It didn’t take long for attackers to start capitalizing on the popularity of Pokémon GO. Shortly after Niantic, the company behind the now ubiquitous app, released it last month, researchers spotted a malicious, backdoored version of the app on a file repository service.
Now attackers are pushing SMS spam messages to entice Pokémon GO players to visit a series of malicious websites.
Researchers at AdaptiveMobile, an Irish mobile security firm, said attackers sent thousands of SMS messages to North American users over the last few months encouraging them to visit one of the malicious sites, pokemonpromo[.]xxx. The site, which mimicked the actual Pokémon GO site and has since been taken offline, claimed it would supply users with additional features if they referred 10 of their friends, which likely would lead to more spamming.
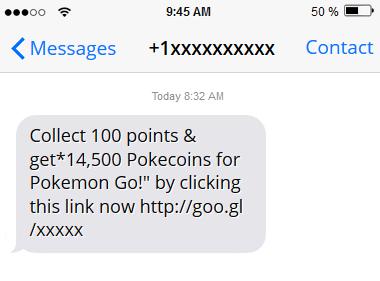 The security company said its observed similar scams, such as a campaign that purports to offer victims 14,500 Pokécoins – the game’s currency – when they collect 100 points, making the rounds as well.
The security company said its observed similar scams, such as a campaign that purports to offer victims 14,500 Pokécoins – the game’s currency – when they collect 100 points, making the rounds as well.
According to Cathal Mc Daid, the firm’s Chief Intelligence Officer, the messages contained Google shortened URLs that ultimately led to spam sites, some Pokémon GO related, some not.
Mc Daid, who tracked the Pokémon GO campaigns, said he spotted another site, pokemon[.]vifppoints[.]xxxx, advertised on social media and Pokémon forums, promising to give users Pokécoins if they shared the site with five friends. Another site, dubbed Pokémon Generator, encouraged users to give their login credentials – which in most instances mean their Google emails and passwords – in order to have Pokécoins deposited to their accounts.
Until buzz around the app subsides, the attacks will continue, Mc Daid said Wednesday.
“It is likely that we will continue to see Pokémon GO spam for some time – at least until the hype around the app recedes,” Mc Daid said, “Be wary of any unsolicited SMS messages you receive mentioning the app – particularly if the message contains a URL as this may lead to a phishing web site or a site containing malware.”
The scams come on the heels of news last week that a new strain of ransomware, Hidden-Tear, is masquerading as a Pokémon GO application for Windows.
Similar to Locky, the ransomware encrypts files using AES encryption and attaches “.locked” to the end of files. Unlike other forms of ransomware however, Hidden-Tear installs a backdoor Windows account and spreads the executable to other drives, creating network shares.
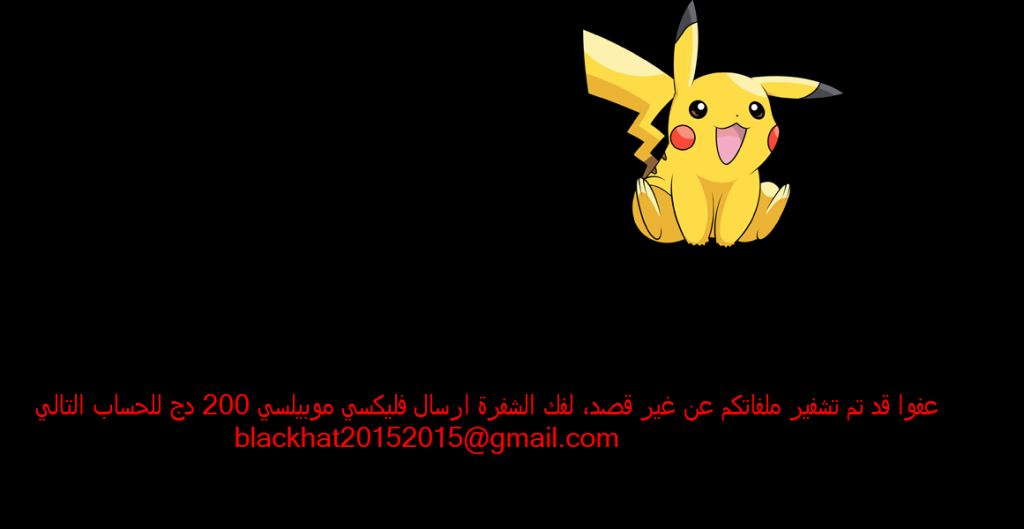
Lawrence Abrams, who blogs at BleepingComputer.com, warned on Sunday that Hidden Tear is specifically targeting Arabic users. After it infects victims, a ransom note screensaver – complete with a Pikachu image – is displayed and written in Arabic. A separate ransom note – “هام جدا.txt” – which translates to “Very important.txt” also appears on the victim’s desktop.
(via BleepingComputer.com)
The fact that the ransomware appears to be custom made for an Arabic audience is significant, experts claim.
“Using a popular app like Pokémon GO to spread malware is nothing new; we see this whenever there’s a topic that is popular,” Javvad Malik, a security evangelist at AlienVault said Wednesday, “The unique thing about this attack is the fact that it’s tailored for an Arabic audience – many of whom may not have encountered malware in their native language before.”
Pokémon GO, which surpassed 100 million total downloads earlier month and shows little signs of slowing down, was met with a privacy controversy when it first launched in mid-July.
Niantic, a Google spinoff, was forced to address why the app was requesting the full Google account information of its users. Niantic ultimately said it wasn’t the company’s intent to request as much information as it did and has since pushed an update ensuring the app only requests basic Google profile information.