An academic study set out to prove whether it’s better to protect your Android phone with a PIN or a swipe pattern. The answer is PIN. At least when it comes to proximity attacks, namely someone lurking about trying to guess your PIN or unlock pattern.
The study (PDF), published Friday by researchers at the U.S. Naval Academy and the University of Maryland Baltimore County, found a lurker spotting a single observation of a user unlocking their Android phone using a graphical pattern unlock (swipe pattern) were able to capture the pattern 64 percent of the time. If observed twice, the same person could repeat the pattern with 80 percent accuracy.
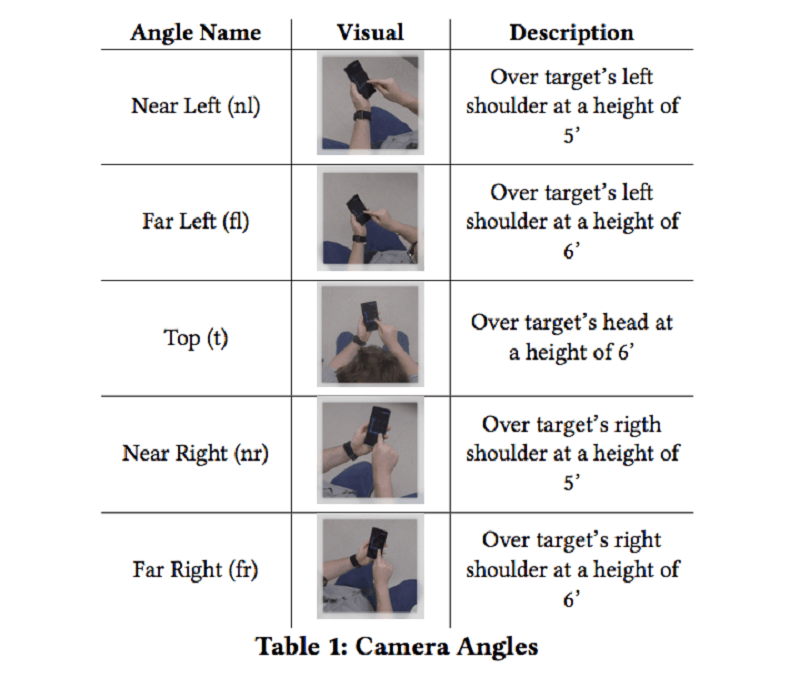
Granted an over-the-shoulder attack is extremely low-tech. But what was interesting about the study was that viewers were able to capture the patterns when five or six feet away and from different angles after a single viewing.
On the flip side of the study, a lurker trying to spot a six-digit PIN were only 11 percent successful after one viewing, and 27 percent after two.
Researchers concluded that patterns are infinitely easier for the brain to recall versus even a 6-digit number string.
The test involved 1,173 online users selected from Amazon’s Mechanical Turk crowdsourcing platform and 91 subjects who conducted the test in person. Online participants were shown videos of people unlocking their phones using unlock patterns and PINs. Videos also included multiple angles and distances.
“Analyzing the results, we found that in all settings, Android’s graphical pattern unlock is the most vulnerable, especially when feedback lines are visible,” authors of the report wrote. Newer smaller-screened iPhones that require a 6-digit passcode, are more secure, researchers said.
“Overall, it appears that the larger phones provide less security for shoulder surfing,” researchers said.
The solution is easy, researchers said: Don’t use unlock patterns to protect your phone. And when using PIN codes, make sure that the number sequence is random enough that it isn’t easy for an over-the-shoulder hacker to recall later.
For those that can’t part ways with the pattern unlock, researchers found when the “feedback” lines (lines that trace your finger’s path) were turned off it was incrementally harder for attackers to remember the trace pattern. Only 35 percent of study participants could remember the pattern with no trace lines versus 64 percent with.
“These results support what we as a community have believed to be true anecdotally, and further demonstrates that current authentication methods provide stronger security against shoulder surfing than one might expect,” researchers said.
This isn’t the first time the researchers have scrutinized PIN and swipe patterns. Previous studies (PDF) found that smudge prints on phones can also be used to lift unlock codes from a phone. So called, smudge attacks use the oily-residues of prior entries to determine the pattern.
Researchers said the paper will be formally presented at the Annual Computer Security Applications Conference in Puerto Rico in December.