A massive mobile espionage campaign has been collecting troves of sensitive personal information since 2012, according to a new report from the Electronic Frontier Foundation and security firm Lookout.
Dubbed Dark Caracal, the advanced persistent threat (APT) campaign has managed to steal hundreds of gigabytes of data, including personal information and intellectual property, from more than 21 countries and thousands of victims, according to the 51-page report (PDF) released Thursday.
Dark Caracal is multi-platform and linked to 90 indicators of compromise (IOCs), among them 26 desktop malware IOCs, 11 Android malware IOCs and 60 domain/IP based IOCs, the report states.
The APT targeted governments, defense contractors, utilities and other “entities that a nation state might attack,” the report states. Dark Caracal has scooped up documents, audio recordings, photos, text messages and more from victims, it adds. Researchers said global operations of Dark Caracal were possibly linked to Lebanese intelligence services.
The investigation stemmed from the EFF’s previous Operation Manul report, which uncovered a similar espionage campaign aimed against journalists, dissidents and other critics of Kazakhstan President Nursultan Nazarbayev’s regime.
After an investigation, Lookout and EFF researchers concluded that the same infrastructure used for Operation Manul is behind Dark Caracal, and thus not linked to a single nation state. “Operation Manul clearly targeted persons of interest to Kazakhstan, while Dark Caracal has given no indication of an interest in these targets or their associates. This suggests that Dark Caracal either uses or manages the infrastructure found to be hosting a number of widespread, global cyber-espionage campaigns,” the report states.
In fact, it’s possible that Dark Caracal is currently executing six separate campaigns dating back as far as 2012, researchers wrote.
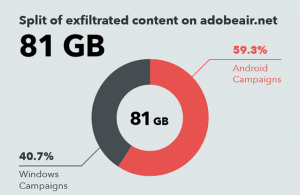
A break in the researchers’ investigation came in July 2017, when they discovered a command-and-control server linked to Dark Caracal that contained 81 GB of compromised data. About 60 percent of the information came from Android devices, with the remaining from Windows machines.
Dark Caracal attackers rely on three types of phishing messages, pushed through Facebook group posts and WhatsApp messages. Each are designed to lure mobile victims to a watering hole. It then distributes a malware called Pallas through trojanized applications such as WhatsApp, Signal and Tor related apps. Apart from their nefarious activities apps behave as they should with full functionality, the researchers found. Attackers gained access to private data through the permissions users granted when they installed applications.
On the desktop, Dark Caracal relies on malware embedded in executables and malicious attachments such as Zip archives, PDFs and other file types – also delivered though spear-phishing campaigns.
Dark Caracal runs on a “sprawling infrastructure” largely hosted on bulletproof hosting provider Shinjiru, according to the report. The infrastructure is used for storing stolen data and as a host for an Android app store stocked with malware infected apps, and other purposes.
Shinjiru also hosted Dark Caracal’s command-and-control server, which was operating with a major security hole, the researchers write:
“The adobeair[.]net C2 server had the Apache mod_status module enabled. This provides operators with information on server activity, performance, and a statistics page under /server-status that details connected clients and the server resources they are accessing. By programmatically monitoring this page, we were able to determine the source IPs of infected clients and admins logging into the console.”
As of September, the server was moved by adversaries to a different host, with better security.
The fact that the infrastructure operators gravitated toward Windows and the XAMPP application server software rather than the much more common LAMP stack provided another clue, since it gave researchers a “unique fingerprint” to look for, the report notes.
Lookout and EFF traced a number of devices Dark Caracal used for testing and operations to a building that houses the Lebanese General Directorate of General Security (GDGS). “Based on the available evidence, it is likely that the GDGS is associated with or directly supporting the actors behind Dark Caracal,” they write.
But they also emphasize that the malware is also being used by other groups, an analysis that suggests Dark Caracal is a type of APT-for-hire, rather than tied to a single nation state.
Yet, despite Dark Caracal’s reach, its operators have exhibited a lack of sophistication and care at times, evidenced by the exposed command-and-control server.
“It was pretty easy to see that someone had quickly spun it up without implementing the property security controls,” said Michael Flossman, security research services lead at Lookout, in an interview.
There are a number of key takeaways about Dark Caracal for security professionals, according to Flossman. “One is overestimating the technical sophistication that actors need to have to be successful in this space,” he said. “The second is that we’re seeing increasingly a trend of hacker groups shifting to mobile devices. Make sure you have visibility and actually have a way of getting insights into what’s going on on these endpoints.”
Lookout focused on the mobile aspects of the research, while the EFF focused on desktop components while jointly sussing out Dark Caracal’s infrastructure.
There is a significant gap in Dark Caracal’s footprint, at least for now. “We haven’t seen any indication they have an iOS capability,” Flossman said. That’s more likely because of the geographic areas the attackers targeted, where Android is the dominant platform, he added. But it’s not unrealistic to expect Dark Caracal to place iOS devices in its sights down the line, Flossman said.











