The TA800 threat group is distributing a malware loader, which researchers call NimzaLoader, via ongoing, highly-targeted spear-phishing emails.
While previous Twitter analysis identified this loader as a mere variant of TA800’s existing BazaLoader malware, new research cites evidence that NimzaLoader is a disparate strain — with its own separate string-decryption methods and hashing algorithm techniques.
The malware loader is unique in that it is written in the Nim programming language. The use of Nim is uncommon for malware in the threat landscape, except in rare cases, such as a Nim-based downloader recently seen being used by the Zebrocy threat group. Because of this, researchers say malware developers may be using Nim to avoid detection by defense teams who may not be familiar with the language.

“Malware developers may choose to use a rare programming language to avoid detection, as reverse engineers may not be familiar with Nim’s implementation, or focused on developing detection for it, and therefore tools and sandboxes may struggle to analyze samples of it,” said Dennis Schwarz and Matthew Mesa, researchers with Proofpoint on Wednesday, in a report shared with Threatpost before publication.
NimzaLoader is used as “initial-access malware” and was first discovered being distributed by the TA800 threat actor in February, said researchers. TA800 is an affiliate distributor of TrickBot and BazaLoader (also known as the BazarBackdoor, BazarCall, etc.). The campaign was spotted targeting about 100 organizations across approximately 50 verticals, Proofpoint researchers told Threatpost.
It is unclear what NimzaLoader’s primary purpose is at this time – however, some evidence suggests the loader is being used to download and execute the Cobalt Strike commodity malware as its secondary payload, researchers said.
BazaLoader Versus NimzaLoader
Some initial analysis of NimzaLoader by various researchers on Twitter has indicated that it may be a variant of BazaLoader, another loader used by TA800 that has the primary function of downloading and executing additional modules. But, researchers with Proofpoint pointed to evidence that they say shows NimzaLoader is not merely a BazaLoader variant: “Based on our observations of significant differences, we are tracking this as a distinct malware family,” they said.
They cited several major differences between NimzaLoader and BazaLoader: For instance, the two samples use different code-flattening obfuscators, different styles of string decryption and different XOR/rotate-based Windows API hashing algorithms, they said. Other tactics that set NimzaLoader apart include the fact that the malware doesn’t use a domain-generation algorithm and that it makes use of JSON in its command-and-control (C2) communications.
The Email Spear-Phishing Campaign
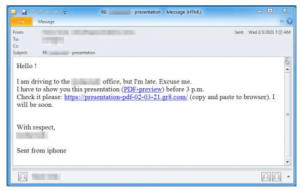
Researchers first observed the NimzaLoader campaign on Feb. 3, in the form of emails with “personalized details” for victims – including their names and company names.
The messages purport to come from a coworker, saying he is “late” driving into the office and asking the email recipient to check over a presentation. The message sends a URL link (which is shortened) that purports to be a link to a PDF preview.
If the email recipient clicks on the link, they are redirected to a landing page hosted on email marketing service GetResponse. That page links to the “PDF” and tells the victim to “save to preview.” This link in turn actually takes the victim to the NimzaLoader executable.
NimzaLoader Malware Executable
Upon closer inspection, researchers found that NimzaLoader is developed using Nim (as evidenced by various “nim” related strings in the executable). The malware uses mostly encrypted strings, using an XOR-based algorithm and a single key per string. One encrypted string contains a timestamp and is used to set an expiration date for the malware. For instance, in one analyzed sample the expiration date was set to Feb. 10 at 1:20:55.003 p.m. – meaning the malware would not run after that date and time.
Most of the other strings contain command names. These commands include the ability to execute powershell.exe and inject a shellcode into a process as a thread. While the NimzaLoader C2 servers were down at the time of research, researchers said a public malware sandbox appeared to show the malware receiving a PowerShell command that ultimately delivered a Cobalt Strike beacon.
“We are unable to validate or confirm this finding, but it does align with past TA800 tactics, techniques and procedures (TTPs),” they said.
TA800 Threat Group: The Future of NimzaLoader
Researchers linked NimzaLoader back to TA800, a threat group that has targeted a wide range of industries in North America, infecting victims with banking trojans and malware loaders.
According to Proofpoint researchers, TA800’s previous campaigns have often included malicious emails with recipients’ names, titles and employers, along with phishing pages designed to look like the targeted company. Researchers noted that the malware shows TA800 continuing to integrate different tactics into their campaigns.
“It is… unclear if Nimzaloader is just a blip on the radar for TA800—and the wider threat landscape—or if Nimzaloader will be adopted by other threat actors in the same way BazaLaoder has gained wide adoption,” said researchers.
Check out our free upcoming live webinar events – unique, dynamic discussions with cybersecurity experts and the Threatpost community:
- March 24: Economics of 0-Day Disclosures: The Good, Bad and Ugly (Learn more and register!)
- April 21: Underground Markets: A Tour of the Dark Economy (Learn more and register!)