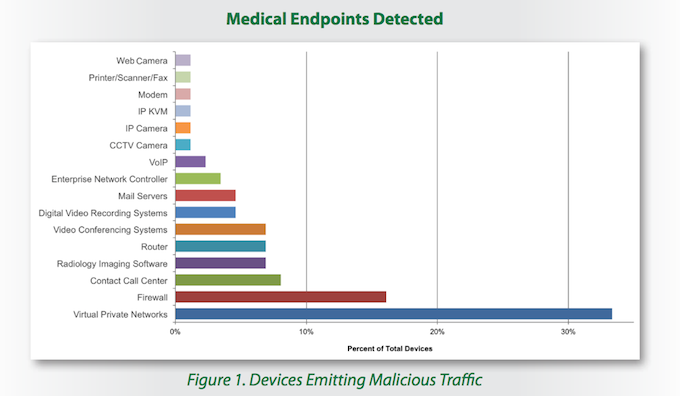
The report examined device-based and organizational sources of malicious traffic. Ironically, in terms of devices, most of the malicious traffic either passed through or was transmitted by security devices or applications. More specifically, virtual private networks enabled 33 percent of malicious traffic while 16 percent of malicious packets were sent by firewalls. Routers and enterprise network controllers together accounted for nine percent of such traffic. Other device types vulnerable to compromise included radiology imaging software, video conferencing systems, mail and VOIP servers, digital video systems, call contact software, and networked printers and fax machines.
“Today, almost every network attached device is shipped from its vendor in an insecure configuration with defaults that can be discovered easily through an Internet search,” said Barbara Filkins, a senior SANS analyst and healthcare specialist.
The report went on to note that network administrators are reliably changing easily guessable default credentials for router firewalls but they often overlook other network attached devices such as surveillance cameras, printers, and fax machines. As is so often the case, weak credentials and poorly configured security controls were among the leading causes for security incidents. Attackers can easily daisy-chain access from one poorly secured medical endpoint to more sensitive network devices.
The volume of Internet protocols examined within this targeted sample, the report claims, could be extrapolated to suggest that millions of health care organizations around the globe may already be exchanging malicious information.
“And theoretically,” the report says, “the effects of an ePHI compromise could potentially touch almost every person in the United States if the goal set by President Bush in 2004 that every American have an electronic health record by 2014 comes anywhere close to reality.”
Compliance, the report says, does not equal security. Existing best practices are not keeping up with attack techniques. Not only is patient data at risk, but so too is intellectual property, medical payment and billing information, and systems integrity. The findings showed that once a breach occurred, attackers regularly launched phishing and distributed denial of service attacks.
“This level of compromise and control could easily lead to a wide range of criminal activities that are currently not being detected,” said Filkins. “For example, hackers can engage in widespread theft of patient information that includes everything from medical conditions to social security numbers to home addresses, and they can even manipulate medical devices used to administer critical care.”
The costs incurred after breaches – said to include lawsuits, free credit monitoring services, stock fallout, and other expenses – are increasing as well. One Ponemon study from 2013 found that each exposed record could end up costing an organization some $233.
The report warns that many healthcare-related organizations – including one not named by SANS but described as a top three example of vulnerable medical organizations – believe their existing security controls, such as their firewall, are enough prevent compromise. In other words, organizations that have already been breached believe that they can not be compromised because of their existing security solutions.
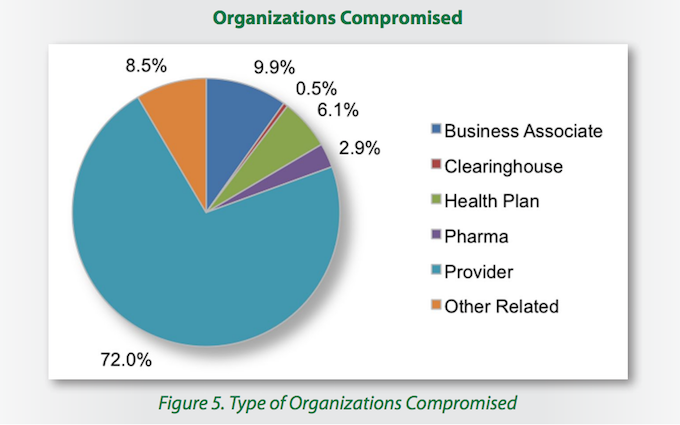
The report examined all sorts of players in the healthcare industry, from small providers to research and teaching hospitals to clearinghouses, health plans, and pharmaceutical companies. Among these, the lion’s share of malicious traffic originated from health care providers (72 percent). Health care business associates – essentially businesses providing services that support that industry – followed in a distant second, accounting for 9.9 percent of malicious packets. Health plans (6.1 percent), pharmaceutical companies (2.9 percent), and health care clearing houses (0.5 percent) closed out the list. Other related health care entities accounted for the remaining 8.5 percent of malicious traffic.
The report ultimately says that a completely new approach to security will be needed to address these problems. Considering the explosion of newly connected devices, organizations must know what is on their network and find ways to secure these devices. Part of this assessment necessarily includes replacing older, vulnerable software and networked equipment. The report also urges organizations to think like attackers. A fax machine may seem benign, but an attacker could potentially monitor it to siphon off patient prescription information. Surveillance systems can be remotely monitored to determine ways of physically accessing areas with valuable data. Furthermore, vulnerability assessments and software patch management must be an ongoing process.
The SANS report was based on data collected by the Norse threat intelligence network between September 2012 and October 2013. Norse is a health care-industry focused provider of security and anti-fraud products. Their threat intelligence infrastructure consisted of a global network of sensors and honeypots that processed and analyzed hundreds of terabytes of daily data during the sample period. According the report, collected data included 49,917 unique malicious events, 723 unique malicious source IP addresses, and 375 U.S.-based compromised health care-related organizations.