LONDON, U.K. – Researchers have identified a highly-sophisticated Nigerian business email compromise gang targeting U.S enterprises and government institutions.
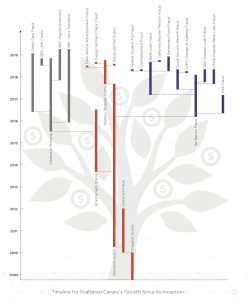
The cybercrime group, dubbed Scattered Canary, has evolved over the past 10 years from a one-man shop working Craigslist scams into a highly-organized cybergang employing dozens of threat actors that targets enterprise organizations with business email compromise (BEC) attacks, researchers said on Wednesday at Infosecurity Europe.
“I think it’s really interesting to look at this group and see how they evolved over time,” Crane Hassold, senior director of threat research at Agari, told Threatpost. “When we look at groups like Scattered Canary, we referred to them as a ‘tech startup’ in the 2008 – 2009 timeframe, as they’re just learning the ropes. And then as they evolve, you see them growing in size, growing in the breadth and depth of scams they’re launching… they’re evolving very much like a business from the startup phase to the corporate phase.”
The BEC group first appeared on researchers’ radar after the group ironically impersonated a senior executive at Agari in an email targeting the company’s chief financial officer in November 2018. Since then, researchers have been tracking the group to get a better sense of its origins, methods used in attacks and targets.
“Since its inception, at least 35 different actors have joined Scattered Canary in its fraudulent schemes,” said researchers with Agari. “The group has turned to a scalable model through which they could run multiple types of scams at the same time. And with multiple tools designed to help them expand their operations and stay hidden from law enforcement, it is no wonder that they are seeing massive success.”
Scattered Canary Evolution
The BEC group’s activity can be traced back to October 2008, with its central figure working as an individual contributor running a variety of Craigslist scams. That scam primarily included a Craigslist check fraud, where a scammer sends a counterfeit check, in exchange for a good on Craigslist – scamming the victim out of whatever they were selling.
Researchers said the original founder behind Scattered Canary worked the Craigslist fraud stint for fifteen months, during which he exchanged over 1,900 emails with victims or scammers related to Craigslist, and made an average amount of $24,000 monthly.
Then, starting in 2010, the cybercriminal began engaging in multiple romance scams. He would interact with victims through social media and text messages, forming an emotional connection, and eventually play on their emotions and persuade them to give him access to their bank or retirement account.
Researchers said that the cybercriminal was highly-effective in playing on victims’ emotions – even sending flowers to two of his victims. And, in March 2016, he even built enough trust with one of these romance victims that she became an unknowing frequent source of new mule accounts for the group.
Between 2015 and 2017, Scattered Canary’s business expanded from romance scams to target larger enterprise organizations with BEC – using methods like credential phishing and spoofing target company domains and requesting payments via wire transfers.
As part of this, the group also expanded from a one-man shop to include up to 19 new members. Some group members were responsible for managing BEC campaigns, some for forging checks and money orders, and still others for harvesting stolen credit card numbers for use in various cons.
Key Tactics
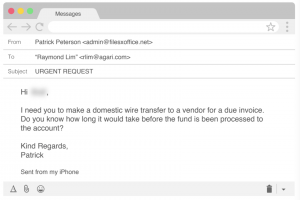
At present, Scattered Canary is a “well-oiled machine” targeting enterprises and government institutions with sophisticated BEC scams like gift card scams and wire transfers.
“By 2017, Scattered Canary had business-critical tools and tactics in place and started to define functional roles across an ever-expanding array of revenue streams,” researchers said. “Like any rapidly-growing company, Scattered Canary took infrastructure into consideration and quickly added Remote Desktop Protocol (RDP) servers to help them scale and coordinate operations. Meanwhile, the organization continued to market-test new approaches to defrauding a growing universe of victims.”
The cybergang uses up to 26 different “message templates” to target organizations with a variety of BEC scams, such as direct deposit and W-2 fraud.
Scattered Canary also notably used VPN infrastructure and applications to make their traffic appear more legitimate, as well as VOIP-based burner phones used to text victims of romance scams, researchers said: The group “maintained subscriptions for several pieces of software to communicate with potential BEC, check fraud, and romance scam victims while remaining somewhat anonymous.”
BEC Scams Increasing
Business email compromise campaigns are nothing new – the scams are popular because they involve little to no technical knowledge, malware, or special tools for cyber criminals.
Despite that, BEC scams are becoming costlier to impacted victims – Overall, in 2018 the FBI reported that BEC scam losses almost doubled year-over-year to reach $1.2 billion. That’s despite an FBI crackdown (dubbed Operation WireWire) on scammers behind several BEC campaigns in June 2018, which resulted in 74 arrests and the retrieval of millions of dollars.
BEC groups like London Blue, Scarlet Widow are more are continuing to hone their techniques and targets to tap into this lucrative profit, researchers said.
“If Scattered Canary can be seen as a microcosm for the rapidly evolving organizations behind today’s most pernicious email scams, this report demonstrates that a much more holistic approach—one based on threat actor identity rather than type of fraudulent activity—is required to detect email fraud and protect organizations,” said Agari.