A proof-of-concept (PoC) attack details how an attacker can gain access a victim’s Microsoft Live webmail session, without having the person’s credentials. It relies upon the hijack of a Microsoft-owned Live.com website subdomain.
The PoC, developed by CyberInt, demonstrates what it characterizes as a “high-severity vulnerability” in a Microsoft Live subdomain (now fixed) that could have been leveraged for full Microsoft account takeover. From there, an adversary could have carried out broad attacks against multiple organizations and their customers.
While the PoC was specifically for a fixed issue, it demonstrates that session hijacking can open the door to advanced attacks, depending on the domain in question.
Subdomains are areas of a main website that can be used to host things like HR information, marketing materials, extranet sites, customer portals, promotional materials, microsites and so on; i.e., marketing.company[.]com, if it existed, would be a subdomain of company[.]com. Subdomain URL names are sometimes also aliases for content hosted on a cloud service, or they redirect traffic to a different domain – and this is where the trouble comes in.
These subdomains can become open to session-hijacking (i.e., takeover) when they’re no longer used by their original owners, because many organizations simply don’t remove or update dormant and expired pages and accounts.
“A threat actor can review the target organization’s domain name server (DNS) information to determine if any subdomain records are configured to redirect or act as an alias for either an expired domain or a disused third-party [cloud] service,” explained CyberInt, in a white paper shared with Threatpost. “In the case of expired domains, the threat actor can purchase the domain from any registrar or, in the case of third-party services, configure a new service using a previously configured or expired name to hijack the subdomain.”
The PoC makes use of the latter tactic. Using a tool that CyberInt developed in-house to find subdomains that are vulnerable to session-hijacking, it found a subdomain of Live.com called “Windows Live,” hosted on the Azure cloud platform. The subdomain lacked an updated DNS configuration, which opened the door to hijacking.
“Many cloud-based services allow you to do a manual configuration for your subdomain,” Jason Hill, CyberInt lead researcher, told Threatpost in an interview. “But if the service hosted on that subdomain is shut down, and the DNS settings are not updated, suddenly the URL is pointing to an unconfigured cloud service. This allows another person to go in, configure that cloud service, and use the exact same subdomain name for their own purposes. They can log in and effectively take control of the old identity.”
Once a subdomain has been hijacked, the threat actor can then take advantage of the reputation and legitimacy of the target organization to mount a range of attacks. This includes publishing content that appears to originate from the target’s own website. Use cases include posting fake content meant to create reputational damage; getting past blacklist checks; hosting phishing or spear-phishing content to target the organization’s employees or customers; create watering-hole attacks; and leveraging the subdomain for web-application attacks, such as cross-site request forgery (CSRF) and cross-site scripting (XSS), as well as authentication bypass and account takeover.
In the case of the Live subdomain, CyberInt researchers decided to see if more advanced attacks would be possible.
“We wanted to see what we could do,” Hill explained to Threatpost. “We could see that Microsoft Live cookies can be configured to be accessible by all Live subdomains, so we developed a PoC code that could steal any cookies that a user has.”
So an attacker could create a phishing email that says, log on and update your Live account. That could direct victims to the hijacked subdomain. It’s convincing, given that the site is a legitimate Live.com domain. Adversaries could then write a script that steals and and then leverages the stolen cookies to gain access to various services.
As the firm explained in its white paper, “In this instance the PoC, having hijacked a Microsoft-owned live.com subdomain, weaponizes it by hosting a Flask (Python) application that would hijack the webmail session of any visiting victim.”
For testing purposes, this PoC simply takes a screenshot of the victim’s webmail inbox – although the firm said that it would be “trivial” to modify the attack to perform other unscrupulous tasks. Hill noted that it would be easy to use this same method to steal information from the mailbox or to send out emails; also, the gambit would work for gaining access to user sessions on other Live.com services.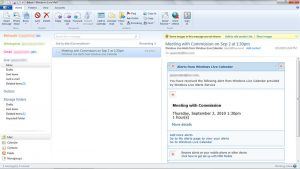
While the Live.com subdomain was the subject of the PoC, Hill noted previous research showing that 96 percent of Fortune 500 companies have subdomains in place, and about a quarter of them are at risk for subdomain hijacking. It’s not a new phenomenon, but one that remains an issue in cloud and web security.
“In practice, maintaining complex DNS configurations in ever-changing environments can result in legacy records being forgotten or inadvertent mistakes being made,” according to Cyberint’s report. “Without robust processes to sanity check new records and audit old records, many will fail to resolve mistakes and remove dormant or expired entries.”










