Apache recently patched Tomcat, fixing a trio of information disclosure bugs and a denial of service bug in the open source web server and servlet container.
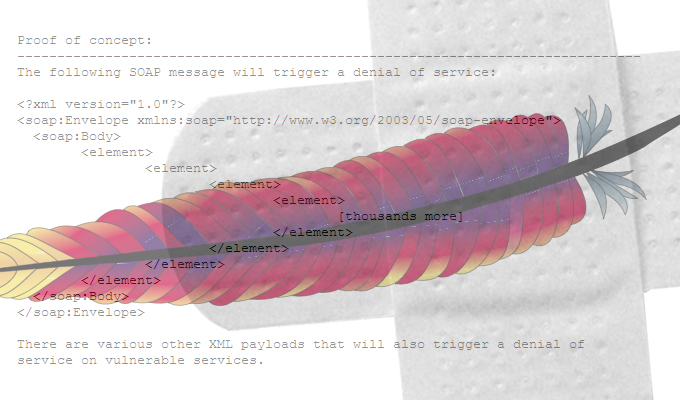
The denial of service bug, discovered in February by David Jorm of the Red Hat Security Response Team, could have allowed an attacker to create a malformed chunk size as part of a chunked request that would’ve allowed an unlimited amount of data to be streamed to the server. This would have bypassed the size limits enforced on a request and triggered a denial of service condition.
 The information disclosure bugs – all discovered by Tomcat’s security team – could have basically allowed an attacker to bypass limits set by the software.
The information disclosure bugs – all discovered by Tomcat’s security team – could have basically allowed an attacker to bypass limits set by the software.
The first one (CVE-2014-0096) could’ve let a malicious web app bypass the file access constraints set by the security manager by using external XML entries. The second (CVE-2014-0119) could’ve allowed the same thing, the bypass of limits set on XML external identities, but also allowed the visibility of the XML files processed for other web apps deployed on the same Tomcat instance.
The last information disclosure bug (CVE-2014-0099) dealt with a problem in the way the code used to parse the request content length header. It didn’t check for overflow when all was said and done. This led to a request smuggling vulnerability when the web server was behind a reverse proxy that correctly processed the content length header. Request smuggling vulnerabilities, when submitted data is incompletely parsed through a HTTP system as a proxy, can be tricky and lead to a handful of other attacks like cache poisoning, session hijacking and cross-site scripting (XSS) attacks.
The information disclosure bugs, while discovered in February, March and April, were not made public until Tuesday, along with the denial of service issue.
Users of vulnerable versions, 8.0.0-RC1 to 8.0.3, 7.0.0 to 7.0.52, and 6.0.0 to 6.0.39, are being encouraged to update to the most recent builds to mitigate the bugs.