The cybercrime network behind the GozNym malware, used to siphon $100 million out of its victims, has been dismantled in a massive international investigation, according to authorities.
Europol said on Thursday that they are charging 10 members of the GozNym criminal network with spreading the malware to businesses and stealing money from more than 41,000 victims.
“An unprecedented, international law enforcement operation has dismantled a complex, globally operating and organised cybercrime network,” Europol said in a Thursday statement. “The criminal network used GozNym malware in an attempt to steal an estimated $100 million from more than 41,000 victims, primarily businesses and their financial institutions.”
Since its discovery in 2016, the hybrid banking trojan has made waves, spreading into Europe and begun plaguing banking customers in Poland with redirection attacks. The banking trojan then reportedly started taking aim at banks in Germany and the U.S.
The 10 members charged – all from five different countries – allegedly used GozNym to infect victims’ computers and capture their online banking login credentials. They then used those credentials to fraudulently gain unauthorized access to victims’ online bank accounts, stole money from those accounts, and laundered the funds using U.S. and foreign beneficiary bank accounts.
Of the 10 members of the criminal gang charged, five remain on the run – including the developer of GozNym malware who oversaw its creation, development, management and leasing to other cybercriminals.
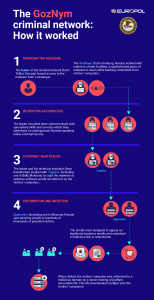 The other five, which are believed to be from Russia, Bulgaria, Ukraine and Moldova, participated in various aspects of the cybercrime ring. One member encrypted the GozNym malware to enable it to avoid detection by anti-virus tools and protective software on victims’ computers; others provided the network access to bank accounts that they controlled to receive stolen funds from victims’ online bank accounts.
The other five, which are believed to be from Russia, Bulgaria, Ukraine and Moldova, participated in various aspects of the cybercrime ring. One member encrypted the GozNym malware to enable it to avoid detection by anti-virus tools and protective software on victims’ computers; others provided the network access to bank accounts that they controlled to receive stolen funds from victims’ online bank accounts.
Also, “the leader of the GozNym criminal network, along with his technical assistant, are being prosecuted in Georgia by the Prosecutor’s Office of Georgia and the Ministry of Internal Affairs of Georgia,” said Europol.
Also of note, the administrator of the “Avalance” network who provided Bulletproof hosting services to the GozNym criminal network is also facing prosecution in Ukraine.
“The Avalanche network provided services to more than 200 cybercriminals, and hosted more than twenty different malware campaigns, including GozNym,” according to Europol. “The administrator’s apartment in Poltava, Ukraine, was searched in November 2016 during a German-led operation to dismantle the network’s servers and other infrastructure. Through the coordinated efforts being announced today, this alleged cybercriminal is now facing prosecution in Ukraine for his role in providing bulletproof hosting services to the GozNym criminal network.”
 The indictment gave a look inside the GozNym network. The network also peddled “cybercrime as a service,” advertising different criminal services – including money mules networks, crypters, spammers, coders, organizers, and technical support – on underground, Russian-speaking online criminal forums.
The indictment gave a look inside the GozNym network. The network also peddled “cybercrime as a service,” advertising different criminal services – including money mules networks, crypters, spammers, coders, organizers, and technical support – on underground, Russian-speaking online criminal forums.
The GozNym network was formed when varying individuals were recruited from the online forums by the unnamed GozNym leader, who controlled more than 41,000 victim computers infected with GozNym malware, Europol said.
GozNym is only the latest cybercrime network to be targeted by law enforcement. Earlier in January, law enforcement agencies took down a credentials marketplace (xDedic Marketplace) as well as continued action against former users of the Webstresser.org DDoS-for-hire site.
And, earlier in May, two Chinese nationals were charged in the massive 2015 data breach of health insurer Anthem that impacted more than 78 million people. Finally, in 2018, the Department of Justice arrested three alleged members of the FIN7 cybercrime group, accusing them of hacking more than 120 U.S.-based companies with the intent of stealing bank cards.
Want to know more about Identity Management and navigating the shift beyond passwords? Don’t miss our Threatpost webinar on May 29 at 2 p.m. ET. Join Threatpost editor Tom Spring and a panel of experts as they discuss how cloud, mobility and digital transformation are accelerating the adoption of new Identity Management solutions. Experts discuss the impact of millions of new digital devices (and things) requesting access to managed networks and the challenges that follow.











