 In a project that found more than 80 million unique IP addresses responding to Universal Plug and Play (UPnP) discovery requests, researchers at Rapid7 were shocked to find that somewhere between 40 and 50 million of those are vulnerable to at least one of three known attacks.
In a project that found more than 80 million unique IP addresses responding to Universal Plug and Play (UPnP) discovery requests, researchers at Rapid7 were shocked to find that somewhere between 40 and 50 million of those are vulnerable to at least one of three known attacks.
A Rapid7 white paper enumerated UPnP-exposed systems connected to the Internet and identified the number of vulnerabilities present in common configurations. Researchers found that more than 6,900 product models produced by 1,500 different vendors contained at least one known vulnerability, with 23 million systems housing the same remote code execution flaw.
Between June 1 and Nov. 17, 2012, Rapid7 conducted weekly scans that sent simple service discovery protoc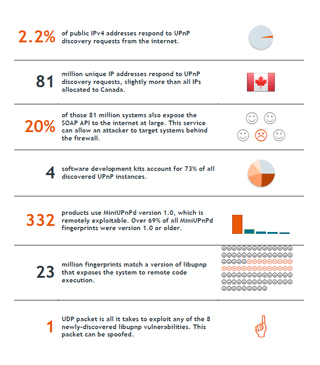 ol (SSDP) requests to each routable IPv4 address. In all, 2.2 percent of all public IPv4 addresses responded to the standard UPnP discovery requests. So, 81 million unique IP addresses responded and, upon deeper probing, researchers determined some 17 million further systems exposed the UPnP simple object access protocol (SOAP). This level of exposure was far higher than researchers had expected, according to the report.
ol (SSDP) requests to each routable IPv4 address. In all, 2.2 percent of all public IPv4 addresses responded to the standard UPnP discovery requests. So, 81 million unique IP addresses responded and, upon deeper probing, researchers determined some 17 million further systems exposed the UPnP simple object access protocol (SOAP). This level of exposure was far higher than researchers had expected, according to the report.
Rapid7 claims that the UPnP protocol has suffered from a number of security problems over the last decade or so. Despite rarely implemented authentication mechanisms, the presence of privileged capabilities on questionable networks, and common programming flaws, Rapid7 decided to focus its research on three classes of problems: programming flaws in common UPnP SSDP implementations that can be exploited to crash the service and execute arbitrary code; exposure of the UPnP control interface that exposes private networks to attacks from the Internet; and programming flaws in the UPnP HTTP and SOAP implementations that can be exploited to crash the service and execute arbitrary code.
“This research was primarily focused on vulnerabilities in the SSDP processor across embedded devices,” Rapid7′ CSO HD Moore elaborated via email. “The general process was to identify what was out there, make a list of the most commonly used software stacks, and then audit those stacks for vulnerabilities. The results were much worse than we anticipated, with the most commonly used software stack (libupnp) also being the most vulnerable.”
According to Moore, the two most commonly implemented UPnP software libraries both contain remotely exploitable vulnerabilities. More than 73 percent of systems uncovered by SSDP were derived from just four development kits: Portable SDK for UPnP Devices; MiniUPnP; a commercial stack likely developed by Broadcom; and one other kit whose developer could not be determined. The most current version of Portable UPnP SDK–at the time the research was conducted–accounted for the previously mentioned 23 million IPs that are vulnerable to remote code execution through a single user datagram protocol packet.
Most Portable UPnP SDK devices are not running on the latest version of the software. Researchers determined that the users running older versions of Portable UPnP SDK could be compromised by no fewer than eight remotely exploitable flaws.
The latest version MiniUPnP (1.1) fixed a remotely exploitable stack overflow in the SOAP handler from its earlier version (1.0), but the SSDP determined that more than 14 percent of MiniUPnP users have yet to update and that 330 separate products remain vulnerable. The MiniUPnP library was also vulnerable to a parsing flaw in the SSDP handler that has since been patched.
UPnP is, according to Rapid 7, a protocol standard, often enabled by default, that allows computers and various other network connected devices to communicate with one another and simplifies the discovery and control of network devices. Devices with UPnP enabled by default include smart TVs, IP cameras, printers, media servers and routers to name a few. It is enabled by default on Mac OS X, Microsoft Windows, and a number of Linux distros. Different devices have different capabilities but some common functions include incoming port mapping on home routers, identification of network printers, and managing media services.
Rapid7 is encouraging that users disable UPnP on all Internet facing systems and replace any systems that do not offer the ability to disable the protocol. Some of these vulnerabilities, such as the Portable UPnP SDK and MiniUPnP, have been patched, but as Moore notes, it takes time for the various device makers and application developers to implement the patch into their products. In the meantime, users will remain vulnerable. He also explains that a number of products are “no longer shipping,” meaning that users of that equipment will not receive patches and will remain vulnerable until they remove or replace the products in question.
Rapid7’s ScanNow tool tocan be used check whether systems are vulnerable.
In the white paper, Rapid7 goes on to make a number of recommendations to Internet service providers, businesses, and home and mobile users that may be vulnerable as well providing in depth analysis of the specific vulnerabilities themselves.










