Researchers are learning more about the cyberespionage group Bronze Butler. While the gang has been targeting Japanese heavy industry since 2012, not much is known about the group’s current modus operandi.
In a report released Thursday by the Counter Threat Unit at SecureWorks, a subsidiary of Dell Technologies, researchers paint the most complete picture yet of the group, also known as Tick.
“In the past 12 months, (SecureWorks) investigated several intrusions carried out by the Bronze Butler threat group at various Japanese organizations. The group’s activities have largely remained undetected since at least 2012, but it has likely been active for much longer,” said Matthew Webster, senior security researcher with SecureWorks, in an interview with Threatpost.
Since its inception, SecureWorks believes Bronze Butler has operated out of People’s Republic of China. The group has focused on exfiltrating intellectual property and other confidential data from Japanese companies involved in critical infrastructure, heavy industry, manufacturing and international relations.
In its report released this week, SecureWorks uncovers shifting tactics and strategies used by the group. According to researchers, Bronze Butler has bolstered its skillsets when it comes to exploiting zero-days, developing unique malware tools and has been increasingly become effective at exploiting a desktop management tool used by sysadmins in Japan.
What is known about Bronze Butler? Besides likely residing in China and targeting Japan, researchers say the group has used spear phishing, strategic web compromises and zero-day vulnerabilities to infiltrate targeted systems.
“The group has used phishing emails with Flash animation attachments to download and execute (customized) malware, and has also leveraged Flash exploits for strategic web compromises attacks,” researchers wrote.
According to SecureWorks when investigating several intrusions into Japanese organizations it found Bronze Butler leveraging an Adobe Flash zero-day vulnerability in a popular Japanese corporate desktop management tool called SKYSEA Client View.
“The fact that this threat group could discover and weaponize a vulnerability in a popular regional IT product, gives further insight into the group’s capability and certainly their dedication to successfully compromising their target victims,” Webster said.
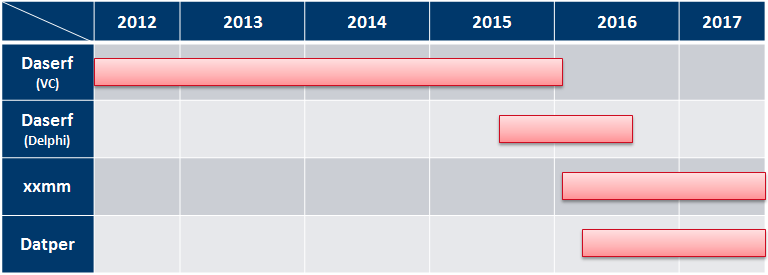
SecureWorks said Bronze Butler has a proficiency for developing and deploying proprietary malware tools exclusive to the group. One of those tools is malware called Daserf; it functions as a backdoor giving adversaries a remote shell to execute commands, upload and download data, capture screenshots, and log keystrokes.
The group appears to have developed two versions of this tool over time. In 2016, the group appears to shift from using Daserf to two remote access trojans (RATS) called xxmm and Datper, Webster said.
According to a report published earlier this year by Palo Alto Networks’ Unit 42, Bronze Butler’s Daserf malware has been observed sharing infrastructure with similar backdoor malware Minzen as well as Gh0st RAT and a RAT identified as 9002 RAT along with the downloader HomamDownloader.
As for intent, Bronze Butler targets almost exclusively sensitive business and sales-related information. To a lesser extent it also goes after business and sales-related information along with network and system configuration files.
“The focus on intellectual property, product details, and corporate information suggests that the group seeks information that they believe might be of value to competing organizations,” according to the report. Researchers add the diverse targeting of Bronze Butler suggests that various group leaders may task the group to carry out multiple goals.
“The extent of the group’s activities is probably still to be fully realized, so we assess that Bronze Butler is still an active and very capable component of the threat landscape,” Webster said.