Adobe has released patches for five critical vulnerabilities in Adobe Illustrator CC, its popular vector graphics editor tool, which if exploited could enable arbitrary code execution.
Overall Adobe patched nine vulnerabilities as part of its regularly-scheduled updates on Tuesday, including five critical ones in Adobe Illustrator CC, and four “important” and “moderate” flaws in Adobe Experience Manager (AEM), its platform for integrated online marketing and web analytics.
“Adobe is not aware of any exploits in the wild for any of the issues addressed in these updates,” according to Adobe’s security update.
The five critical flaws (CVE-2020-3710, CVE-2020-3711, CVE-2020-3712, CVE-2020-3713, CVE-2020-3714) open Illustrator CC up to a memory-corruption attack, which occurs when the contents of a memory location are modified due to programming errors, ultimately enabling attackers to execute arbitrary code.
The bugs affect Illustrator CC 2019 for Windows, versions 24.0 and earlier. Adobe users are urged to update to version 24.0.2, in a “priority 3” update. According to Adobe, a “priority 3” update “resolves vulnerabilities in a product that has historically not been a target for attackers. Adobe recommends administrators install the update at their discretion.”
Honggang Ren with Fortinet’s FortiGuard Labs was credited with discovering the flaws. Threatpost has reached out to Fortinet for further technical details.
Adobe also stomped out three “important” vulnerabilities and one “moderate” flaw in AEM. All four flaws could enable sensitive information disclosure. The important-severity flaws include two reflected cross-site scripting glitches (CVE-2019-16466 and CVE-2019-16467) that impact AEM 6.3, 6.4 and 6.5. These flaws enable an attacker to use a web app to send malicious code to a victim.
The other important-severity flaw is an expression language injection flaw (CVE-2019-16469) affecting AEM 6.5. Expression language injection occurs when attacker-controlled data is entered into an expression language interpreter.
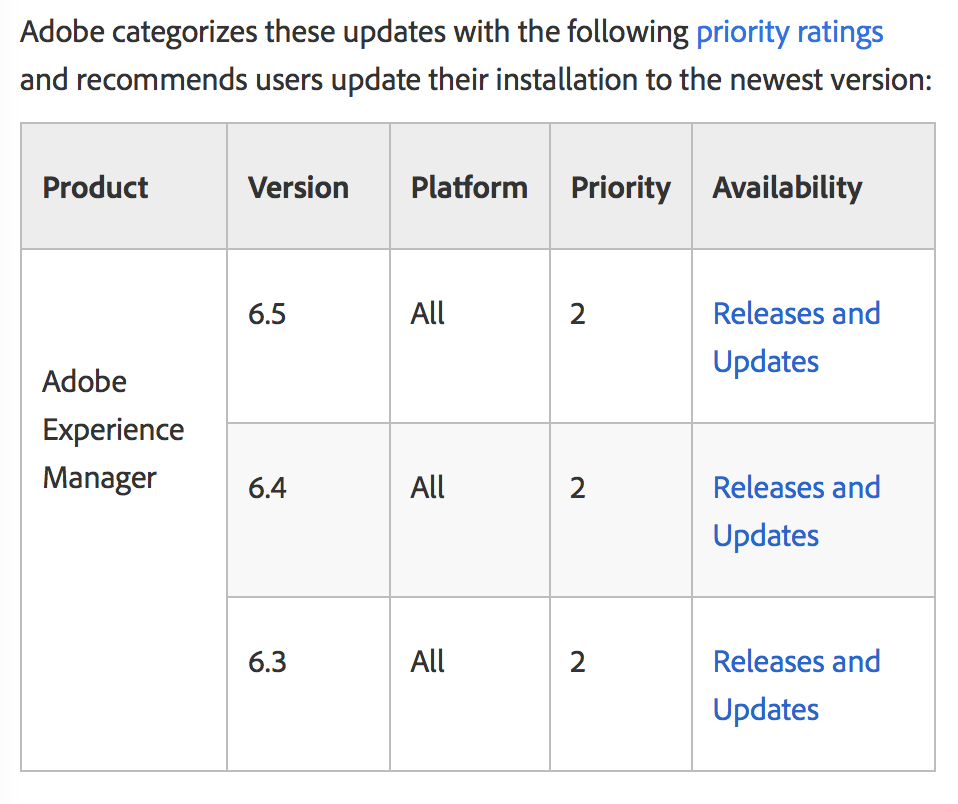
Finally, a moderate-severity user interface injection flaw (CVE-2019-16468) was also fixed, which impacts AEM 6.3, 6.4 and 6.5. The AEM flaws are a “priority 2” update, meaning they exist in “a product that has historically been at elevated risk.” AEM users can update to the fixed versions, listed below:
This month’s Adobe patches were few and far between, particularly after last month’s December update, when Adobe patched 25 CVEs overall across various products, including 17 critical vulnerabilities in Acrobat Reader, Photoshop and Brackets, which could lead to arbitrary code execution if exploited.
Concerned about mobile security? Check out our free Threatpost webinar, Top 8 Best Practices for Mobile App Security, on Jan. 22 at 2 p.m. ET. Poorly secured apps can lead to malware, data breaches and legal/regulatory trouble. Join our experts to discuss the secrets of building a secure mobile strategy, one app at a time. Click here to register.