Security researchers warn that a bogus Flash Player app aimed at Android mobile devices has surfaced and is luring victims to download and install banking malware that steals credit card information and can defeat two-factor identification schemes.
Wells Fargo, Discovery Financial and Chase customers, along with services such as Skype, Snapchat and Facebook are targeted in these attacks. Fortinet researchers said Tuesday the phony Flash Player was spotted Oct. 21. While it is not available via the Google Play app store, it’s unclear how it’s being distributed.
“This banking malware can steal login credentials from 94 different mobile banking apps. Due to its ability to intercept SMS communications, the malware is also able to bypass SMS-based two-factor authentication,” said security analyst Kai Lu at Fortinet.
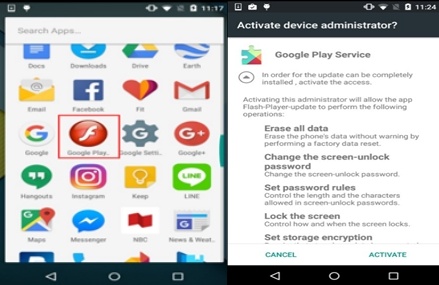
According to Fortinet, the malware is spreading in the United States, Germany, France, Australia, Turkey, Poland and Austria. If installed, it creates an icon on the Android device’s application launcher screen. According to Lu, when a user launches the bogus Flash Player, “the user is tricked into granting device administrator rights to the app through a fake Google Play Service” (below). Attackers are able to con users into activating the malware via a bogus Google Play Service screen that is actually a screen overlay.
If the user decides to cancel the download, the window closes only to reappear again. The only way to make the overlay go away is to choose “activate” from the menu choices. Doing so grants full device administrator rights to the malware. Next, the Flash Player icon is then hidden and the malware remains active in the background of the device, Fortinet said.
Once given administrative rights, the app can’t easily be uninstalled from the device, Lu writes. Worse, the malware has been given permission to send and receive text messages. This access, Lu points out, is what enables the attacker to bypass may two-factor authentication systems.
“After the malware is installed it collects information about the device, sends it to its C&C server, and waits for the server to respond with new commands to carry out,” Lu writes. Permissions granted to attackers controlling the malware include the ability to compose, edit, read, send and receive text messages to any number – premium or otherwise. Other permissions include modifying content on the phone, changing Wi-Fi connectivity settings, preventing the phone from going into sleep mode and the ability to reset the device to its factory settings.
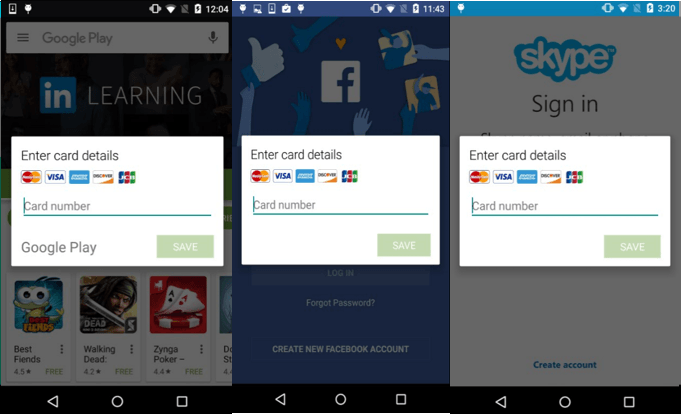
When a targeted banking, communication or social media app is launched by a user, the malware displays a screen overlay above the app (below). This action forces a victim to interact with the malware, because users are unable to use the desired app until entering credit card data.
Upon further inspection of the malware, the attackers prompt victims to input their credit card number and are able to verify valid credit cards via communication with the command and control server.
“This malware implements multiple malicious functionalities into a single app and takes full advantage of a successful infection. The attacker can control the list of legitimate apps to be targeted via C&C commands, and is also able to send and intercept SMS messages, upload SMS messages to its C&C server, reset the device to factory settings,” Lu wrote.
Removal of the malware is possible by disabling the administrator rights of the bogus Flash Player through Settings->Security->Devices Administrators->Google Play Service->Deactivate and uninstall “Flash Player.”
In some scenarios, because the malware repeatedly creates a screen overlay to request device administrator rights, “users will have to uninstall the malware via the Android Debug Bridge (ADB) by using the command ‘adb uninstall [packagename]’,” according to Lu.
Occurrences of overlay malware experienced a sharp uptick earlier this year, according to an April report by security researchers at IBM’s X-Force. Interest in overlay malware began to rise, according to X-Force, after the GM Bot malware code was leaked online in February. Since then, hackers reworked the leaked code and relaunched a new GM Bot variant pricing it at a much higher $15,000, compared to an average price of $5,000 for GM Bot six months ago.
In its April report, X-Force reported that the price hike sparked a pricing war among peddlers of similar overlay malware that also targeted Android devices. Pricing for these range from $3,000 to $6,000 and also includes malware-as-a-service options.