On Saturday an alert went out about a new Twitter worm.
Could this have been another XSS-Worm? Upon clicking the link users would see the following:
However that’s not all that happens. Covertly a connection is made to another server that will result in a malicious PDF being downloaded. This PDF contains a flurry of exploits.
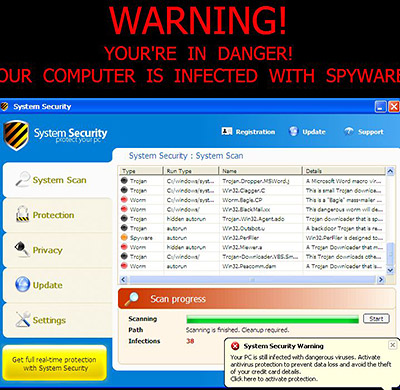
If exploitation is successful a file will be downloaded. Given the reports one would expect this to be the worm. However, it turned out to be yet another Fraudware installer. This time a fake program called “System Security” is being promoted.
During the research process I was not able to detect any worm-like component. There’s another very plausible explanation for the worm-like activity we’ve seen.
About a week ago there was a pretty high-profile phishing attack targeted at Twitter. It was only going to be a matter of time before we would see the abuse of the stolen accounts one way or the other.
Most likely the cyber criminals behind this attack simply used the stolen credentials of those phished accounts to tweet the messages. From my perspective this would also have been the more likely scenario rather than using a worm.
This attack is very significant. It would seem that at least one criminal group is now exploring the distribution of for-profit on Twitter. If the trends we’ve seen on other social platforms are any indicator for Twitter then we can only expect an increase in attacks.