In an attempt to better evade detection, cybercriminals are increasingly configuring their command and control infrastructure in such a way that initial malware callbacks communicate with a server located in the same country as the newly infected machines.
This emerging trend is among the vast and varied findings of a FireEye report, “The Advanced Cyber Attack Landscape,” made public this morning. FireEye gathered the data in the report in an analysis of some 12 million messages communicated between various malware targeting enterprises and their command and control servers.
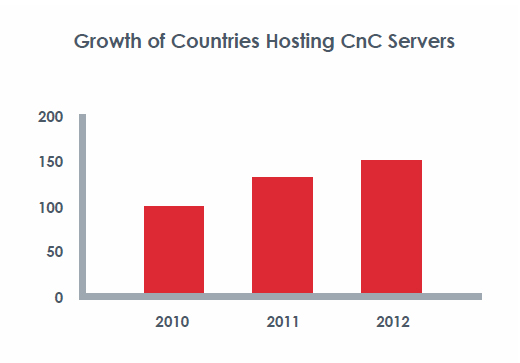
The creation and proliferation of malware is more global than ever, with C&C servers living in 184 countries. That’s a substantial 42 percent increase from 2010, when only 130 nations played host to C&C servers.
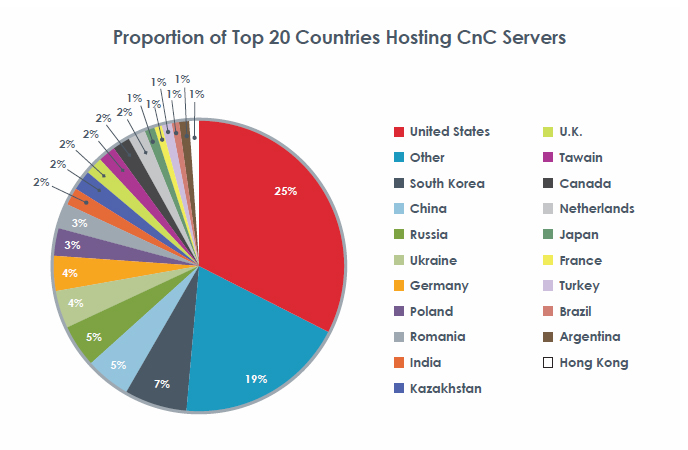
While the breadth and quantity of such servers is changing dramatically, much remains the same: parts of South and Eastern Asia and areas near Eastern Europe are still the international cybercrime hotspots. China, South Korea, India, Japan, and Hong Kong are believed to be responsible for 24 percent of cyberattacks, while Russia, Romania, Poland, Ukraine, Kazakhstan, and Latvia accounted for 22 percent. The caveat to FireEye’s claim that these regions are driving the majority of advanced attacks is that their analysis showed that 44 percent of C&C servers are actually located in North America. This, FireEye believes, is a statistical anomaly reflecting the new reality that attackers are evading detection more and more by distributing the C&C servers in close proximity to their targets.
In fact, North America’s 44 percent share of these servers and its more drastic 66 percent share of C&C servers responsible for advanced persistent threat-style attack campaigns is an indicator of something that has not changed according to FireEye: relatively speaking, the U.S. corporate landscape, particularly its wealth of high technology firms, is densely packed with valuable intellectual property, and therefore attackers continue targeting companies based there. However, forensic analysis of the tools used in these attacks and the communication tactics of the C&C infrastructure supporting them revealed that the vast majority of attacks – and as many as 89 percent of APT tools, most of them related to Gh0stRAT – originated in China where they were developed by Chinese hacker groups.
Another evolution is a move toward the use of social sites like Facebook and Twitter to communicate with infected machines. This tactic and another whereby attackers embed stolen content in commonly used JPG files are deployed by attackers in an attempt to make malicious traffic seem benign.
Other interesting findings highlighted by FireEye are that South Korean businesses, mostly because of that country’s incredibly developed Internet infrastructure, are witnessing the highest level of callbacks per organization. Their findings also suggest that Japan’s density of intellectual property may rival that of the U.S., considering that 87 percent of callbacks originate and stay in that country. Lastly, high exit-rate detection in both the U.K and Canada suggests to FireEye that attackers are generally unconcerned about being detected in those countries.