Google said it has disabled offending accounts involved in a widespread spree of phishing emails today impersonating Google Docs.
The emails, at the outset, targeted journalists primarily and attempted to trick victims into granting the malicious application permission to access the user’s Google account. It’s unknown how many accounts were compromised, or whether other applications are also involved. Google advises caution in clicking on links in emails sharing Google Docs.
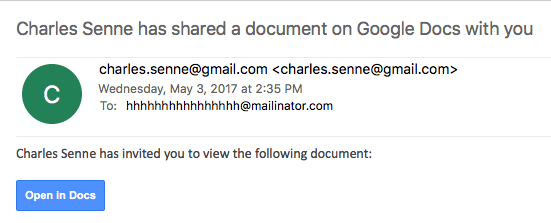
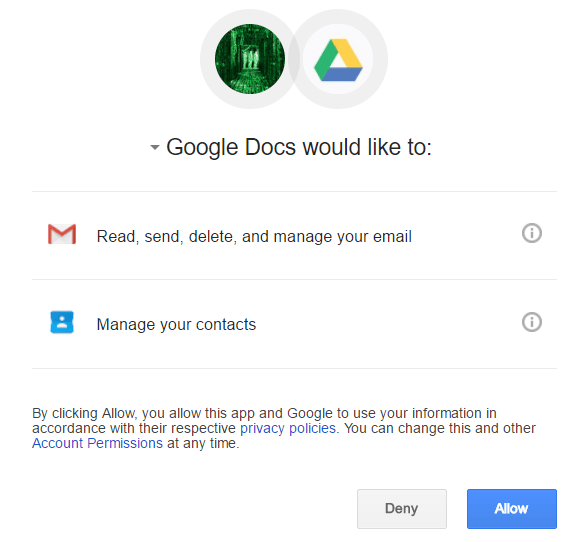
The messages purport to be from a contact, including contacts known to the victim, wanting to share a Google Doc file. Once the “Open in Docs” button is clicked, the victim is redirected to Google’s OAUTH2 service and the user is prompted to allow the attacker’s malicious application, called “Google Docs,” below, to access their Google account and related services, including contacts, Gmail, Docs and more.
@zeynep Just got this as well. Super sophisticated. pic.twitter.com/l6c1ljSFIX
— Zach Latta (@zachlatta) May 3, 2017
“We have taken action to protect users against an email impersonating Google Docs, and have disabled offending accounts,” a Google spokesperson told Threatpost. “We’ve removed the fake pages, pushed updates through Safe Browsing, and our abuse team is working to prevent this kind of spoofing from happening again. We encourage users to report phishing emails in Gmail.”
OAUTH is an authentication standard that allows a user to authorize third party applications access to an account. The attempt to steal OAUTH tokens is a departure from traditional phishing attacks that target passwords primarily. Once the attacker has access to the victim’s account, the phishing message is sent along to the compromised contact list.
“Considering how indiscriminate the targeting is, it doesn’t seem to be anything else but trying to exploit a weakness in how end users can be tricked into granting access to their Google accounts,” said Alvaro Hoyos, CISO at OneLogin.
While this attack is likely the work of a spammer, nation-state attackers including APT28, aka Fancy Bear or Sofacy, have made use of this tactic. APT28 has been linked to last summer’s attacks attempting to influence the U.S. presidential elections. The group has long been targeting political entities, including NATO, and uses phishing emails, backdoors and data-stealing malware to conduct espionage campaigns against its targets.
“I don’t believe they are behind this though because this is way too widespread,” said Jaime Blasco, chief scientist at AlienVault. “Many people and organizations have received similar attempts, so this is probably something massive and less targeted.”
Bojan Zdrnja, a handler with the SANS Internet Storm Center, identified a number of domains involved, all with different TLDS for googledocs[.]g-docs[.]xxxx or googledocs[.]docscloud[.]xxxx. Many of those domains have been taken down; Google also quickly updated Safe Browsing and Gmail with warnings about the phishing emails and attempts to steal personal information.
Anyone who allowed the malicious app access to their accounts can revoke those permissions at myaccount.google.com.
“Google has a systemic issue,” said Eric Hodge of Cyber Scout. “Its OAUTH processes are subject to fakery and therefore phishing attacks. The question is will Google address the issue systemically (adding TLS certificate servers for individuals) or will they just try to address this particular attack?”