The ransomware gang behind an attack on videogame developer CD Projekt Red may have made good on its promise to auction off the company’s data – including source code for Cyberpunk 2077 and an unreleased version of the Witcher 3.
Or it may not have.
The Twitter account @vxunderground, which bills itself as “the largest collection of malware source code, samples and papers on the internet,” put out a notice on Wednesday that the purported stolen data was being put up for sale on the well-known Russian-language underground forum “Exploit,” and it provided alleged screenshots.
“This is the source code to ‘Gwent’ card game,” according to the tweets. “Witcher 3, CyberPunk 2077, etc. is being auctioned today on EXPLOIT forums…The ransomware authors said they will not be auctioning data anywhere else – any other location other than EXPLOIT is fake.”
@vxunderground also said that the information had a starting bid of $1 million, but they whole cache could be bought outright for $7 million.
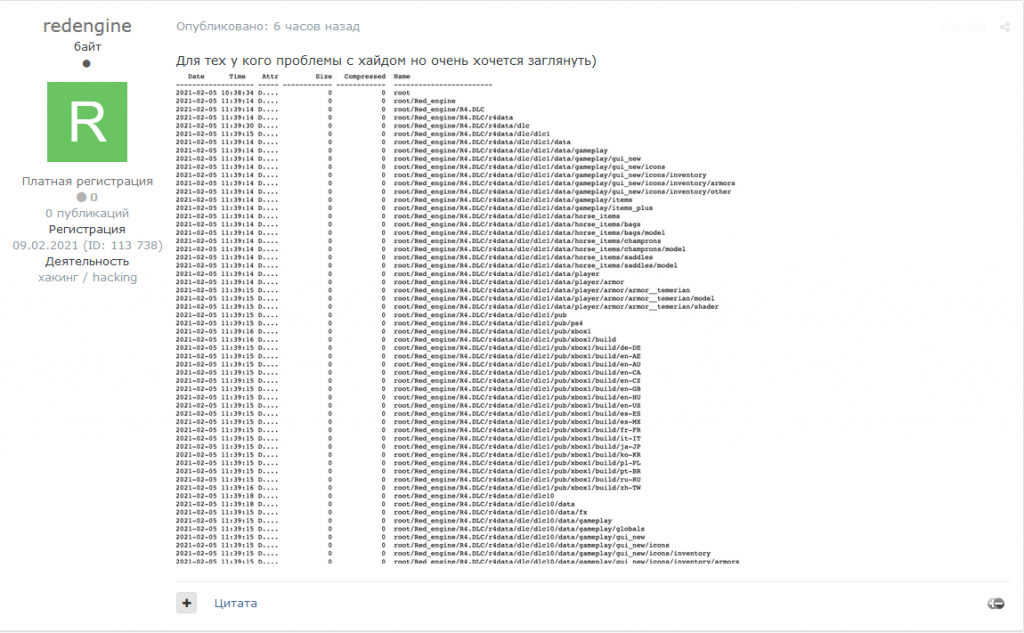
When asked to independently verify the claim, Austin Merritt, cyber-threat intelligence analyst at Digital Shadows, told Threatpost that the auction posting did indeed exist. An Exploit user named “redengine” created a thread in the auctions section of the site, entitled “Auction date for CD Projekt RED” when translated from the Russian.
“The user claimed to have full source codes for various games including Thronebreaker, Cyberpunk 2077, Witcher 3 and the undeclared Witcher 3 RTX (a version of Witcher with raytracing),” Merritt said. “The user also claimed to have dumps of internal documents and files related to CD Projekt RED ‘offenses.'”
As for cost and timing, Merritt said that the poster set the auction to start Thursday, Feb. 11 at 13:00 Moscow time (5 a.m. ET), and that bidders would be required to make a 0.1 BTC deposit (around $44,900 at press time) to enter.
“The user started the auction at $1 million, however, users have not yet expressed any interest in purchasing this information,” Merritt told Threatpost. “At the time of writing, there have been six replies to the original post. Users that have replied have largely questioned the legitimacy of the post, alleging that user ‘redengine’ does not have an established reputation on the forum.”
Thus, it’s unclear if what the user is offering is legitimate, or if the posting is from an opportunist trying to take advantage of the buzz around the stolen data that percolated up this week in media accounts.
Merritt gave Threatpost a screenshot of the alleged Gwent data files:
CD Projekt Red has not responded to a request for comment or verification.
CD Projekt Red Ransomware Strike
The Warsaw-based videogame company tweeted out a notice on Tuesday, warning of “a targeted cyberattack in which some of our systems have become compromised.”
The attackers – believed to be part of the “Hello Kitty” ransomware gang, as Threatpost previously reported — acknowledged that the ransomware itself would likely not be a problem for the company, which had backups in place to quickly remediate the attack. More concerningly, the attackers threated to dump troves of stolen company data online – including game source code.
“We have encrypted all of your servers, but we understand that you can most likely recover from backups,” according to the ransom note shared by CD Projekt Red. However, “source codes will be sold or leaked online, and your documents will be sent to our contacts in gaming journalism.”
It went on to say that not paying up would have an impact on the company’s public image, stock price and investor confidence (CD Projekt Red is traded in over-the-counter markets). The attackers also claimed that the information will expose how terribly the company is run.
Release of the source code would allow fans to develop game hacks and perform all kinds of “modding” (i.e., development of custom features) and jailbreaks; and would be a gift to competitors.
Threatpost WEBINAR: Is your small- to medium-sized business an easy mark for attackers? Save your spot for “15 Cybersecurity Gaffes SMBs Make,” a FREE Threatpost webinar on Feb. 24 at 2 p.m. ET. Cybercriminals count on you making these mistakes, but our experts will help you lock down your small- to mid-sized business like it was a Fortune 100. Register NOW for this LIVE webinar on Wed., Feb. 24.











