Researchers have observed ransomware so sophisticated over the last few months that we’ve seen a variant tease researchers with strings of hidden code and another composed entirely of JavaScript. But not every attacker is technically proficient; researchers are suggesting the ones behind a new strain of ransomware may just be plain lazy.
The ransomware Ranscam simply deletes users’ files, even if the victim chooses to pay, researchers at Cisco’s Talos Security Intelligence and Research Group claim, no encryption needed.
Like the ransomware’s name implies, Ranscam is just that: a ‘scam.’
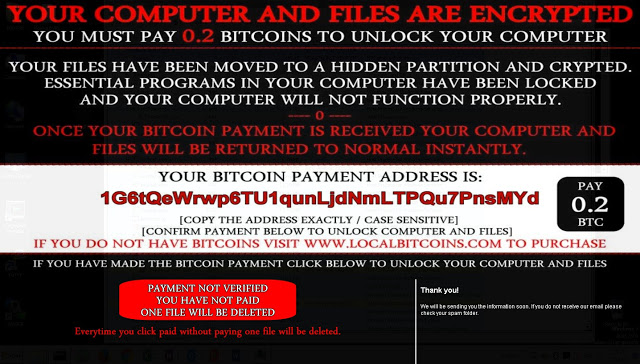
According to two researchers with the group, Edmund Brumaghin and Warren Mercer, who wrote about it on Monday, after a user’s machine is infected, Ranscam starts out like any other type of ransomware. Victims are encouraged to pay 0.2 BTC ($130 US) to unlock their files, which Ranscam claims have been moved to a hidden partition and encrypted.
“Once your Bitcoin payment is received your computer and files will be returned to normal instantly,” the ransom note claims.
Once users click a verification button claiming they’ve paid, the note changes and the button morphs into a “Payment not verified” button. It threatens to delete one file every time the user clicks the button without paying. In reality the button does nothing. The malware makes two HTTP GET requests to bring up a PNG image but it’s too late: the users’ files have already been deleted. To make matters worse the files aren’t recoverable, researchers claim. Since they were never encrypted in the first place, there’s no way to decrypt them.
Researchers claim the malware works as follows: a .NET executable calls on a batch file which multiplies and populates throughout the victim’s file system. From there, a script deletes a slew of important files: the core Windows .EXE responsible for System restores, shadow copies, and registry keys associated with booting the machine into Safe Mode.
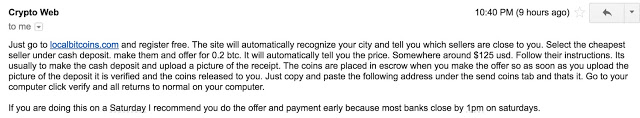
Brumaghin and Mercer were able to communicate with the attacker behind the ransomware – albeit it briefly – to discuss a payout. The exchange was polite – and demonstrated to what extent attackers are willing to go in order to receive a ransom:
It’s assumed the attackers behind Ranscam are more of a fly by night crew than dedicated operation, however. Researchers claim there haven’t been any transactions associated with the Bitcoin wallet they listed since June 29th. Furthermore, the ransomware has yet to been incorporated into any large-scale email campaigns, suggesting at least for the moment, the attacker behind it are novices and the scope of Ranscam remains small.
“Ranscam shows the desire of adversaries to enter the ransomware/scareware arena,” the researchers write, “They do not need to use novel attacks or even fully functional ransomware, as seen here, this appears to be an amateur malware author and is not a sophisticated campaign.”
Deleting files has become a cruel but common trait of ransomware. Researchers came up with a clever trick to circumvent Jigsaw infections this week. The ransomware frightens users into paying by deleting one file after the first hour, two after the second, and so on. Victims who restart their computer are penalized by one thousand deleted files.