Social media used as a cudgel for nation-states to sway opinion is a cybersecurity threat CISOs can’t ignore — and need to understand better and mitigate against.
That’s the message from Renée DiResta, research manager at the Stanford Internet Observatory, who said she is seeing a steady growth and maturing of damaging social-media campaigns by nation-states. The use of social media to sway opinion, sow division and hurt reputations is now part of a threat-actor’s playbook, according DiResta. During a keynote address at Black Hat on Thursday entitled “Hacking Public Opinion,” she said threat actors are fine-tuning these attacks.
Her message to the Black Hat community is that these types of attacks can just as easily be delivered as “reputation attacks” against businesses as they can against elections.
“Where does this threat land in your org chart? It falls to the CISO,” she said. “This is a cybersecurity issue…we need to do more red-teaming around social and think of it as a system and how attacks can impact operations.”
She noted that recent reputation attacks leveraging a social-media playbook have included the agrochemical firm Monstanto Company, petroleum producers involved in fracking, and business and organizations that have taken strong stances on social issues. Too often, DiResta said, there is a lack of ownership of the problem inside companies.
In her talk, DiResta walked virtual attendees through what constitutes a modern social-media influence campaign. First there is the creation of thousands of fake-personae accounts. Then there’s the development of content, which is seeded to social platforms. Next, dubious news sites generate plausible — yet bogus — articles that amplify a core message. If successful, the viral nature of the “news” piques the interest of mass-media news sites. They take the bait and report on the viral “news” as fact.
“As people in the infosec community, you need to identify the kill chain here and understand how to stop these attacks,” she said.
She outlined how both China and Russian nation-state actors have created influence operations to fit what she calls the “the information environment” of the day. The goal is to distract, persuade, entrench and divide.
“The secret with social isn’t ad buys and fake personas. It’s people becoming the unwitting participants in these influence campaigns by spreading their messages for them,” she said.
She drew a sharp distinction between China and Russian state actors. To wit: She pointed out that efforts to sway public opinion on the Hong Kong riots and attempts by China to deflect blame for the spread of the coronavirus were a failure.
While the number of fake social-media accounts created by China state actors was staggering, campaigns lacked the emotional component needed to spark organic human-to-human sharing of memes, stories or opinions. Stanford Internet Observatory estimated that 92 percent of the hundreds of thousands of fake accounts tied to China-influence campaigns had less than 10 followers, she said.
Russia-linked APT Fancy Bear on the other hand has been extremely successful in leveraging social platforms via a sophisticated mix of tactics that include hacking, leaking sensitive information and infiltrating impassioned affinity groups.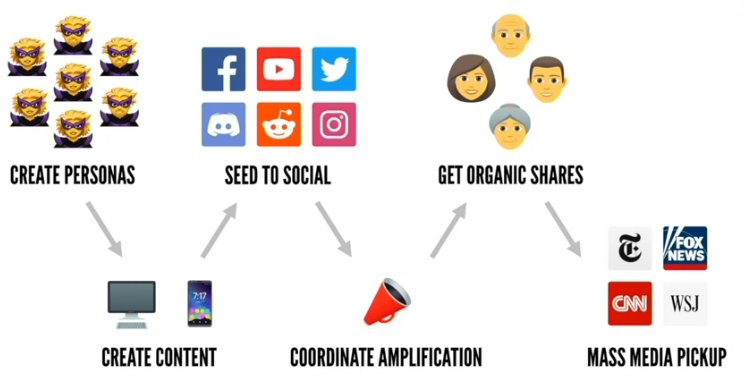 The hack-and-leak strategy begins with a compromise of a high-profile individual or organization. Damning information is then disclosed. Next, a social campaign amplifies the compromising information. Quasi-news sites report on the information leaked — and not the hack. Eventually, mainstream media picks up the report.
The hack-and-leak strategy begins with a compromise of a high-profile individual or organization. Damning information is then disclosed. Next, a social campaign amplifies the compromising information. Quasi-news sites report on the information leaked — and not the hack. Eventually, mainstream media picks up the report.
This virtuous circle of propaganda is accelerated by social platforms that are optimized for content-curation, meme-sharing and generating threaded discussions. Add to the mix the abuse by hackers of algorithms used by social platforms to maximize member engagement, DiResta said, and you have a “full-spectrum information operations.”
The antidote is heightened awareness of how these systems are abused by social platforms, consumers and victims. That includes CISOs and the cybersecurity research community, who should view these campaigns the same way malware or business-email compromises are reverse-engineered and mitigated against.
Complimentary Threatpost Webinar: Want to learn more about Confidential Computing and how it can supercharge your cloud security? This webinar “Cloud Security Audit: A Confidential Computing Roundtable” brings top cloud-security experts from Microsoft and Fortanix together to explore how Confidential Computing is a game changer for securing dynamic cloud data and preventing IP exposure. Join us Wednesday Aug. 12 at 2 p.m. ET for this FREE live webinar with Dr. David Thaler, software architect, Microsoft and Dr Richard Searle, security architect, Fortanix – both with the Confidential Computing Consortium. Register Now.











