Google began in January flashing warnings in the Chrome address bar that a page was “Not Secure” if password or payment card data fields were present.
“Since the change in Chrome 56, there has been a 23 percent reduction in the fraction of navigations to HTTP pages with password or credit card forms on desktop, and we’re ready to take the next steps,” said Emily Schechter of the Chrome Security Team.
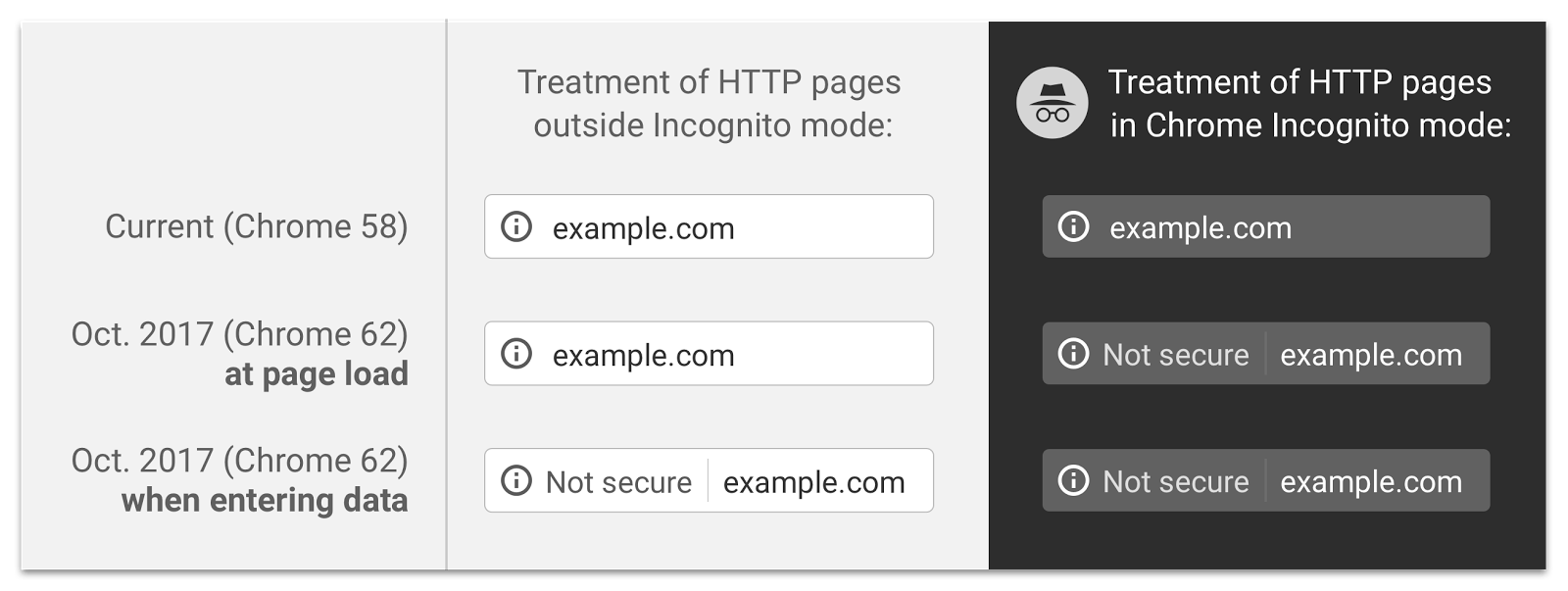
Today, Schechter announced that with the release of Chrome 62, scheduled for some time in October, Google will also show the “Not Secure” warning when users enter data on a HTTP page and for any HTTP page a user visits while in the browser’s incognito mode.
Chrome 62 (October) will mark HTTP pages with user-entered data and all HTTP pages in Incognito mode as "not secure" https://t.co/A3bjJ9Xbyk pic.twitter.com/xB6JSZ2N2U
— emily schechter (@emschec) April 27, 2017
“Passwords and credit cards are not the only types of data that should be private,” Schechter said. “Any type of data that users type into websites should not be accessible to others on the network, so starting in version 62 Chrome will show the ‘Not secure’ warning when users type data into HTTP sites.”
HTTP pages send data in the clear from the browser to a webserver. With more than half of the web already encrypted on average, awareness of data protection is improving. But especially when browsing in incognito mode, users may have a false sense of security that their activity online may be secure.
“When users browse Chrome with Incognito mode, they likely have increased expectations of privacy,” Schechter said. “However, HTTP browsing is not private to others on the network.”
Schechter also said today that Chrome will eventually display the Not Secure warning for all HTTP pages, regardless of whether the user is browsing in incognito mode.
Prior to Chrome 56 when the first pages began being marked Not Secure, the browser showed more of a neutral indicator, a gray exclamation point inside a circle.
“This doesn’t reflect the true lack of security for HTTP connections,” Schechter said in January. “When you load a website over HTTP, someone else on the network can look at or modify the site before it gets to you.”
More and more websites are loading HTTPS pages every day, and movements such as Let’s Encrypt, which provides free TLS certificates, are in large part responsible for the surge. Amazon, Cloudflare and others have simplified the process of obtaining and implementing TLS certs, and the result has been a rapid growth in the number of pages served over HTTPS. Last October, for example, Mozilla telemetry for the first time showed more than 50 percent of internet traffic for a single day was encrypted. In February, that jumped to more than 50 percent of internet traffic for a two-week period.
“I just love to think about how much data we’re talking about,” said Josh Aas, executive director of the Internet Security Research Group and former Mozilla developer in an October interview with Threatpost. “The reality on the ground is there’s a whole bunch of data that’s encrypted now that wouldn’t have been before. Going from 40 percent (39.5 percent when Let’s Encrypt entered its public beta in December 2015) to 50 percent is a massive amount. It’s hard to imagine what 10 percent of daily transfer on the Internet is like.”