Device manufacturers are combing through code again this week to determine whether their products are affected by a vulnerability tied to the SMB file-sharing protocol.
The vulnerability, (CVE-2017-7494) disclosed last Wednesday, affects versions of 3.5.0 onward of Samba, the free software re-implementation of the SMB/CIFS networking protocol. If exploited, the bug could allow authenticated attackers to execute arbitrary code remotely and take control of an affected system.
Samba Releases Security Updates https://t.co/BkdgitQrl8
— CISA Cyber (@CISACyber) May 25, 2017
Samba pushed a patch for versions 4.4 and higher a week ago but companies, many of which make products that use Samba, are continuing to learn about the vulnerability’s scope.
Cisco confirmed Tuesday that two of its products are affected by the bug and that it’s investigating which of its other products might be affected. Netgear said last week it was also looking into its products and that it had already pushed firmware updates for some it found were affected by the vulnerability.
So far, Cisco says it’s in the middle of developing fixes for two affected products, its Network Analysis Module and Video Surveillance Media Server. The company claims it’s reviewing whether the following 11 additional products are affected:
- Cisco Identity Services Engine (ISE)
- Cisco Small Business RV Series RV320 Dual Gigabit WAN VPN Router
- Cisco Common Services Platform Collector
- Cisco IP Interoperability and Collaboration System (IPICS)
- Cisco Expressway Series
- Cisco MXE 3500 Series Media Experience Engines
- Cisco TelePresence Video Communication Server (VCS)
- Cisco VDS Recorder
- Cisco VDS-TV Caching Nodes
- Cisco VDS-TV Streamer
- Cisco VDS-TV Vault
Conversely the company says three products, its Application and Content Networking System – ACNS, Web Security Appliance – WSA, and Digital Media Manager, are not vulnerable.
Netgear was one of the first companies to push a fix for affected products out the gate. It released firmware fixes for its ReadyNAS products running OS 6.x last week. A Netgear forum moderator said Friday the company plans to move to a newer version of Samba on OS 6 in the future but in the meantime has backported Samba’s fix.
The company also pushed new versions of RAIDar, the firmware ReadyNAS devices use, to mitigate the vulnerability on Tuesday. Users can download the Legacy Sparc, x86, and ARM firmware for the network storage devices via the company’s support page.
The company says it is also investigating whether ReadyNAS products running 4.1, 4.2, 5.x, and 6.x, its ReadyDATA products, and a handful of routers are vulnerable:
- C7100V
- C6220
- C3700
- N450/CG3000Dv2
- R7000P
- R6900P
- C3000
- C6250
- C6300
- C7000
The company is recommending users concerned about the vulnerability disable write access to drives shared via SMB or simply remove USB storage devices connected to their router or gateway.
“The potential for remote code execution remains if you do not complete all recommended steps,” Netgear warns in its advisory.
Synology, another company that manufactures NAS devices, released updates (6.1.1-4 and DSM 6.0.3-1) for two affected products – DiskStation Manager (DSM) 6.1 and DSM 6.0 – last week. The company, headquartered in Taipei, is reportedly working on a fix for another affected product, its web-based operating system Synology Router Manager (SRM) 1.1. That fix should arrive this week, Synology says.
The Samba vulnerability initially drew comparisons to WannaCry, the ransomware worm responsible for 200,000 infections across 150 countries earlier this month. Both vulnerabilities rely on leveraging a vulnerability in the SMB protocol. Samba is predominantly run on Linux and Unix machines however, making them the biggest target here.
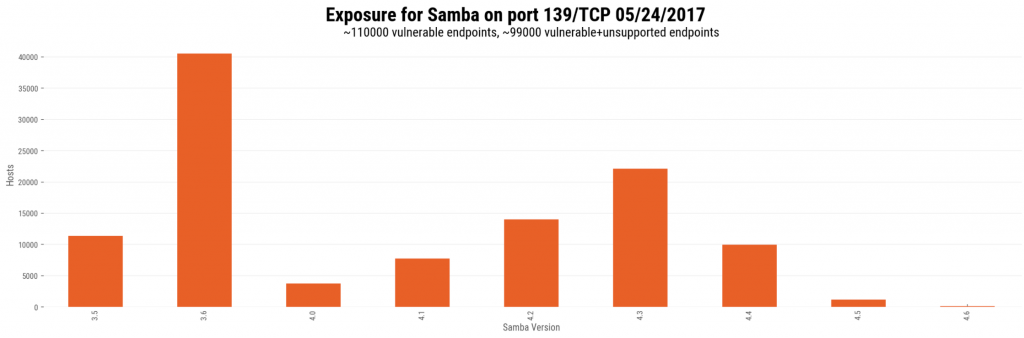
Researchers with Rapid7 said last week that saw more than 104,000 internet-exposed endpoints running vulnerable versions of Samba on port 445 and approximately 110,000 endpoints on port 139. According to the company, 91 percent of the port 139 endpoints were running older, unsupported versions of Samba, something that could make resolving the vulnerability tricky.
Since Samba’s patch is only for versions 4.4 and up, users running older versions, 3.5x to 4.4x, need to update to a supported version of the software in order to apply the patch.
The bug is seemingly the biggest to surface in Samba since last year’s Badlock vulnerability. That bug, hyped for weeks, ultimately fell short of expectations. Instead of allowing code execution—like last week’s bug, Badlock was merely a combination man-in-the-middle and denial-of-service bug that allowed attackers to elevate privileges or crash a Windows machine running Samba.