More than half of all internet of things (IoT) devices are vulnerable to medium- or high-severity attacks, meaning that enterprises are sitting on a “ticking IoT time bomb,” according to Palo Alto Networks Unit 42 research team.
In new research released Tuesday, researchers said that several deep-rooted issues exist around connected devices, both used by general enterprises and in medical environments. At the most basic level researchers found that 98 percent of all IoT device traffic is unencrypted, exposing personal and confidential data on the network.
Other issues, like the reliance on outdated legacy protocols and operating systems, are opening up organizations up to older attack techniques that IT teams may not have had to deal with in years. For instance, researchers outlined one attack they discovered of a connected mammogram machine, used in a hospital, by the Conficker worm (malware first discovered more than a decade ago).
Threatpost talks to Ryan Olson, vice president of Threat Intelligence for Unit 42 at Palo Alto Networks, and May Wang, senior distinguished engineer at Palo Alto Networks and former Zingbox CTO, about the top IoT threats.
Download the podcast directly here.
See below for a lightly edited transcript of the podcast.
Lindsey O’Donnell Welch: This is Lindsey O’Donnell Welch and welcome everyone to this week’s Threatpost Podcast. Today we’re talking about insecure IoT devices. We’ve all seen it in the news over and over again – anything from privacy busting connected baby monitors, all the way to doorbells that can be hacked into, and even vulnerable connected surveillance cameras that are used in enterprises. Palo Alto Networks’ Unit 42 team took a deep dive look at the security mess that is IoT devices in their 2020 IoT Threat Report, released Tuesday. In this report Unit 42 analyzed security incidents throughout 2018 and 2019, spanning 1.2 million IoT devices in thousands of physical locations across enterprise IT and healthcare orgs in the United States.
So here to talk about the IoT security landscape with me today is Ryan Olson, the Vice President of Threat Intelligence for Unit 42 at Palo Alto Networks and May Wang, the Senior Distinguished Engineer at Palo Alto Networks and former Zingbox CTO. Ryan and May thanks so much for joining me today.
Ryan Olson: Thanks for having us.
May Wang: Thank you.
LO: There was a lot that stuck out to me in this report, a lot of really interesting statistics. For one, 98 percent of all IoT device traffic is unencrypted. But one big takeaway for me is that you found that more than half of IoT devices are vulnerable to medium- or high-severity attacks, making IoT the low-hanging fruit for attackers. And that speaks to an overall trend in the report about how the general security posture of IoT devices is leaving organizations vulnerable to new IoT-targeted malware and these older attack techniques that IT teams haven’t had to deal with for a long time. Can you talk a bit about the current state of IoT security and what you mean when you say that older attack techniques are cropping up to target these devices?
RO: I’ll go ahead and jump in on that one, Lindsey. So this is Ryan. You know, the two stats that you just mentioned, I think really go hand in hand in answering your question. So 98 percent of IoT device traffic being unencrypted, meaning it’s in the clear, anyone can go and see it if they are able to access it on that network, sort of gives you an indication around how the software and how the protocols for these are 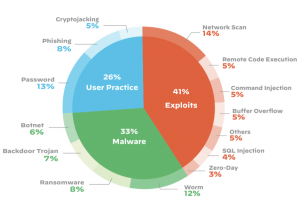 being done. They’re not being developed with the thought around security in mind necessarily, not thinking about the fact that this traffic should be encrypted, it needs to be hidden. And in the same way that staff around 57 percent of the devices being vulnerable to these medium or high severity attacks, in the same way these devices have insecure software or they’ve been deployed in an insecure configuration, which does leave them vulnerable. Either they’ve got software on them that there’s a vulnerability that exists which hasn’t been patched because the device maybe hasn’t been patched in a long time, or maybe there’s no patch available for it, or it has some sort of default password on it, which is widely known and it’s easy to identify that this device could be compromised. These are the kinds of things that really, as the report describes, makes them low hanging fruit, the kind of thing that anyone if they wanted to, could poke at and get into, not like what we typically see in an IT environment where things do more regularly, get patched, have more up to date configurations, and have more defenses in place.
being done. They’re not being developed with the thought around security in mind necessarily, not thinking about the fact that this traffic should be encrypted, it needs to be hidden. And in the same way that staff around 57 percent of the devices being vulnerable to these medium or high severity attacks, in the same way these devices have insecure software or they’ve been deployed in an insecure configuration, which does leave them vulnerable. Either they’ve got software on them that there’s a vulnerability that exists which hasn’t been patched because the device maybe hasn’t been patched in a long time, or maybe there’s no patch available for it, or it has some sort of default password on it, which is widely known and it’s easy to identify that this device could be compromised. These are the kinds of things that really, as the report describes, makes them low hanging fruit, the kind of thing that anyone if they wanted to, could poke at and get into, not like what we typically see in an IT environment where things do more regularly, get patched, have more up to date configurations, and have more defenses in place.
