We live in an increasingly connected world, but even in an age when DDoS attacks can take entire airlines offline, many critically sensitive industrial control systems (ICS) are still connected to the internet.
A pair of reports released today by Kaspersky Lab reveal how dire the situation really is. In a scan, it found nearly every industrial control system that’s connected to the internet suffers from remotely exploitable vulnerabilities and is vulnerable to man-in-the-middle attacks.
According to a review of publicly accessible ICS hosts, a staggering 91.1 percent likely belong to large organizations and have vulnerabilities that can be exploited remotely; 3.3 percent of the hosts contain remotely exploitable vulnerabilities that are considered critical.
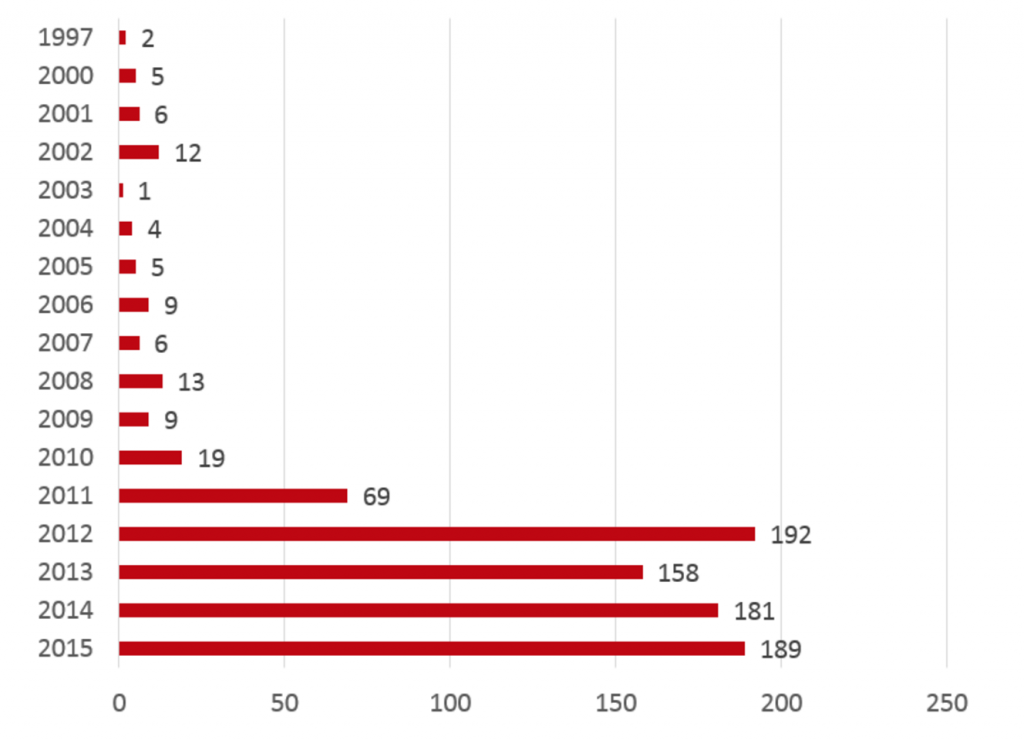
One report, “Industrial Control Systems Vulnerabilities Statistics,” carried out by the company’s Security Services team, takes a comprehensive look at industrial control system security throughout the 2015 calendar year, breaking down all 189 ICS vulnerabilities dug up in 2015. While it may seem like there’s been an influx of ICS bugs over the last 12 months, the figure is actually more or less in line with statistics from the last few years and comes in just three bugs fewer than the all time high of 192 discovered in 2012.
The number 189 vulnerabilities does mark a tenfold increase from 2010 however, when only 19 vulnerabilities were identified.
ICS Vulnerabilities Through The Years
In another report, “Industrial Control Systems and Their Online Availability,” Kaspersky Lab discovered 188,019 hosts with ICS components, spread across 170 countries. Researchers at the firm deduced that 13,698 of those hosts likely belong to large organizations; stressing that in many instances, the corporations may be responsible for regulating energy, aerospace, oil, gas, chemical, or other industries.
Networking devices were the most popular type of ICS component Kaspersky found connected to the internet, followed up by PLCs, or programmable logic controllers, and SCADA, or supervisory control and data acquisition, systems.
As far as vendors go, products from Siemens, Schneider Electric, and Hospira were the biggest culprits last year, the report claims, with each responsible for 33, 18, and 12 vulnerabilities, respectively.
Siemens and Schneider Electric regularly appear on the Industrial Control Systems Cyber Emergency Response Team’s (ICS-CERT) list of advisories. In one instance last year – as the report notes – Siemens had to patch an authentication bypass vulnerability that plagued small telecontrol systems made by the company called SICAM MIC devices. An attacker could’ve obtained administrative access to the devices through HTTP requests.
Schneider meanwhile was forced to patch multiple vulnerabilities, including a locally exploitable flaw, and a hard-coded credential, in its software, following a disclosure at DEFCON last summer.
Hospira made history last summer after its Lifecare PCA3 drug infusion pumps were found susceptible to multiple vulnerabilities. The flaws, which were largely uncovered by security researcher Billy Rios and Jeremy Richards, prompted the Food and Drug Administration to issue a public safety notification, the first of its kind, warning hospitals to stay away from the devices.
Kaspersky found that a whopping 91.6 percent of the externally available ICS devices it discovered used inherently insecure protocols like Telnet and SNMP. The lion’s share of those devices, 116,900 in total, used HTTP, something that could allow an attacker to compromise the devices, potentially through a man-in-the-middle attack.
