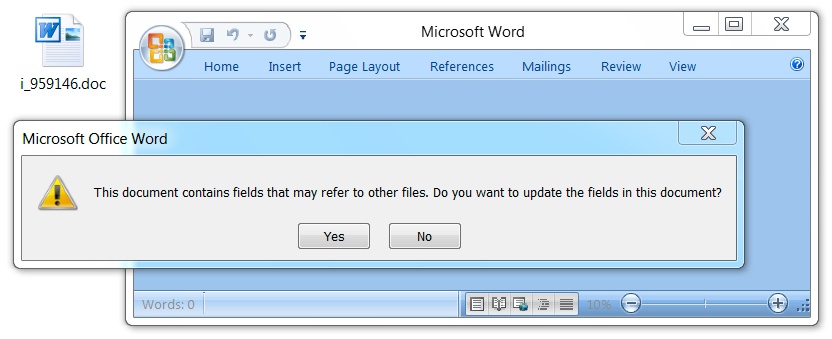
Microsoft may soon have to reflect on its stance that the use of an Office feature called DDE to execute code on compromised computers doesn’t merit a patch.
The SANS Internet Storm Center last night said the Necurs botnet has been spreading Locky ransomware using the DDE attack. Handler Brad Duncan said he had access to several dozen emails that are part of a spam campaign moving the ransomware. The emails contain one of three distinct Word document attachments spreading the malware and opting for the DDE technique rather than macros, which for more than a year have been the preferred means of downloading malware from a remote server.
“I think attackers are using DDE because it’s different. We’ve been seeing the same macro-based attacks for years now, so perhaps criminals are trying something different just to see if it works any better. In my opinion, DDE is probably a little less effective than using macros,” Duncan said. “We might see more DDE-based attacks in the coming weeks, but I predict that will taper off in the next few months.”
Like macros, DDE or Dynamic Data Exchange is a legitimate Office feature. It allows a user to pull data from one document and inject it into a second, such as a when a sales report is opened in Word, and an embedded field can dynamically update it with data from an Excel spreadsheet.
Last Friday, researchers at SensePost disclosed that a number of document-based attacks have been installing malware using DDE. They disclosed their findings to Microsoft in August and Microsoft said in late September that DDE was a feature and no further action would be taken.
SensePost said that a proof-of-concept exploit for this situation suppresses language in a dialog box that could ward off a user from starting an executable.
“The second prompt asks the user whether or not they want to execute the specified application, now this can be considered as a security warning since it asks the user to execute ‘cmd.exe’, however with proper syntax modification it can be hidden,” SensePost said.
Attacks using DDE are also likely to bypass antimalware and intrusion prevention scanners given that it’s likely a whitelisted feature.
“Apparently, DDE and macros are both legitimate features in Microsoft Office. Both have been used in malware attacks. In both cases, Office documents from malicious spam provide warnings to let a victim know what’s going on. To fix the issue, you’d have to remove the DDE entirely,” Duncan said. “If DDE is a functionality, then yes, I agree with Microsoft’s statement that it won’t be patched. However, many articles about DDE state it’s been superseded by OLE functionality. If so, why doesn’t Microsoft get rid of DDE entirely? Are there any legitimate DDE cases that require Microsoft to retain this backwards compatibility?”
Microsoft has indeed replaced DDE with the Object Linking and Embedding toolkit, but it has not discontinued support for DDE because Office still supports legacy documents that use the feature.
Duncan’s analysis of the Locky attacks show that the Word attachment using the DDE attack grabs the first stage of the attack, likely a downloader which then downloads the ransomware. Duncan described the traffic flow in a SANS ISC post:
“Traffic was a bit different than I’ve seen with recent attachments from the Necurs Botnet. The first HTTP request returned a base64 string that contained further URLs for the 1st-stage malware download. The second HTTP request returned the 1st-stage malware. Two follow-up HTTP POST requests came from the 1st-stage malware with the User-Agent string Windows-Update-Agent. Then came an HTTP POST request that returned the Locky ransomware binary. The Locky binary was encoded as it passed through the network, and it was decrypted on the local host. No callback traffic from the Locky binary was noted. I just saw some more HTTP POST requests from the 1st-stage malware.”
The Locky infection encrypts files stored on the local hard drive and demands 0.25 Bitcoin in exchange for the decryption key. SANS posted a number of indicators of compromise, including hashes of the attachments and malware, as well as IP addresses involved in the attacks.
“The best option I’ve found so far to disable DDE? For each office Application, under the Options menu, go to Advanced Options –> General, then make sure the “Update automatic links at open” box is un-checked,” Duncan said. “I found that prevents Word documents with DDE attacks from working. But in online forums, some people indicate this change doesn’t necessarily stay, and ‘Update automatic links at open’ may get re-checked again on its own.”