Last year, 2.3 billion credentials were stolen from 51 different organizations, including Ancestry.com, Imgur and Virgin America. Where do all those user names go?
In Shape Security’s second annual Credential Spill Report, it found that billions of stolen digital IDs are contributing to an epidemic of credential-stuffing and account-takeover fraud.
Credential-stuffing is a technique used by hackers to gain fraudulent access to an account. It uses automated scripts to try multiple username/password combos against a targeted website. Successful account compromises from credential-stuffing are typically tied to the fact many users reuse the same credentials on multiple accounts.
The potential losses tied to credential spills is $50 million a day globally, and it takes an average of 15 months for a credential breach to be reported.
“Half of all credential spills were discovered and reported within the first four months of the compromise. However, because some spills take years to discover. It took an average of 15 months between the day that an attacker accessed the credentials to the day the spill was reported in 2017,” according to the report (PDF).
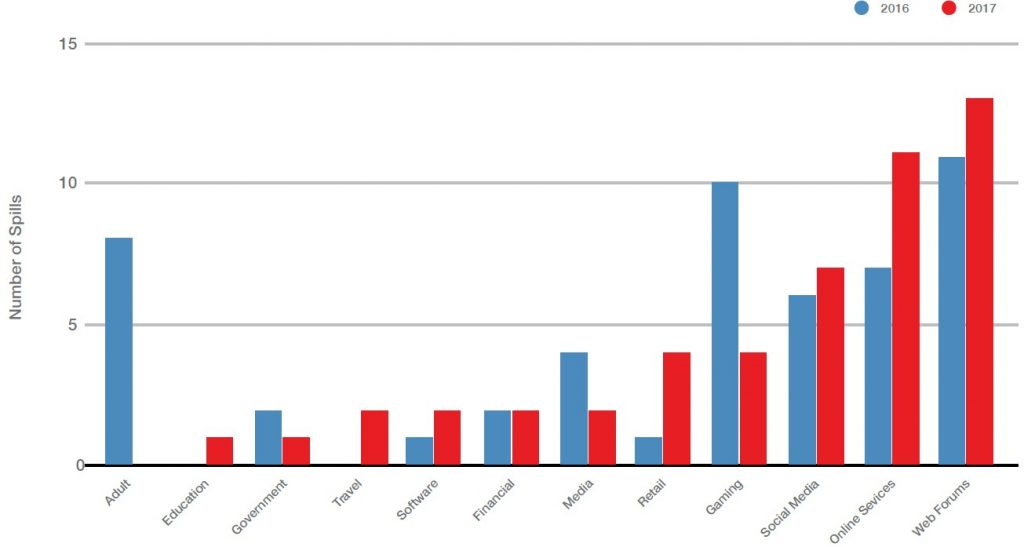
Further, no sector is immune to credential stuffing, as seen in this chart:
The sky-high cost of spills, according to the report, takes into account the cost of fraud prevention. Shape Security does not specify what those measures are.
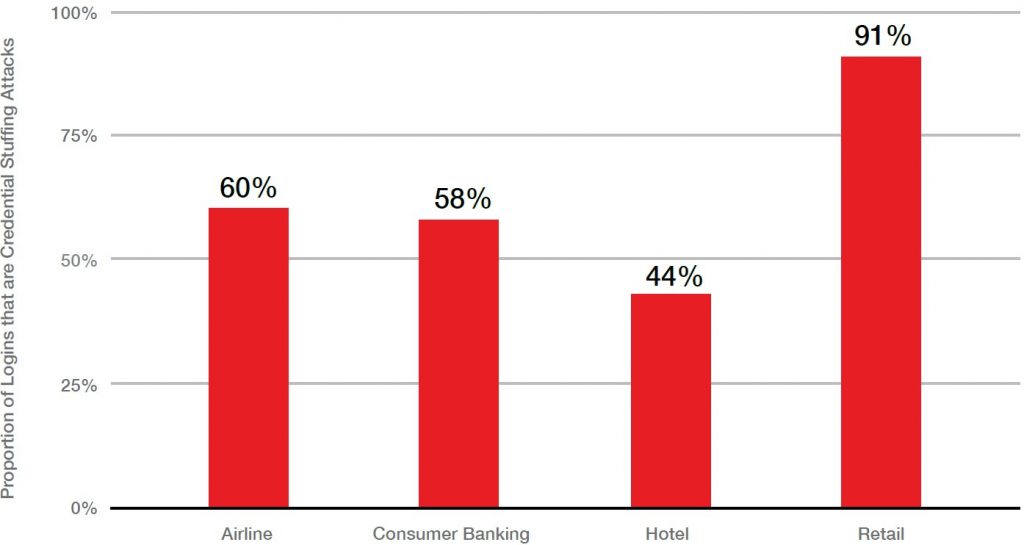
Equally disturbing, 80 to 90 percent of log-in attempts at online retailers is tied to attempted credential-stuffing by hackers. The report added that 82 percent of log-in requests at hotel and hospitality websites and services can be attributed to the technique. And, about 65 percent of log-ins against airlines are credential-stuffing attacks.
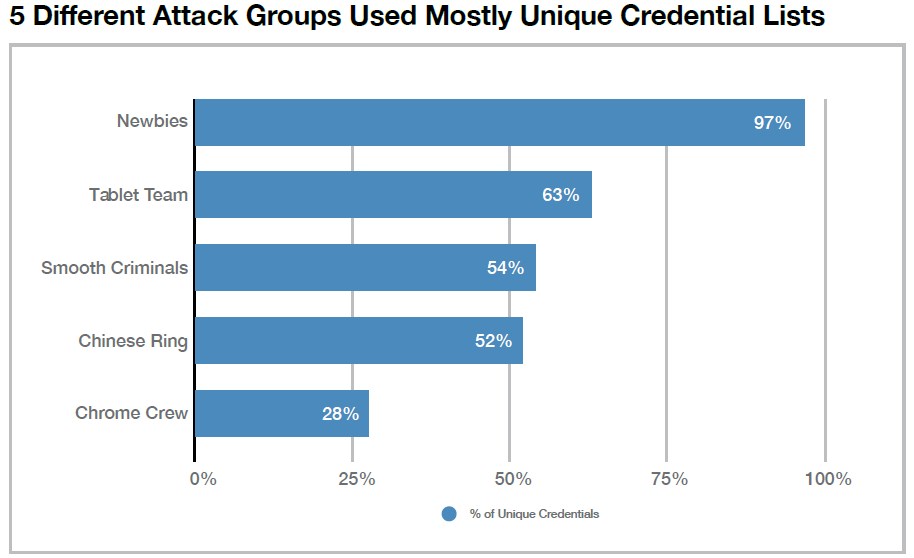
Researchers also said they observed five different attack groups performing these kinds of attacks on a “top-5 U.S. bank’s” mobile app over the course of two weeks. “In total, the attackers targeted 363,000 bank accounts, or approximately 4,000 accounts per day,” according the report.
The report also identified categories of cybercriminals in this space. Newbies are identified by Shape Security as a group new to credential-stuffing. Tablet Team adversaries mainly target Android tablet users with Android tablet-specific apps. Smooth Criminals were identified as sophisticated, able to target Android and iOS platforms with a higher-than-average log-in success rate. China Ring, as the name suggests, originates in China. And members of the Chrome Crew heavily favors user agent strings associated with Chrome 30, according to researchers.