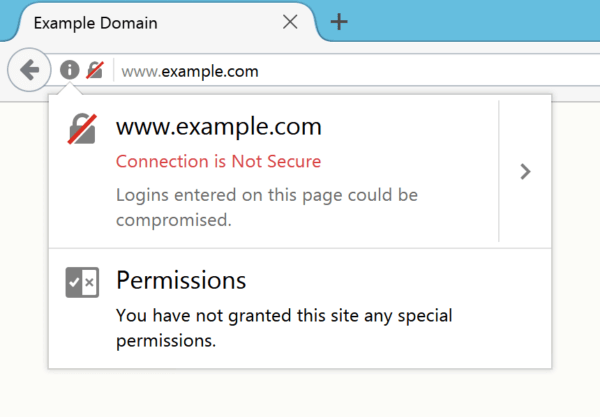
Mozilla Foundation took steps with the release of Firefox 51 on Tuesday to communicate more clearly to users when they land on a HTTP website collecting personal information such as passwords that the site may not be secure.
Going forward, Firefox will display a gray lock icon with a red strikethrough in the address bar. Should the user click on the lock, a dialog box will pop up with text indicating the connection is not secure. Eventually, Mozilla said, this will be the experience for all HTTP pages.
“To continue to promote the use of HTTPS and properly convey the risks to users, Firefox will eventually display the struck-through lock icon for all pages that don’t use HTTPS, to make clear that they are not secure,” a post to the Mozilla security blog said. “As our plans evolve, we will continue to post updates but our hope is that all developers are encouraged by these changes to take the necessary steps to protect users of the Web through HTTPS.”
Mozilla’s move follows similar efforts by Google with its Chrome browser. Late last year, Google said starting this month, Chrome users who navigate to some HTTP sites will be notified they’re on a site that isn’t secure.
On Tuesday, Mozilla also patched several critical security vulnerabilities. Topping the list of critical vulnerabilities is one described as a “excessive JIT code allocation allowing the bypass of ASLR and DEP.” A JIT (just in time) code is a default processes that handles how Java request are made, allowing for compiled byte code to run directly versus taking an additional step of interpreting the code and then running it. The ASLR (address space layout randomization) guards against buffer-overflow attacks and DEP (data execution prevention) protects operating systems from virus attacks launched from Window’s system memory locations.
“JIT code allocation can allow for a bypass of ASLR and DEP protections leading to potential memory corruption attacks,” according to the security advisory. The vulnerability (CVE-2017-5375) impacts only Firefox 51.
Other critical vulnerabilities include a use-after-free flaw (CVE-2017-5376) related to manipulating XSL in XSLT documents. A second critical memory corruption flaw (CVE-2017-5377) was found impacting the open source 2D graphics library called Skia.
Of the advisories rated high three were use-after-free vulnerabilities related to web animations (CVE-2017-5379), DOM manipulation of SVG content (CVE-2017-5380) and a bug related to the Firefox Media Decoder (CVE-2017-5396).
Several critical vulnerabilities were also found in Mozilla’s Extended Support Release (ESR) version of the Firefox browser. Firefox ESR is a custom version of the Mozilla Firefox browser specifically designed for the special browser requirements relied upon by schools, government agencies and businesses that maybe leery about forced browser updates that could disrupt line-of-business browser-based applications.
One of those Firefox ESR critical security alerts (CVE-2017-5374) was a memory safety bug that with enough effort could be exploited to run arbitrary code, according to the advisory. Another critical memory safety bug was found in Firefox and Firefox ESR 45.7 that also could be exploited to run arbitrary code. Both Firefox ERS vulnerabilities were patched.
Firefox 51 browser also became the first of the major browsers to display a warning to users who run into a site that doesn’t support TLS certificates signed by the SHA-2 hashing algorithm. According to Mozilla, SHA-1 warnings start this week for beta Firefox users and will roll out to all other users sometime after that. The move is meant to protect users from collision attacks, where two or more inputs generate the same hash value.