MW: The good news is we do see increasing amounts of IoT devices being deployed in organizations, whether that’s general enterprises or in hospitals. At the same time, because we have so many IoT devices and so many different kinds of IoT devices, and each device can have different hardware, different software, different operating systems, different applications, different protocols. So we consider IoT environment is more of a heterogeneous environment, versus IT environment, which is more homogeneous environment, where we have relatively standard operating systems, relatively standard hardware. So, in order to protect these IoT devices, the traditional IoT device security mechanism are not as effective as they were before, because you cannot have one cross the board mechanism to protect all these devices. So we do see loss of increasing challenges to secure these IoT devices.
LO: Yeah, May, that’s a really good point and the research mentioned that a lot of IoT focused cyber attacks are kind of targeting these legacy protocols that you mentioned that there are all these different types of facets that are going into IoT applications. And I know the research mentioned that the OT protocols that were still being used, that are very old. Is that kind of the driver behind this increase in older attacks behind IoT devices, are there other types of causes behind that as well that are kind of driving this increase?
MW: Yeah, that’s actually a very key driving factor, because we do see different characteristics of these IoT devices compared to traditional IT devices. For example, lots of these IoT devices are in deployment for much longer lifespan compared to IT devices. We probably change our cell phones every other year. We change our laptops 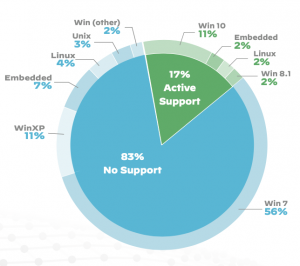 every two, three years. But lots of these IoT devices, they’re in mission critical positions. And they are in deployment, they can be in deployment for 10, 20 years without any updates. And there are lots of urgency to update these devices, whether it’s software, whether it’s operating systems, whether it’s applications, but the challenge is because lots of these devices are in mission critical positions, and the last thing the operational team wants is to bring down their operational devices, so the downtime is the last thing anybody wants. So while the devices are still functioning, well, lots of organizations don’t really patch these devices. Because also there are lots of examples that have already shown even though we tested the patches in the lab, very often when these patches are applied to these IoT devices in the real field, some how they bring down the devices. So for lots of various reasons, lots of these devices, first of all, they are in the field much longer, and they are not updated or patch.
every two, three years. But lots of these IoT devices, they’re in mission critical positions. And they are in deployment, they can be in deployment for 10, 20 years without any updates. And there are lots of urgency to update these devices, whether it’s software, whether it’s operating systems, whether it’s applications, but the challenge is because lots of these devices are in mission critical positions, and the last thing the operational team wants is to bring down their operational devices, so the downtime is the last thing anybody wants. So while the devices are still functioning, well, lots of organizations don’t really patch these devices. Because also there are lots of examples that have already shown even though we tested the patches in the lab, very often when these patches are applied to these IoT devices in the real field, some how they bring down the devices. So for lots of various reasons, lots of these devices, first of all, they are in the field much longer, and they are not updated or patch.
LO: Right. And I know you mentioned downtime, I feel like downtime is such a big issue for kind of operational technology, for industrial control systems and the industrial environment. And speaking of updates and patches, and the research also looked at medical IoT devices that are connected as well. And basically one really interesting angle here is that, you know, as a result, in part of Windows 7 operating system reaching its end of life, there was a huge number of medical imaging devices that are running on unsupported operating systems, that are leaving all of these connected devices vulnerable. I think was the stat was 38 percent of medical imaging devices are running on unsupported OSes? I think that was it. So I thought that really shed some light into kind of at least for the medical space, the issues that connected medical devices are facing too due to that problem. So was there anything that stuck out to either of you in terms of the takeaways from a medical perspective? Because I know the research did go into the implications here for the medical and healthcare space that are using these connected IoT devices.
