TrickBot, the infamous info-stealing trojan, has been trying out a test module that accidentally pops up fraud alerts to victims.
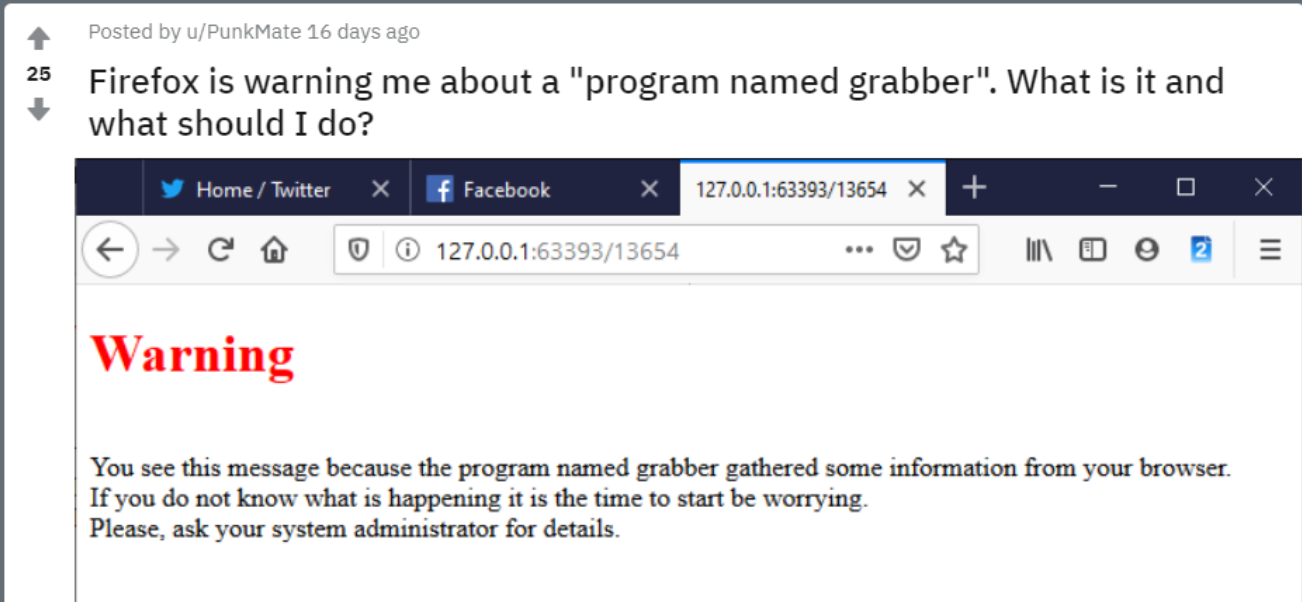
A sandboxed sample of the trojan, obtained by MalwareHunterTeam and analyzed by Advanced Intelligence’s Vitali Kremez, turns out to contain a new module, called “module 0.6.8,” that carries the file name “grabber.dll.” It works to log browser activity and steal passwords used in Google Chrome, Internet Explorer, Mozilla Firefox and Microsoft Edge, and it sniffs out browser cookies — just like other grabber modules used by TrickBot.
However, this one has an unintended side effect. It immediately alerts victims that they’ve been infected by opening the browser with the alert message. This is bad news for TrickBot operators, who use the malware to set up backdoors on target machines — presumably to maintain persistence and steal as much information as possible.
TrickBot is a rapidly evolving modular malware strain that has been around since 2016, starting life as a banking trojan. Over time, it has gradually extended its functions to include the ability to collect credentials from a victim’s emails, browsers and installed network apps. The malware has also evolved to add more modules and act as a delivery vehicle for other malware, including ransomware like Ryuk.
TrickBot has been busy of late adding backdoor functionality to its bag of tricks. In June, a new stealthy module that researchers call “BazarBackdoor” was added to TrickBot’s arsenal; and in January, researchers found the malware’s operators to be using “PowerTrick,” a backdoor that helped the malware conduct reconnaissance of targeted financial institutions and also fetch yet other backdoors.
According to Kremez’ analysis, the newly discovered grabber module uses several internal C++ code references, such as “grabchrome.cpp,” which align with the usual TrickBot grabber code patterns and functions. It appears that its triggering of browser alerts is a coding mistake, he said.
“Advanced Intelligence assesses with high confidence that this module was likely a test module deployed mistakenly, alerting on the malware activity during the testing phase,” Kremez wrote in a blog posting on Saturday.
Kremez noted that the latest sample offers a window into how TrickBot’s operators are able to develop new functions so quickly – i.e., perhaps by outsourcing the coding duties, and perhaps by hiring coders under the ruse of offering legitimate anti-malware development work.
“When running actual crime operations, there is no need to alert any user of the ‘fraud’ or ‘suspicious’ activity (especially via browser) during active infection as it might lead to loss of the bot in most of the cases,” he told Threatpost. “It leads us to believe that the developers might have been hiring coders for this module under the ruse of ethical hacking or pen-test operation. It allows them to recruit unsuspecting or social-engineered developers who might not be willing to code malware but could write it under the false pretense.”
Outsourcing the work isn’t a new idea, he added: “Since the widely disclosed FIN7 outsourcing operations, it is believed it has been a common tactic among top-tier crime groups to run crime as a business,” Kremez said.
He added that the sample is linked to the “chil48” distribution/campaign marker, which is one of several that researchers believe the group uses to track the spread of its campaigns. Kremez said that it appears that this malware strain has “been spread quite a bit, affecting thousands of victim globally.”
Posters on Reddit also began flagging the activity a couple of weeks ago, Bleeping Computer pointed out.
Interestingly, TrickBot operators may soon have yet another new module to deploy: The researcher also found a piece of code called “socksbot.dll,” which he said appears to act as a Socks5 proxy for the malware.
“Socksbot is a newer name for the backconnect Socks5 proxy leveraged for bank fraud and other malicious activity,” Kremez told Threatpost.
Overall, the code review of the module and its mistaken deployment has offered a larger window into one of the more sophisticated malware groups out there, he noted.
“TrickBot runs their operations as a focused and dedicated crime organization with multiple, talented coders and assets available to their disposal,” he said. “The module contains a highly verbose command prompt, showing the group focus on code quality.”
Anyone receiving the warnings should take their machine offline, Kremez recommended, and should reset both their passwords as well as any logged-in sessions, to prevent reuse of stolen cookies.
BEC and enterprise email fraud is surging, but DMARC can help – if it’s done right. On July 15 at 2 p.m. ET, join Valimail Global Technical Director Steve Whittle and Threatpost for a FREE webinar, “DMARC: 7 Common Business Email Mistakes.” This technical “best practices” session will cover constructing, configuring, and managing email authentication protocols to ensure your organization is protected. Click here to register for this Threatpost webinar, sponsored by Valimail.











