The Necurs botnet is driving a fresh spam campaign that uses Excel Web Query (.IQY) file attachments to skim under the antivirus radar. If successful, the attack ultimately delivers the remote access trojan (RAT) known as FlawedAmmyy.
This is the third wave in an offensive that started in late May. The emails, posing as internal company communications regarding an “unpaid invoice,” are part of one of the first prolific campaigns in the wild to use .IQY attachments, according to Barkly researchers.
Unlike full Excel spreadsheets, which are usually inspected by AV engines when they come in as email attachments, the comparatively diminutive .IQY files aren’t usually indexed by AV software. This is likely because they’ve never really been weaponized in the past, plus, they’re lightweight affairs from a size perspective, being simple, plaintext files.
As a result, this week’s campaign has had remarkably low detections, according to VirusTotal.
Researcher Derek Knight (@dvk01uk), who spotted the first campaign, pointed out that “These blow past all antiviruses because they have no malicious content.”
However, .IQY files are deceptive, because they act as downloaders. “They’re extremely simple (just a few lines of text), but also powerful,” said Barkly researchers, in an analysis this week. “The .IQY files used in these campaigns download a PowerShell script, which is launched via Excel and kicks off a chain of malicious downloads.”
When opened, the .IQY file launches via Excel (its default program) and attempts to pull data from the URL included inside. In the case of the Necurs spam, that data happens to be a malicious PowerShell script.
Barkly researchers added, “The ability of these files to open Excel and (if users choose to ignore warnings) download any data from the internet makes them extremely dangerous.”
The Payload and the Botnet
Built from leaked source code of the popular remote desktop software Ammyy Admin, FlawedAmmyy first drew attention to itself in March. Proofpoint researchers discovered at the time that the previously undocumented RAT had actually been used since the beginning of 2016.
It’s been used in two types of campaigns: highly targeted email attacks against the automotive industry, among others; and massive, multi-million message campaigns that Proofpoint researchers said appear to be associated with threat actor TA505, which has been active for the last four years.
FlawedAmmy offers the same bells and whistles as the legitimate version: complete access to victim machines. That allows them to steal files and credentials, hijack computers to send out more spam emails, and more.
Meanwhile, the choice of Necurs as a delivery mechanism makes for a wide attack surface. Over the past five years it has become the Scarface of spam, working its way up from nothing to sit atop a massive criminal enterprise.
Cisco Talos analysis shows it to be the world’s largest spambot, accounting for more than 90 percent of the daily spam seen by the firm. Its evaluation of Necurs traffic between August and November of last year detected more than 2.1 million spam messages, sent from almost 1.2 million distinct sending IP addresses, in over 200 countries and territories.
Mitigation
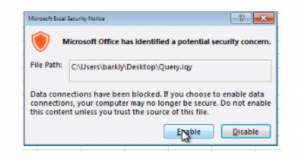
Barkly pointed out that as long as Microsoft Office is configured to block external content (which is the default), when Excel launches users will be presented with a warning prompt, and users must actively choose to enable the macros:
Even if a user clicks “yes,” another prompt shows up:
For IT admins that don’t want to leave protection to user awareness, Barkly suggests adjusting the firewall settings and email filtering to block .IQY files altogether unless they’re actively used in the business.
It’s also possible to instruct Windows to always open .IQY files in Notepad so they can be inspected by IT before they launch.
It’s wise to have a plan, given that these specific campaigns are likely not the end of criminals using .IQY files.
“The ease in which .IQY files can be created, combined with the ubiquity of Excel, could even put .IQY files roughly on par with macros in terms of potential for abuse,” Barkly researchers said. “The fact that they are being utilized in multiple Necurs campaigns means the genie is completely out of the bottle and more widespread abuse is likely on the way.”