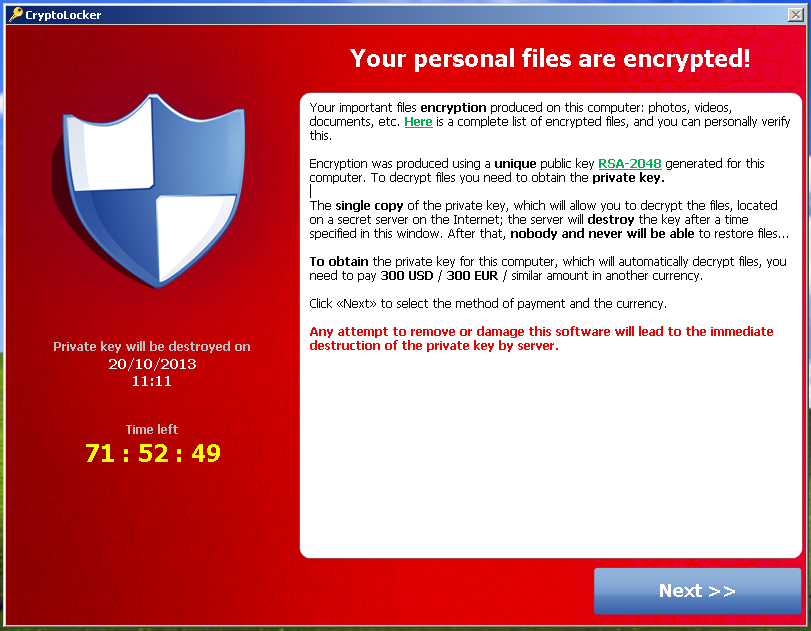
A family of ransomware known as CryptoLocker has added the popular digital currency Bitcoin to the list of payment methods it accepts in exchange for the private key that will decrypt the files encrypted by the malware.
According to a blogpost penned by AlienVault researcher Alberto Ortega, Bitcoin joins online payment services Ukash, MoneyPak, and cashU as possible means of paying the roughly $300 ransom requested by CryptoLocker.
Ransomware is a type of malware that attempts extort money from it’s victims by encrypting their files or locking down their computer in some other way. The malware generally threatens that user files or the victim-machine itself will be inaccessible until the user pays the ransom. There is never any guarantee that paying these ransoms will recover anything. In many cases it is entirely possible that the files aren’t really encrypted or are completely unrecoverable. Paying such ransoms is not recommended. It is better to try to rid the malware using an antivirus product of some kind or by manually removing it from an infected machine.
While the move to accept the pseudo-anonymous crypto-currency in malware-ransom payments is certainly new, it also appears – in this specific case – to have not worked thus far. Ortega examined the transaction record of the Bitcoin address listed in the scammer’s malware interface, finding that scheme has yet to net the criminal a single Bitcoin. As Ortega points out, at present, Bitcoin is used almost exclusively by the technically savvy, who are far less likely to become infected with malware in the first place. However, two similar scams utilizing the same malware family but offering different Bitcoin addresses for payment have made modest profits. These transaction can be monitored on the Bitcoin wallet site, Blockchain.
Payments aside, the malware claims to encrypt photos, videos, documents, and more, even providing victims with a link to a full list of encrypted file-types. The malware creators claim to have deployed RSA-2048 encryption protected by a private key. The ransomware-interface also displays a countdown clock, warning users that if time elapses, the private decryption key will be deleted and there will be no way to recover the encrypted files.
Bitcoin enthusiasts defend the crypto-currency as an easy to use, globally accepted method of buying and selling goods and services online. Unfortunately, Bitcoin is widely used by cyber- and traditional criminals as well. The digital currency offers a number of perks for criminal use, chief among those is the fact that the currency is decentralized. There is no central authority governing Bitcoin, and therefore, there is no way of freezing a Bitcoin account thought to be involved in criminal behavior. Bitcoin is also anonymous and difficult to track.
Earlier this month, the FBI seized and shutdown an underground cybercriminal marketplace known as the Silk Road. The shutdown demonstrated the extent to which users can purchase illegal drugs, weapons, and hacking tools using Bitcoin and money transfer services.
It’s difficult to operate a multi-billion dollar operation like the Silk Road using only Bitcoin though. As Kaspersky Lab principle security researcher Kurt Baumgarnter explained in recent Threatpost interview shortly after the Silk Road takedown, much of the value attributed to Bitcoins is reliant on an emerging industry of overseas currency exchangers that will essentially pay cash for Bitcoins at a discounted rate or – depending on how you look at it – exchange cash for Bitcoins for a fee.