The RIG Exploit Kit remains fairly active despite an overall decline in such activity, and of late, it’s been spreading a fairly new variant of ransomware called CryptoShield.
The main culprit is an attack group known for using EITest to deliver malware; it has been infecting victims’ machines via malvertising campaigns and compromised websites, and since the start of the year, CryptoShield has been the primary payload.
Brad Duncan, a handler at the SANS Institute Internet Storm Center said EITest activity has ramped up of late.
“I’m seeing a fair amount of the traffic,” Duncan said of EITest, which has been a known offender since 2014. “EITest is known to distribute other types of malware, but I’ve been seeing a lot of CryptoShield ransomware from it during the past week or so.”
CryptoShield is a descendant of CryptoMix and was discovered by researcher Kafeine as it spread in EITest campaigns. EITest injects JavaScript into sites or advertisements, and that code calls out to the attacker for the ransomware payload.
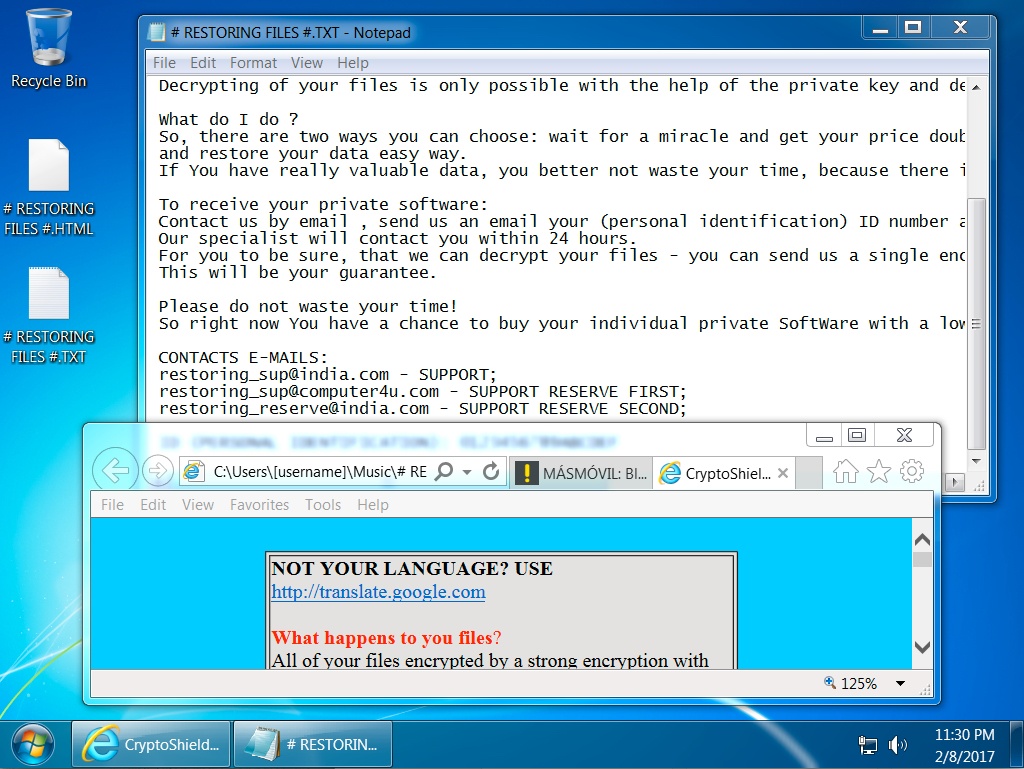
An analysis published by BleepingComputer in January said that once CryptoShield infects a computer, it creates a unique ID and encryption key for the machine, and encrypts files stored on the local drive. All encrypted files are tagged with a .CRYPTOSHIELD extension, researcher Lawrence Abrams said.
Duncan described a typical attack in a SANS ISC post published today. Once a victim’s browser lands on an infected website or on one hosting a malicious ad, the host machine is infected. Two popups are generated, Duncan said, one an application error, and another a Windows User Account Control prompt. After clicking through both prompts, a text file displayed on the desktop with decryption and payment instructions.
Duncan identified two RIG Exploit Kit IP addresses and domains (194[.]87[.]93[.]53 for need[.]southpadreforsale[.]com, and 194[.]87[.]93[.]53 for star[.]southpadrefishingguide[.]com), as well as 45[.]63[.]115[.]214 for post-infection communication from CryptoShield. Duncan said that IPs and domains associated with RIG traffic change daily, sometimes more frequently, and that these IPs have likely been changed.
Duncan and Abrams said that victims are likely exclusively infected over the web and spread via RIG, rather than email-based campaigns. RIG, meanwhile, continues to assert itself as one of the busiest exploit kits in circulation. With monster kits such as Angler put out of commission as recently as last summer, along with a number of others, the reliance on exploit kits for malware propagation has noticeably diminished.
“Rig EK is the most prevalent exploit kits I’m seeing at the moment. It’s definitely not the only one,” Duncan said. “Other exploit kits like Magnitude and Sundown are still active, and I see indicators of those on a daily basis. But volume-wise, I see more indicators for Rig EK. The majority (50 percent or more) of all exploit kit indicators I’m finding are for Rig.”