Gatekeeper is Mac OS X’s guardian against rogue applications and malware sneaking into Apple’s famous walled garden. It’s also been a favorite target of researchers and advanced attackers desperate to gain control of Apple devices.
Tomorrow at Virus Bulletin in Prague, researcher Patrick Wardle, director of research at Synack, will demonstrate a Gatekeeper bypass he’s been cooking up for some time. Wardle told Threatpost he has shared his findings with Apple, which is reportedly working on a short-term mitigation until a full patch can be pushed out to users.
The problem is that Wardle’s bypass could require some re-architecting of the operating system to fully address the design weakness being exploited.
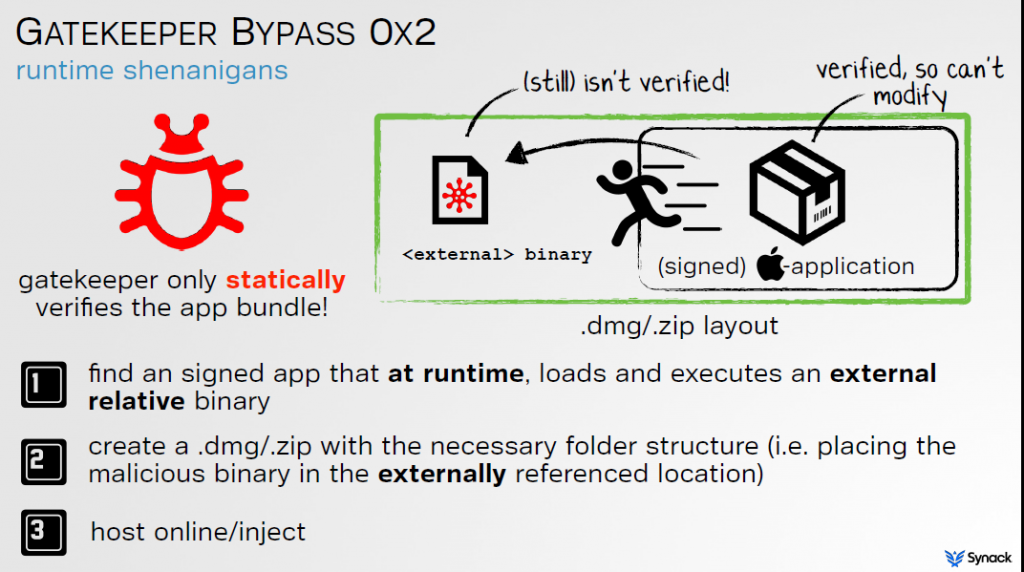
Gatekeeper performs a number of checks on apps before it allows one to execute on an Apple machine. For example, it will not allow code to execute that’s not signed with an Apple developer certificate or if it’s not downloaded from the App Store. But what Gatekeeper fails to do, Wardle said, is check whether an app runs or loads other apps or dynamic libraries from the same or relative directory.
Gatekeeper signs off only on the first static check and trusts the application is secure and behaving accordingly. Wardle said that an attacker could trick the user into downloading a signed and infected app from a third-party source, or if in a man-in-the-middle position, for example, could load a malicious library into the directory over an insecure HTTP download, and gain that initial foothold onto the machine.
In the case of his exploit, Wardle found signed Apple binaries that he used to craft his attack, which would take the form of a DMG file (Apple disk image file) he tricks the user into downloading, for example. The user is presented with a traditional app icon that when executed looks for the malicious executable in the same DMG file and executes that.
“It’s not super complicated, but it effectively completely bypasses Gatekeeper,” Wardle said. “This provides hackers the ability to go back to their old tricks of infecting users via Trojans, rogue AV scams or infect applications on Pirate Bay. More worrisome to me is this would allow more sophisticated adversaries to have network access. Nation states with higher level access, they see insecure downloads, they can swap in this legitimate Apple binary and this malicious binary as well and man-in-the-middle the attack and Gatekeeper won’t protect users from it anymore.”
Wardle, who demonstrated Apple dylib hijacking attacks at CanSecWest this year, said he tested his attack on Yosemite versions of OS X, but believes this affects all versions, including El Capitan, the upcoming release. Wardle said his attack worked on the most recent beta version of El Capitan, released recently to developers and he was still able to bypass Gatekeeper.
“In my opinion, Gatekeeper is a good idea. Apple touts it as one of the cornerstones of their security posture as why Macs are more secure. But the reality is that sure Gatekeeper can protect naïve users from lame attackers, but sophisticated adversaries, I don’t think Gatekeeper is a stumbling block at all,” Wardle said. “It’s not really a bug, but a limitation of Gatekeeper. I think fixing this requires significant code changes. It’s not like they can just patch a buffer overflow with an extra check. This will take some significant changes.”
Until Apple fixes the vulnerability, users should take care in download apps only from trusted sources and over HTTPS in order to ward off the potential for man-in-the-middle attacks. Wardle said he’s not aware of attacks similar to his being used in the wild, but cautioned that Gatekeeper isn’t keeping nation state adversaries awake at night.
Ironically, in the case of Wardle’s attack, applications don’t necessarily look for apps or libraries in other directories; it’s not common app behavior. He believes one way to approach fixing this is for Apple to perform a runtime check when executables start or libraries are load that determines if it’s from an untrusted source online or from Apple.
“If the application or dynamic library is from the Internet, let’s check to see if it conforms to the users’ settings, make sure it’s signed or from the App Store. We could do that, and that would generically stop an attack,” Wardle said. “When the Apple trusted executable launches the second executable that is unsigned and untrusted, their runtime hook would detect that. They already have a framework in place where they’re hooking runtime executions and examining things; I think they could extend it further to validate that.”