A new variant of the banking trojan Dridex is part of a sophisticated phishing attack targeting users of the cloud-based accounting firm Xero.
The global campaign is the latest in what security experts at Trustwave said is a wave of phishing attacks against Xero and other financial and accounting services such as Intuit.
As part of the campaign, attackers are spoofing messages that appear to be originating from Xero, an accounting company based in New Zealand that sells cloud-based accounting services to small and medium-sized businesses. Messages contain malicious links that attempt to trick recipients into downloading Zip archives containing a JavaScript file.
“On execution, this JavaScript downloads and launches banking malware on to the victim’s computer that steals their personal and private information and leaves them vulnerable to the mercy of their attackers,” said Trustwave researchers Fahim Abbasi and Rodel Mendrez who coauthored a report on the campaign published Wednesday.
The subject line of messages is typically “Xero Billing Notifications” with the originating email address displaying “xeronet.org” instead of the legit business “xero.com.” The domain was registered in China the same day the campaign started (Aug. 16). The message body attempts to spoof a legitimate inquiry from Xero, requesting the recipient to follow a set of malicious URLs. (see below)
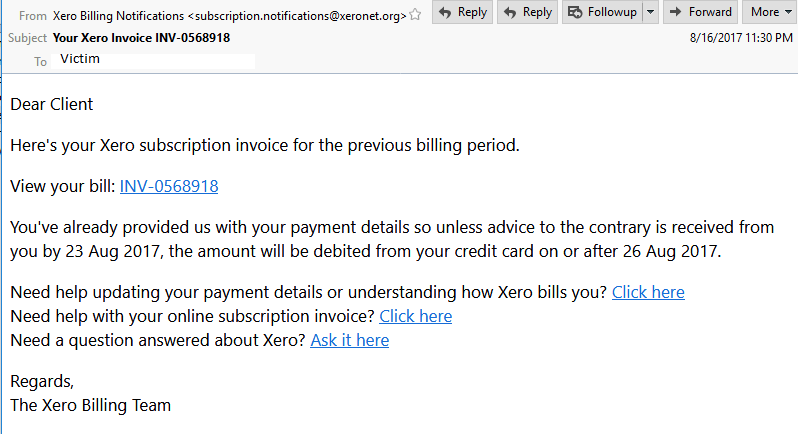 “Browsing to either URL has the same result, the URLs load JavaScript into the browser that forces a ZIP file download on to the victim’s computer,” researchers said. Unzipping Xero Invoice.zip extracts to Xero Invoice.js.
“Browsing to either URL has the same result, the URLs load JavaScript into the browser that forces a ZIP file download on to the victim’s computer,” researchers said. Unzipping Xero Invoice.zip extracts to Xero Invoice.js.
“On further analysis, it appears to be a generic JavaScript downloader and executer, that employs the Microsoft ActiveX object MSXML2.XMLHTTP to download the malware payload. This object is used to send an arbitrary HTTP request, receive the response, and have the Microsoft XML Document Object Model (DOM) parse that response,” researchers wrote.
The malware payload is identified as “Y739Ayh.exe,” a variant of the Dridex banking trojan. Trustwave call it a “sophisticated malware sample” capable of gathering system information such as installed applications and user account details. The malware also preforms several system wide policy settings and configuration changes for Internet Explorer through the registry. The malware also attempts to hook benign Windows processes such as “whoami.exe” and “net.exe”.
“When executed, Y739Ayh.exe performs a Process Hollowing technique to inject its malicious code into a legitimate process. It creates a suspended process of either of the two target processes: ‘svchost.exe’ or ‘spoolsv.exe’, using the API CreateProcessInternalW(),” researchers wrote. After the malicious code is written the main executable (Y739Ayh.exe) is then deleted.
“The malware probes the infected system by gathering computer name, system information as well as privilege information and integrity level. It uses built in Windows commands such as ‘whoami.exe /all’ and ‘net.exe view’ and then saves the result to a .tmp file dropped in Windows %Temp% folder which is later ex-filtrated,” according to researchers.
Information is stored as XML format and is then encrypted and exfiltrated to a control server using several different nonstandard ports using encrypted SSL channels.
“Dridex is designed to steal banking and personal information by injecting itself into web browsers such as Firefox, Chrome and Internet Explorer. It monitors browsing activity and steals sensitive information for target online banks listed in its configuration file,” Trustwave wrote.
The number of Dridex banking malware campaigns has fluctuated over the past year. In January, Dridex campaigns were on the upswing after an extended six-month hiatus. According to security firm Flashpoint, the Trojan began targeting large financial institutions in the U.K with a new technique that can bypass Windows User Account Control (UAC).
In February, researchers with IBM X-Force identified the new Dridex v4 sample sporting a new injection method for evading detection based on the technique known as AtomBombing. In April, Microsoft patched a zero-day vulnerability that was being used to spread the Dridex banking Trojan.
In each of the cases campaigns focused on banks and large financial institutions in the U.K.
Attacks targeting Xero customers follow a string of related campaigns targeting customers of online financial software services companies. In many cases, phishing emails used Microsoft SharePoint for hosting malicious URLs – as the Xero campaign did.
“Our research suggests that based on matching whois info, the cybercriminals behind this fresh wave of phishing attacks have been active in the past with similar campaigns using domains,” researchers said. Those similar campaigns began on Aug. 20 and included links to domains: xeroaccounting[.]org , intuito[.]biz, quickbooks-support[.]biz, financialaccountant[.]info, myobaustralia[.]org, australiangovernments[.]com, btconnect[.]biz and drvenergy[.]com.
“Such attacks have emerged as a recent trend on the attack landscape that exploit the trust that people associate with specific brands. As a mitigation measure, customers should avoid opening any email messages that appear suspicious, especially avoid opening any unknown downloaded files,” wrote Abbasi and Mendrez.










