An out-of-the-blue tweet from a Dutch researcher kicked off an unprecedented 24-hour rumor mill yesterday concerning the arrest of Paunch, a hacker allegedly behind the notorious Blackhole Exploit Kit. The arrest, finally confirmed today by the head of the European Cybercrime Centre (EC3), is likely to put a dent in the shadowy cybercrime underworld.
Blackhole is the most well-known malware kit available on the darknet; the kit is leased out to criminals who use the many browser exploits available within the kit to infect users. Cybercriminals use malicious links to lead users to compromised sites and the exploit kit then will determine which exploits will work on the victim’s PC and use them to compromise the machine.
Troels Oerting, who runs the EC3 out of The Hague in the Netherlands, confirmed to TechWeek Europe that Paunch was in custody.
“I know it’s true, we got some information, but I cannot say anymore,” Oerting is quoted, adding that he could not share further details.
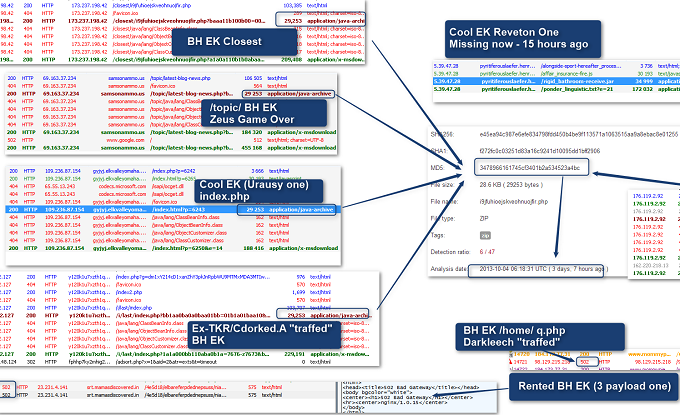
The rumor mill kicked off after a tweet from Fox-IT security researcher Maarten Boone announced Paunch’s arrest in Russia. Shortly thereafter, French security researcher Kafeine told Threatpost via email that the kit’s Java archive files had not been updated in almost four days, an indication something was afoot. He provided Threatpost with a graphic, above, that shows a number of Blackhole sites returning gateway errors or JAR files that have been ignored for days; Blackhole JAR files are updated sometimes twice daily.
Kafeine also said that distribution of the Reveton ransomware malware has moved from Blackhole to the WhiteHole Exploit kit. In addition, crypt[.]am, an online service allegedly run by Paunch was unreachable yesterday; the service is used to encrypt portions of the exploit kit.
Aleks Gostev, chief security expert for the Kaspersky Lab Global Research & Analysis Team, also confirmed via anonymous sources that the arrest was made.
“Three scenarios are [now] feasible: Blackhole can disappear, be taken over by other developers, or replaced by other exploit kits,” Gostev said. “What combinations of these scenarios will happen, we will see.”
In January, the Cool Exploit Kit surfaced online, also allegedly built and maintained by Paunch. Cool, however, is much pricier than its older brother, fetching close to $10,000 in monthly lease fees compared to $500 a month for Blackhole.
At the time, Cool made use of a number of browser zero-days that were meant to be kept private, while Blackhole, a hosted service, is a package of known exploits targeting patched bugs, generally browser redirects that force a victim’s browser to an attack site where more malware awaits. Recently, Blackhole shifted away from exclusively offering browser-based bugs, and began folding in exploits for Java, Adobe Reader and Flash.
In 2011, the source code for Blackhole leaked online, which just served to make the landscape for vulnerable organizations that much hairier. But that didn’t hurt business for Paunch and his gang, the alleged creator of Blackhole, who re-invested more than $100,000 in browser and browser plug-in vulnerabilities, according to a post on an underground forum reported by Krebs on Security in January of this year.