Researchers from MIT believe a new anonymity scheme they’ve devised dubbed Riffle could contend with Tor, claiming it’s every bit as secure as Tor, and bandwidth-efficient, to boot.
According to a paper, “Riffle: An Efficient Communication System With Strong Anonymity,” (.PDF) released this week, the system can guarantee anonymity among a large group of users, as long as there’s one honest server.
The scheme is based on a trio of concepts, what its creators call a hybrid verifiable shuffle technique, private information retrieval for bandwidth, and “computation-efficient anonymous communication.”
The paper was authored by Albert Kwon, a graduate student in electrical engineering and computer science at MIT, his advisor Srini Devadas, an Edwin Sibley Webster Professor of Electrical Engineering and Computer Science at MIT’s CSAIL, or Computer Science and Artificial Intelligence Laboratory, David Lazar, a graduate student in electrical engineering and computer science, and Bryan Ford SM ’02 PhD ’08, an associate professor of computer and communication sciences at the École Polytechnique Fédérale de Lausanne, in Lausanne, Switzerland. The quartet is slated to present their research at the Privacy Enhancing Technologies Symposium (PETS) in Germany, later this month.
At the crux of Riffle is a series of servers known as a mixnet that shuffles around the order of messages before it delivers them. By using verifiable shuffles, the system can shuffle the inputs but still be able to verify that an attacker in the mix didn’t tamper with the message. A shuffle takes an input list of ciphertexts and outputs a permuted and re-encrypted version of the input list, according to the paper.
“Assuming at least one of the mixes is honest, a verifiable mixnet is secure even with compromised mixes in the network: The honest mix alone shuffles inputs sufficiently to thwart traffic analysis attacks, and malicious mixes cannot tamper with messages without generating a bad proof,” the researchers write.
While utilizing verifiable shuffles can be an expensive and taxing process – it usually results in lower bandwidth – the researchers implemented a hybrid shuffle, one that’s used once and verified through authenticating ciphertexts, as part of Riffle. The method improves bandwidth and computation overhead, Kwon and company claim.
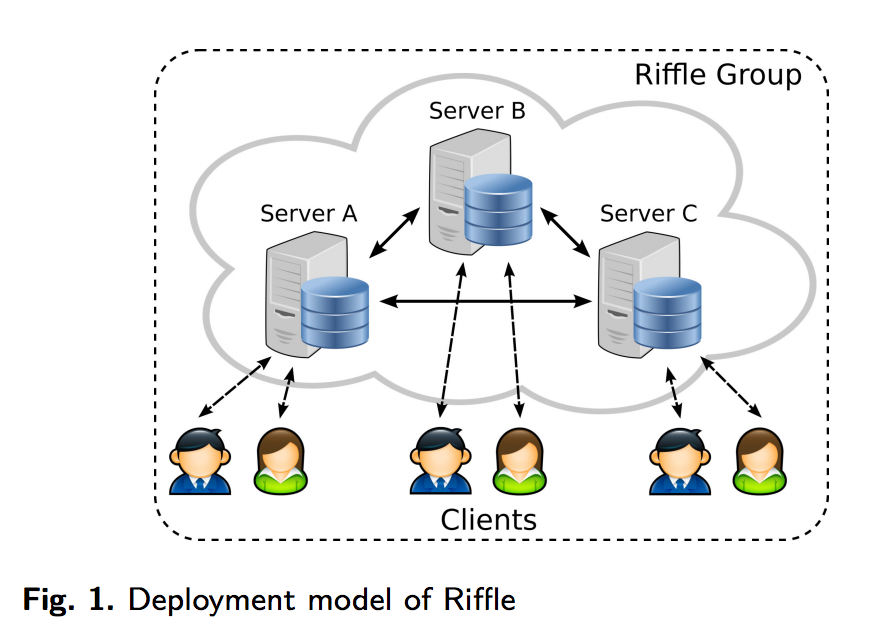 The system uses multi-server private information retrieval (PIR) to hide data it accesses and to minimize downstream bandwidth.
The system uses multi-server private information retrieval (PIR) to hide data it accesses and to minimize downstream bandwidth.
To demonstrate Riffle, the group developed two applications to work in tandem with a prototype of the system: an anonymous file sharing app akin to BitTorrent and an anonymous microblogging app.
Both were effective; the researchers found the file sharing app took one-tenth as much time as other systems to transfer a large file between anonymous users and can support up to 200 clients, with a bandwidth of around 100KB/s. The microblogging app, meanwhile, can handle over 100,000 users with less than 10 second latency.
Kwon and company acknowledge that while anonymity networks like Tor have gained popularity over the past few years, they’ve been plagued by on and off traffic analysis attacks. Kwon, Lazar, and Devadas were some of the researchers behind a paper published last summer, “Circuit Fingerprinting Attacks: Passive Deanonymization of Tor Hidden Services,” (.PDF) that identified a vulnerability in Tor’s design. The group found that an attacker could determine a hidden server’s location, or source of information reaching a Tor user, through traffic analysis.
The FBI, who are believed to have used a network investigative technique to de-anonymize Tor Browser users that visited a dark web child pornography site last year, have been mum on how exactly their exploit works. A federal judge excluded evidence from a trial in May involving the FBI and defendant Jay Michaud, a teacher who was charged with possession of child pornography, after the FBI refused to disclose details around the NIT.
The researchers claim that unlike Tor, Riffle can prevent traffic analysis by carrying out communication in rounds – in each round a client sends and receives a message – even if he or she didn’t wish to communicate that round.
Another group of researchers plan to present a new way to mitigate attacks that unmask Tor users at the same symposium in Germany later this month. The technique, Selfrando, works alongside mitigations already present in Tor Browser that are designed to protect against memory-corruption attacks.










