Researchers disclosed a bevy of Bluetooth vulnerabilities Tuesday that threaten billions of devices from Android and Apple smartphones to millions of printers, smart TVs and IoT devices that use the short-range wireless protocol.
Worse, according to researchers at IoT security firm Armis that found the attack vector, the so-called “BlueBorne” attacks can jump from one nearby Bluetooth device to another wirelessly. It estimates that there are 5.3 billion devices at risk.
“If exploited, the vulnerabilities could enable an attacker to take over devices, spread malware, or establish a ‘man-in-the-middle’ to gain access to critical data and networks without user interaction,” according to the company. “The attack does not require the targeted device to be paired to the attacker’s device, or even to be set on discoverable mode… since the Bluetooth process has high privileges on all operating systems, exploiting it provides virtually full control over the device.”
As part of a coordinated disclosure, Armis said Google and Microsoft have already made patches available to their customers.
In a statement to Threatpost, Microsoft said: “Microsoft released security updates in July and customers who have Windows Update enabled and applied the security updates, are protected automatically. We updated to protect customers as soon as possible, but as a responsible industry partner, we withheld disclosure until other vendors could develop and release updates.”
Microsoft’s September Patch Tuesday disclosure lists one of the BlueBorne bugs (Bluetooth driver spoofing vulnerability – CVE-2017-8628) as part of its security patches for the month.
Apple iOS devices running the most recent version of the OS (10.x) are safe, Armis said.
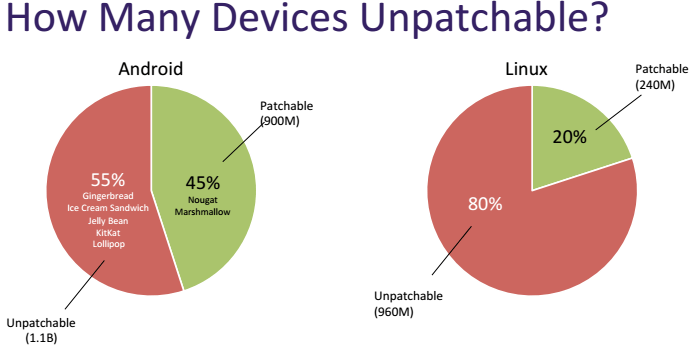
According to researcher, only 45 percent of Android phones (960 million) are patchable, leaving 1.1 billion active Android devices older than Marshmallow (6.x) vulnerable.
Also vulnerable are millions of smart Bluetooth devices running a version of Linux. Commercial and consumer-oriented versions of Linux (Tizen OS) are vulnerable to one of the BlueBorne bugs as are Linux devices running BlueZ and 3.3-rc1 (released in October 2011). All Windows computers since Windows Vista are affected, according to the researchers. Microsoft Windows Phones are not impacted.
“This set of capabilities are every hacker’s dream. BlueBorne can serve any malicious objective, such as cyber espionage, data theft, ransomware, and even creating large botnets out of IoT devices like the Mirai Botnet or mobile devices as with the recent WireX Botnet,” according to the company.
“This means almost every computer, mobile device, smart TV or other IoT device running on one of these operating systems is endangered by at least one of the eight vulnerabilities. This covers a significant portion of all connected devices globally,” researchers said.
In all, BlueBorne consists of eight related vulnerabilities, three of which are classified as critical. The vulnerabilities were found in the Bluetooth implementations in Android, Microsoft, Linux and iOS. They include:
*Linux kernel RCE vulnerability – CVE-2017-1000251
*Linux Bluetooth stack (BlueZ) information leak vulnerability – CVE-2017-1000250
*Android information leak vulnerability – CVE-2017-0785
*Android RCE vulnerabilities CVE-2017-0781 & CVE-2017-0782
*The Bluetooth Pineapple in Android – Logical Flaw CVE-2017-0783
*The Bluetooth Pineapple in Windows – Logical Flaw CVE-2017-8628
*Apple Low Energy Audio Protocol RCE vulnerability – CVE Pending
An attack scenario includes an adversary identifying Bluetooth devices nearby and using commonly tools to identify the MAC address of vulnerable Bluetooth devices.
“By probing the device, the attacker can determine which operating system his victim is using, and adjust his exploit accordingly. The attacker will then exploit a vulnerability in the implementation of the Bluetooth protocol in the relevant platform and gain the access he needs to act on his malicious objective,” researchers wrote.
At this stage the attacker can choose to create a Man-in-the-Middle attack and control the device’s communication, or take full control over the device and use it for a wide array of cybercriminal purposes, researchers stated.
In order to traverse from one Bluetooth device to the next, researchers say attackers would take advantage of a feature called Bluetooth Mesh, introduced with Bluetooth 5, which allows Bluetooth devices to interconnect and form a larger network with a more elaborate and dense structure.
“The automatic connectivity of Bluetooth, combined with the fact that nearly all devices have Bluetooth enabled by default, make these vulnerabilities all the more serious and pervasive,” they said. “Once a device is infected with malware, it can then easily broadcast the malware to other Bluetooth-enable devices in its vicinity, either inside an office or in more public locations.”
“These silent attacks are invisible to traditional security controls and procedures. Companies don’t monitor these types of device-to-device connections in their environment, so they can’t see these attacks or stop them,” said Yevgeny Dibrov, CEO of Armis. “The research illustrates the types of threats facing us in this new connected age.”
BlueBorne attack types boil down to two types. One, where an adversary goes undetected and targets a specific devices to execute code with the objective to gaining access corporate networks, systems, and data. The second scenario involves creating a Bluetooth Pineapple to sniff or redirect traffic.
“These vulnerabilities are the most serious Bluetooth vulnerabilities identified to date. Previously identified flaws found in Bluetooth were primarily at the protocol level. These new vulnerabilities are at the implementation level, bypassing the various authentication mechanisms, and enabling a complete takeover of the target device,” according to researchers.
(This story was updated Sept. 12, 1:30pm ET to include Microsoft’s comments and CVE details.)