Security experts are warning some “Quit Smoking” and “20 Minute Fat Loss” ads online are delivering more than sales pitches. According to researchers at Zscaler, ads are redirecting browsers to malicious landing pages hosting the Terror exploit kit.
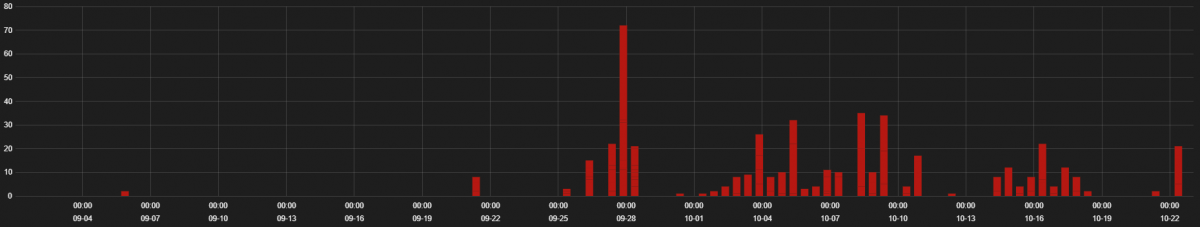
The campaigns have been sustained, with the initial blast spotted on Sept. 1 and lasting through Oct. 23.
“Terror EK activity has been low throughout the year but we are starting to see an uptick in the activity delivered via malvertising campaigns in past two months,” according to Rohit Hegde security researcher at Zscaler.
The Terror EK is distinguished for being a relatively new exploit kit, first identified earlier this year. In a separate Zscaler report, researchers said the EK borrows from other kits such as Sundown and Hunter with additional pieces borrowed from exploits built for the penetration testing software Metasploit.
“We’ve continued tracking the development of this kit since we first spotted it, and have watched developers transition to new domains with stolen identities, with traffic coming from the PopAds advertising network,” said Derek Gooley, Zscaler security researcher.
Over the past two months, a typical attack includes Terror EK redirects in the form of fake advertisements in the form of pop-up ads. “The initial JavaScript that gets served via a malicious advertisement page is obfuscated,” Hegde said.
“When a request is sent to the .php page, it responds with a HTTP 302 redirect to Terror EK Landing page,” researchers said. And that Terror EK landing page contains the VBScript and JavaScript exploits.
According to researchers, the Terror exploit kit is targeting two vulnerabilities CVE-2016-0189 and CVE-2014-6332. One of the bugs (CVE-2016-0189) is a scripting engine memory corruption vulnerability in Jscript (5.8) and VBScript (5.7, 5.8) engines used in Internet Explorer 9 through 11. The second (CVE-2014-6332) is a 2014 flaw called a Windows OLE automation array remote code execution vulnerability found in multiple versions of Windows from 7 to 8.1.
In addition to those two CVEs, researchers said, the landing page also calls to another URL, which tries to load three Flash exploits.
“The Terror EK actors have now started protecting their SWF files from decompilers using the DComSoft SWF Protector,” Zscaler explains. SWF Protector is software to protect SWF files and to make them secure.
As for the payload, researchers say the malware served in the most recent Terror EK malvertising chains belongs to the Smoke Loader downloader Trojan family.
“We observed that Smoke Loader payload with MD5 hash of “6ea344d0db80ab6e5cabdc9dcecd5ad4″ was served for an active Terror EK cycle earlier this week the most recent payload has MD5 hash of ‘b23745bcd2937b9cfaf6a60ca72d3d67’,” wrote researchers.
Smoke Loader is also known as the Backdoor.Win32.Mokes, a Backdoor.Win32.Mokes Backdoor.Win32.Mokes Trojan designed to give attackers remote control over an infected computer.