Remote workers are being warned of a new phishing campaign targeting their Skype passwords.
The phishing emails look “eerily similar” to a legitimate Skype notification alert, according to a report released by Cofense on Thursday. Emails indicate users have 13 pending Skype notifications that can be checked by clicking a “Review” button.

“It is not uncommon to receive emails about pending notifications for various services,” researchers wrote. “The threat actor anticipates users will recognize this as just that, so they take action to view the notifications. Curiosity and the sense of urgency entice many users to click the ‘Review’ button without recognizing the obvious signs of a phishing attack.”
Those red flags are apparent upon closer inspection. The sender address, which spoofs a convincing Skype phone number and email address in the sender address, appears legitimate at first glance. But the real email address – an external, compromised account – can be found in the return-path (displayed as “sent from”).
Upon clicking “Review,” users are redirected through an app.link (hxxps://jhqvy[.]app[.]link/VAMhgP3Mi5) and finally to the end landing page (hxxps://skype-online0345[.]web[.]app).
The .app top level domain, used for this phishing landing page, is backed by Google to help app developers securely share their apps. It adds an air of further legitimacy to the phishing attack, researchers said.
“A benefit of this top-level domain is that it requires HTTPS to connect to it, adding security on both the user’s and developer’s end, which is great…but not in this case,” said researchers. “The inclusion of HTTPS means the addition of a lock to the address bar, which most users have been trained to trust. Because this phishing site is being hosted via Google’s .app TLD it displays this trusted icon.”
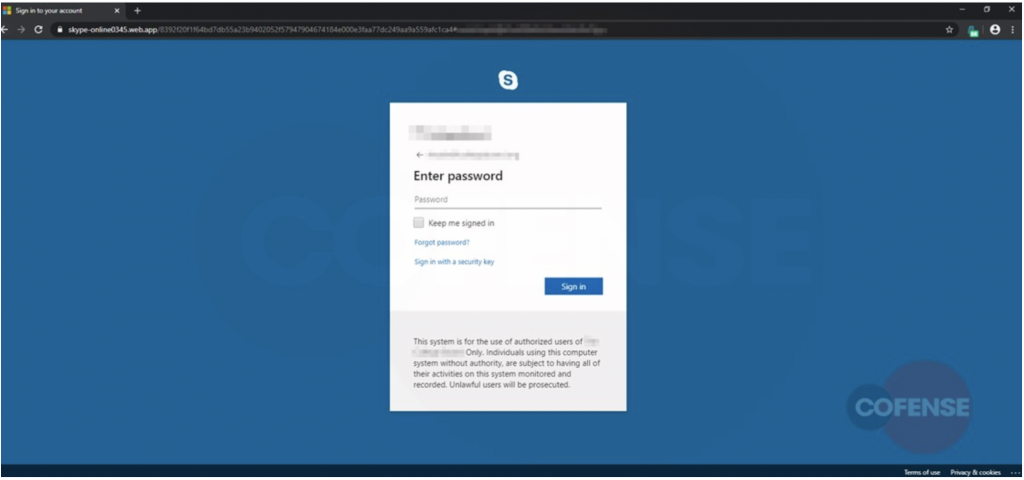
The webpage impersonates a legitimate Skype login page, asking for victims’ Skype credentials. The threat actors have done their research – they’ve added recipients’ company logos to the login box, as well as a disclaimer at the bottom warning that the page is for “authorized use” of that company’s users only.
The username is also auto-filled (due to the URL containing the base64 of the target email address) – another trick that leaves little room for doubt on the victims’ side.
“The only thing left for the user to do is to enter his or her password, which then falls into the hands of the threat actor,” said researchers.
The campaign is one of many looking to leverage the wave of remote workers who, in the midst of the coronavirus pandemic have come to rely on online conferencing tools like Webex (as well as Zoom and other platforms). With this upward spike in online meetings, compromised Skype credentials could be sold on underground forums, or used to log into accounts where sensitive files and data are shared (among other malicious activities).
Earlier in April, a phishing campaign was unearthed reeling in victims with a recycled Cisco security advisory that warns of a critical vulnerability. The campaign urges victims to “update,” only to steal their credentials for Cisco’s Webex web conferencing platform instead.
Researchers warn users to stay on the lookout for bad actors spoofing web conferencing and virtual collaboration apps. In general, attackers are taking advantage of the panic around the coronavirus with phishing emails around financial relief, promises of a cure and symptom information details.
“With so many people working from home, remote work software like Skype, Slack, Zoom, and WebEx are starting to become popular themes of phishing lures,” said Cofense researchers.
Worried about your cloud security in the work-from-home era? On April 23 at 2 p.m. ET, join DivvyCloud and Threatpost for a FREE webinar, A Practical Guide to Securing the Cloud in the Face of Crisis. Get exclusive research insights and critical, advanced takeaways on how to avoid cloud disruption and chaos in the face of COVID-19 – and during all times of crisis. Please register here for this sponsored webinar.