MW: Yeah, because lots of these imaging systems are using Windows system as you mentioned, because Windows 7 is out of life this past January. So we do see from our data, we see 83 percent of medical imaging systems are using not supported operating systems and that is a severe security issue, even though the number of imaging systems is not the number one in terms of quantity of medical devices we’re seeing, but it is definitely the number one type of devices that bring in the most security issues. Actually, because of that last year NIST initiated a project that we’ve been honored to be selected as a partner to study the security issues of these medical imaging systems. Moving forward, we do think it is we actually for a foreseeable period of time we do see lots of these legacy systems are still going to be deployed, are still going to be used in daily operation to take images of patients to upload images. So we do see, there are two critical things that each organization can do. The first one is to know what kind of devices you have, what kind of operating systems you’re using, what kind of applications you’re using, what kind of software you’re using. And for that we think it’s very important to be able to recognize each endpoint device, not just based on its IP address, but we need to know what kind of device that is. For example, you can have two endpoint devices that are both using Windows operating systems; one is your laptop, one can be an X-Ray machine, taking images for patients. If you only know this is a Windows system, then you can just apply generic security mechanisms to these devices, but if you know one of them is an X-Ray machine, then you know this X-Ray machine is not supposed to go out, browse the internet, it’s not supposed to play YouTube. You’re not supposed to play Pokemon Go on that. All that, a lot more strict security measures should be applied on this particular device. That’s why we think a very important, critical first step is to know what kind of IoT devices you have in your network. And only once you have that visibility, then the second step, you can put the right security policies around these devices. So the second one we emphasize, is you do need to have 24-7 continuous monitoring of these devices, so that you can know what the normal behaviors these devices should carry, and whenever there’s any abnormal behaviors, we can catch them easily.
RO: Just to follow on Mays point around these devices, as well as the earlier point around patching. Patching is not the only solution that’s available for trying to keep these devices secure. IoT devices have a life cycle that they pass through, and understanding that a device may be out of support, may not get any patches in the future doesn’t mean you just have to say, hey, that device is insecure. Let’s just live with that. You can do what May’s describing, put it into an isolated VLAN, where it can’t go and talk to other devices. The last thing you want in a hospital is your device that’s connected, that’s maybe used for medical imaging, on the same network as a doctor who’s sitting down and opening phishing emails and maybe getting malware on his laptop. If you can isolate those devices, so they can’t talk to each other, you can greatly reduce the risks that that critical device is going to be impacted by some sort of malware.
LO: Right. Yeah. And, you know, in the research, speaking of kind of the situations and how you can handle these types of security issues, there was a really interesting kind of incident that you had highlighted, where Zingbox alerted one of the hospitals that they had a security issue with their mammogram that was being under – I believe it was attacked by the Conficker worm – Yeah, can you kind of talk a little bit more about that because I feel like that is a really good illustration of the how how these types of security issues can be handled.
MW: Yes, while we were securing and monitoring one of our customers we notice one of the machines was exhibiting some abnormal behaviors and then we actually were able to identify this machine, it turned out to be a mammogram machine and then the organization brought down the machine and then reimaged the machine and after they put the reimaged machine back into operation, because we are doing continuous monitoring, and we notice abnormal behaviors again, and then turns out the image that was used to reimage this machine was not updated image, it was wasn’t with the latest security patch. So after we identified that problem that this particular machine was taken down again, and finally, was re-imaged by the latest operating systems image, and then brought back online. And actually, while the machine was affected, it was connected online and we noticed it was affecting several other machines at the same time. So we notify the customer and the customer took down all the affected machines and used the latest image to update all these machines and brought all the machines back online. And after continuous monitoring, we notice all these machines were functioning well eventually.
LO: Yeah, no, I just like to hear incidents like that, because it kind of reflects that this is something that’s happening in the real world and it kind of paints a picture of how these types of devices are actually being attacked.
MW: So, yeah, that that is an interesting example, because Conficker is a very old malware in the IT world that we don’t see as much as before, because lots of machines have been updated, have the latest patches, but surprisingly, in the IoT devices, we still see a significant amount of percentage of these medical imaging machines aren’t carrying Conficker.
LO: Right. And that goes back to the central theme here, which is that you are seeing these older attack techniques crop up to really target these IoT security flaws. So and I also had a question too, and just beyond the medical space, what were some of the newer IoT targeting malware strains that are really threatening the IoT landscape at this point, was there anything that stuck out to either view that you either saw as part of your research or are seeing going into 2020?
RO: I think one in particular that’s interesting is one that we call Gafget, which has largely been targeting wireless routers, things that are directly exposed to the internet. It’s a variant of Mirai, which you might have heard of this now or that’s scanning the internet looking for devices like routers, which are exposed the internet and oftentimes have lots of little vulnerabilities in them that have built up over time. And oftentimes Gafget and things like it and Mirai they build up a big botnet and then they’re used to launch DDoS attacks in one direction or another take down gaming servers and other things. That’s a common theme that we’ve been seeing in the world of IoT. And that’s definitely one that I expect to continue this year.