The company performed its research using a fingerprint knowledge base of 2,000 records, something which allowed it to identify select ICS vendors and versions in ICS search engines such as Shodan and Censys. It also used a combination of open source intelligence and information from ICS-CERT, the NVD/CVE database, and other sites.
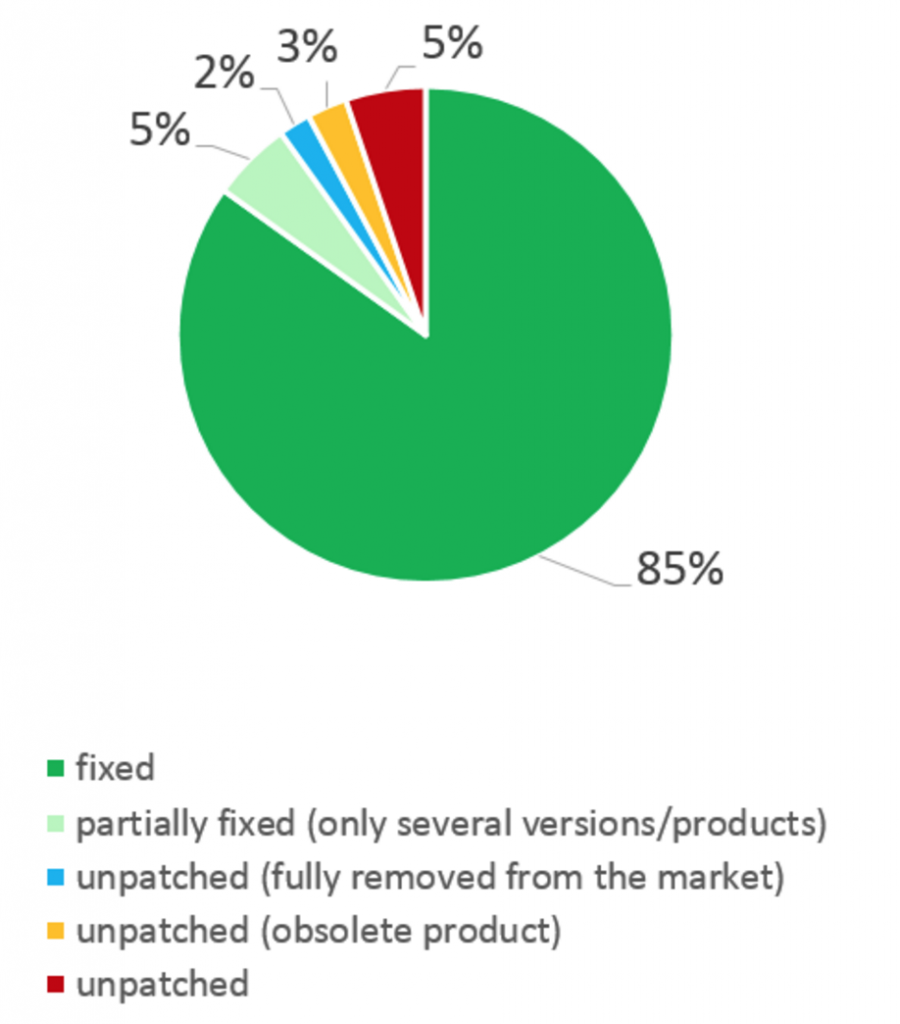
For anyone looking for a silver lining to the report, one of the more positive figures comes to the forefront if you only take ICS-CERT data into account: vendors fixed 85 percent of published vulnerabilities last year. Five percent of vulnerabilities, 19 vulns in total – 14 that are high risk – were never patched in 2015 however. The remaining 10 percent includes vulnerabilities that were either partially fixed, or left unpatched simply because the product was deemed obsolete.
ICS Vulnerabilities in 2015
While it’s scary enough that some of the vulnerabilities from last year never got fixed, stories about factories, power plants, airlines, and other industrial systems being taken offline due to new vulnerabilities continue to command headlines in 2016.
Earlier this year a man associated with the Iranian government was indicted after being accused of hacking into the SCADA systems of a small dam in Rye, New York. The man was able to monitor water temperature, water levels, and more data pertaining to the dam. He reportedly would’ve even been able to control a gate in the dam, had it not already been disconnected for maintenance.
Polish planes at Warsaw’s Chopin Airport were grounded for a weekend last June after an airline there was hit by a DDoS attack. Earlier this year a cyber attack – ultimately fingered as the BlackEnergy1 APT – struck Western Ukraine power company Prykarpattyaoblenergo leaving hundreds of thousands of residents in the Ivano-Frankivisk region of the country in the dark.
A report from IBM just two weeks ago revealed from last March to this May, denial of service attacks and malicious attachments accounted for nearly 50 percent of attacks against the control networks of planes, trains, trucks, and ships.
“We are seeing this industry emerging as high-value target right alongside healthcare, manufacturing, financial services and government,” Michelle Alvarez, a researcher with IBM told Threatpost at the time.
The numbers in today’s Kaspersky Lab report echo those sentiments.
“Our research shows that the larger the ICS infrastructure, the bigger the chance that it will have severe security holes,” Andrey Suvorov, Head of Critical Infrastructure Protection at Kaspersky Lab said of ICS security.
“This is not the fault of a single software or hardware vendor. By its very nature, the ICS environment is a mix of different interconnected components, many of which are connected to the Internet and contain security issues,” Suvarov said.