Following the disclosure of a critical SQL injection vulnerability in the software last week, as expected, attacks are being carried out against sites running old, unpatched versions of the content management system Joomla.
Experts warned that it’d be easy for an attacker to gain full control of a website and execute additional attacks through the vulnerability last Thursday and that’s exactly what has happened, according to researchers with the firm Sucuri.
Daniel Cid, the founder and CTO of the company wrote yesterday in a blogpost that only four hours after disclosures from both Jooma and Trustwave, the firm that discovered the vulnerability, attackers began narrowing their sights on two “popular Joomla sites.” Cid didn’t name the sites but claims that attackers attempted to extract the current sessions from logged in admin users, but were blocked by defense mechanisms.
Cid says attackers wasted no time deploying two scans. One was relatively harmless and looked for a SQL syntax error page that pops up following errors on Joomla systems running the old software.
The second one was a little scarier and involved a scan that requested the “admin user” session from a table on the CMS.
When the attackers discovered a website running an older, vulnerable version, then the leveraged the exploit and ran a payload to extract the user’s session.
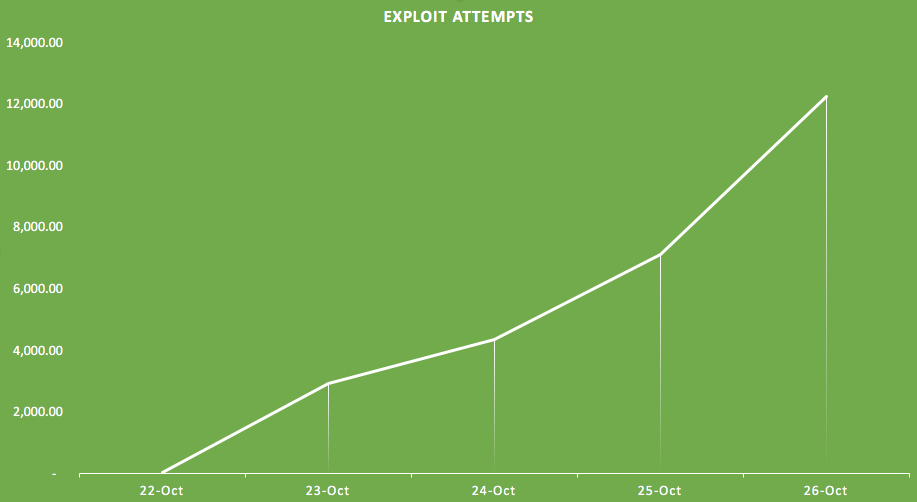
It should come as little surprise, but there was really an uptick in exploit attempts over the weekend. As indicated by the corresponding graph, attackers tried some 12,000 attempts on Monday.
The vulnerability previously existed in versions 3.2 to 3.4.4 of the CMS until developers at Joomla pushed a patch last week, but it appears multiple sites neglected to apply the update.
“What is very scary to think is that neither of these sites were patched at the time. The disclosure happened on a Thursday afternoon (evening in Europe), when many webmasters were already off for the day,” Cid wrote.