LO: Yeah, definitely. And I do feel also like DDoS attacks are getting bigger, they’re longing, they’re lasting longer. And so I think that that is certainly a big threat that is kind of opening up because of all these insecure IoT devices as well. And one other thing I wanted to kind of touch on is and, we mentioned this earlier, but how enterprises are really facing a lot of IoT devices. And as you guys mentioned, it’s almost like they’re “sitting on a time bomb” of IoT devices, everything from IP phones, to printers, to cameras, to IoT gateways, and wearables. And as part of your research, you looked at some of these connected devices in the enterprise space and looked at not just how many there were, but what kind of security they had. I thought that was a really good approach to take when looking at enterprise connected IoT deployments, what were some of the biggest takeaways that you found there?
MW: We do see in general enterprises, even though the number one devices we’re seeing are IP phones. But actually the type of device that brings in most security issues are cameras, all kinds of cameras, security cameras, surveillance cameras, and it amounts to about 33 percent of security issues we’ve seen among general enterprise IoT devices. And we do see these devices because they are different types of devices, they can have different normal behaviors. That’s why we do see it is very important, not just use the traditional IT security, for example, it’s not more or less like today’s we’re talking about coronavirus, originally we can identify the source of the virus and for people coming from all these highly affected countries, then we can quarantine them, and we can test them. But now, that doesn’t work anymore. The same thing for IoT devices we cannot just rely on “Okay, this is because of this camera, then it’s definitely affected or is definitely not affected, or is only based on this IP address or a packet source address.” But more intelligently we need to continue monitoring all these devices, different behaviors, because for example, cameras can have different normal behaviors than Nest thermostats. So only once we know what their normal behavior is supposed to be, we know what kind of devices they are. And then whenever it does something abnormally, then we can detect them, we can catch them.
LO: I think to that there’s almost like a lack of awareness about the types of connected devices that are in even just a regular office building like I know, when you think of a printer in your office that’s connected, you might not think that it could provide access to print logs or open up as a lateral movement mechanism for other computers on your network or be used in a DDoS attack. So what can we really do to change the mindset of both enterprises or I guess people who are using these connected devices, as well as the manufacturers of the devices and the industry as a whole, so that we can all really better collaborate and recognize IoT security is a top priority that needs to be addressed?
MW: I think that’s exactly the purpose of this threat report, to make people be aware of the current IoT security challenges and how important this issue is. We do see, because of special characteristics of these IoT devices, we do see the security of IoT devices is very important, not only because, if these devices are compromised, the data, the privacy will be affected. But also because lots of devices, these devices are in operations, if they are compromised, we can definitely impact the operations. And also because these devices are, as you mentioned, Lindsey, it’s because these devices are connected to all the networks to IT network to our laptop to our computers that carries sensitive information. So hackers can easily leverage these low-hanging fruits, these IoT devices, to become a stepping stone to more critical, sensitive information. And we do see now more and more organizations are paying more attention to IoT security. And also we start seeing the policymakers are making a move towards this direction. For example, the latest regulation from California and several countries, including the U.S., NIST, and UK and Japan are all coming out of IoT security policies and guidelines. We certainly hope more and more organizations can put more resources and have the right mindset to protect these IoT devices, instead of having to wait till any disaster happens before we take actions.
LO: Those are all really good points. And so, Ryan and May, just before we wrap up, is there any kind of final takeaways that you want to leave us with regarding either this IoT threat report or really what we can look forward to in terms of IoT threats in 2020?
RO: For me, I think the key takeaway is that managing your IoT security starts with visibility. If you don’t know what all these little computers are inside your network, there’s no way you’re going to secure them. And then you need to manage all of those devices through their lifecycle. Every device has a lifecycle, you need to manage it, when it has patches that are available, whether it does in the future or not. And then through its eventual retirement. At some point, these devices will be retired, they won’t be effective anymore, but you need to make sure that they’re effective and secure the entire time that you have them inside your network.
MW: Yeah, with the increasing amount of IoT devices deployed, now IoT devices are around us, all over the place. It brings tremendous amount of efficiency and convenience to our daily life. And the only way moving forward is to secure these devices so that these devices can better serve our daily life and daily work. And as increasing amount of IoT devices are being being deployed, we’ll for sure, see more security issues among all these IoT devices. So for each organization, we need to have mechanism in place, we need to have the tools, the right kind of tools in place, because with these huge amount of IoT devices, and it’s impossible to secure each one manually. So the right tools are very important to be able to identify these devices, to protect these devices, and to segment these devices in the correct way.
LO: Absolutely. Well, Ryan, and May, thank you so much for joining me today and really kind of highlighting some of these top concerns and issues with IoT devices.
RO: Thank you so much, Lindsey.
MW: Thank you Lindsey.
LO: Great. And for our listeners, be sure to catch us next week on the Threatpost Podcast and thank you for listening in.










