An adult-themed botnet was found by researchers and dismantled by Twitter last month. The Twitter-based botnet consisted of 86,262 bot accounts, and over the past six months blasted out 8.6 million tweets that attempted to lure males to pornographic, dating, hookup and cheating-spouse websites.
ZeroFOX’s Threat Research team made the discovery, which it said was unique because the botnet was active when found. “We rarely see these types of botnets in action. Doing so gave us unprecedented insights into how these operations work,” said Zack Allen, manager of threat operations at ZeroFOX.
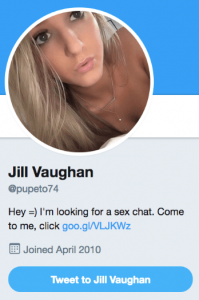
He said the botnet leveraged a vast network of algorithmically generated Twitter accounts used to distribute a payload URL that redirects to a variety of spammed pornography websites.
“By abusing short link services from Twitter and Google, the botnet engages with victims in two ways: either directly by quoting one of the target’s tweets, or by leaving the payload visible on their profile bio or pinned tweet,” said researchers.
The live analysis of the botnet allowed ZeroFOX to determine the campaign had amassed 30 million unique clicks from victims who clicked on shortcut URLs between February and June 2017.
The discovery is related to a large email spam botnet recently disclosed by Brian Krebs of KrebsOnSecurity. In both cases, the email spam and Twitter botnets leveraged similar tactics that drove victims to an identical network of pornographic websites, according to a ZeroFOX analysis posted online Sunday.
Those websites varied and were hosted on just five domains. Two of those domains were owned by California-based Deniro Marketing, according to ZeroFOX. Allen suspects that Deniro Marketing works as an advertising affiliate and earns commission when generating traffic and sign-ups at the adult-themed sites.
Deniro Marketing declined a Threatpost request for comment for this story.
 The unique nature of Twitter botnets is that they don’t used hijacked or paid resources as traditional botnets do. Also, Twitter botnets are free and instead of pelting inboxes with spam they target social media accounts.
The unique nature of Twitter botnets is that they don’t used hijacked or paid resources as traditional botnets do. Also, Twitter botnets are free and instead of pelting inboxes with spam they target social media accounts.
“The security community has gotten very good at defending the inbox against spam and phishing attacks,” Allen said. “That’s just not the case with social platforms.”
Allen said the perpetrators have devised a number of anti-detection techniques that include using “aged” Twitter accounts designed to thwart Twitter’s anti-fraud algorithm.
Links were embedded in Twitter messages and in Twitter bot bios. Operators either used Google’s goo.gl or Twitter’s t.com URL shortening service. Once a link is click, the user is taken through a series of redirects.
In order to avoid detection by anti-spam services the goo.gl shortcut links redirects to a “rotator” website.
“This rotator ingests a connection from the goo.gl redirect, and redirects the user again based on a simple user-agent check. If the request comes from an automated program like Python’s request library or cURL, it redirects the connection back to Twitter or Google,” researchers said. “Once the rotator deems the client as ‘legitimate’, it then sends the connection via another redirect to the final URL destination.”
“These affiliate websites would ask people for PII, email or SMS sign-up information in order to connect to services. They tricked the user into signing up. They’d promise people near you are waiting and all you have to do is sign-up and you’ll have access to everyone. Once they make that conversion, then they get paid,” Allen said.
ZeroFOX said the Twitter-based spam campaign most likely had a centralized command-and-control account, though none was identified. It also said the campaigns steered clear of luring people to malicious websites loaded with malware. Instead Twitter messages focused on conning targets to hand over an email or cellphone number.










