Google always seems to be busy fortifying Gmail–the latest steps by the company resolve to bolster message encryption and deter attackers from censoring or altering messages before they’re delivered to users.
The company announced last week it would begin rolling out warnings in the coming months to inform users if they’ve received a message through a non-encrypted connection.
The moves partially stems from research carried out collaboratively by researchers from Google, the University of Michigan, and the University of Illinois. 10 researchers examined in a global sense how accepted and effective security mechanisms for email, such as protocols STARTTLS, DKIM, and DMARC, have been over the last few years.
The paper “Neither Snow Nor Rain Nor MITM… An Empirical Analysis of Email Delivery Security,” (.PDF) was published last Thursday, in a post to Google’s Online Security Blog.
The researchers looked at 700,000 SMTP servers associated with the Alexa top million domains and discovered 82 percent supported TLS, but only 35 percent of those were properly configured to allow server authentication. A scant 1.1 percent, meanwhile, specified a DMARC authentication policy, the paper claims. Those poor numbers can partially be chalked up to the behavior of several countries, the researchers argue.
Tunisia, Iraq, Papua New Guinea, Nepal, Kenya, Uganda, and Lesotho are the biggest culprits, guilty of what the researchers call “STARTLS stripping.” Tunisia is far and away the worst offender – 96 percent of Gmail messages sent from the nation are downgraded to cleartext, the researchers state.
STARTTLS, an extension to SMTP, ensures messages and any associated metadata are encrypted.
For the study, the researchers looked at SMTP logs for 16 months, spanning back to January 2014, in Gmail and other domains, to see what percentage of messages were being prevented from being encrypted. Roughly a quarter of messages sent from the other nations, were stripped of TLS.
Through STARTTLS stripping an attacker or organization could break encryption by tampering with the fail-open design of STARTTLS and launching a downgrade attack, causing an error in the handshake, something which would revert the text to cleartext.
“The fail-open nature of STARTTLS and the lack of strict certificate validation reflect the need for interoperability amidst the gradual rollout of secure mail transport, and they embody the old adage that “the mail must go through.” Unfortunately, they also expose users to the potential for man-in-the-middle attacks, which we find to be so widespread that they affect more than 20 percent of messages delivered to Gmail from several countries,” the paper reads.
While it’s easy to focus on the negative, the paper also showed the researchers how email security has been able to grow over the past two years, as well.
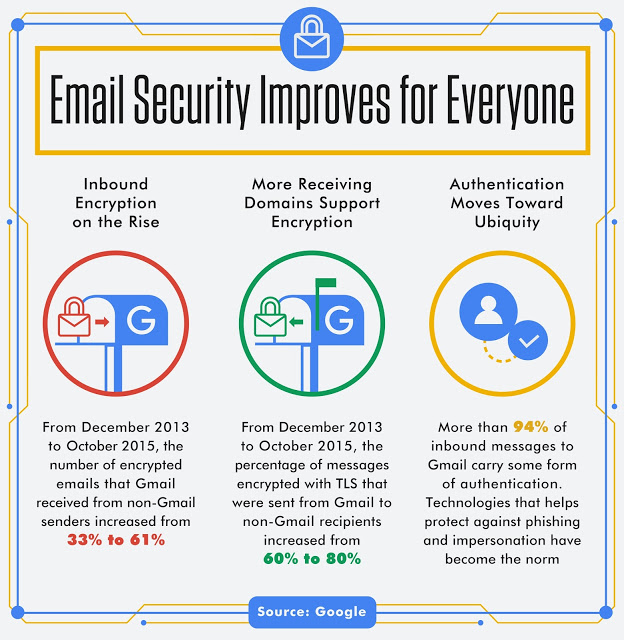
The researchers note that the number of encrypted emails to Gmail from non-Gmail senders was up (33 percent to 61 percent), over the two year span, and that the percentage of messages encrypted with TLS from Gmail users to non-Gmail users also increased (60 percent to 80 percent).
In a blog post two of the paper’s authors, Elie Bursztein, with Google Anti-Fraud and Abuse Research division, and Nicolas Lidzborski, a Gmail Security Engineering Lead, claim the company its working with the Messaging, Malware and Mobile Anti-Abuse Working Group (M3AAWG) to promote more widespread TLS adoption.
The new warnings should help alert users whether or not messages they receive are legitimate, and give them a heads up whether they’ve been censored or altered.
The moves build on an announcement by the company last month that it would soon begin rejecting messages that fail to pass DMARC specifications. In a statement published to DMARC.org, Google said that by next summer it would ensure messages conform to the protocol, which stands for Domain-based Message Authentication, Reporting and Conformance, a move that many experts expect to tone down email address spoofing.
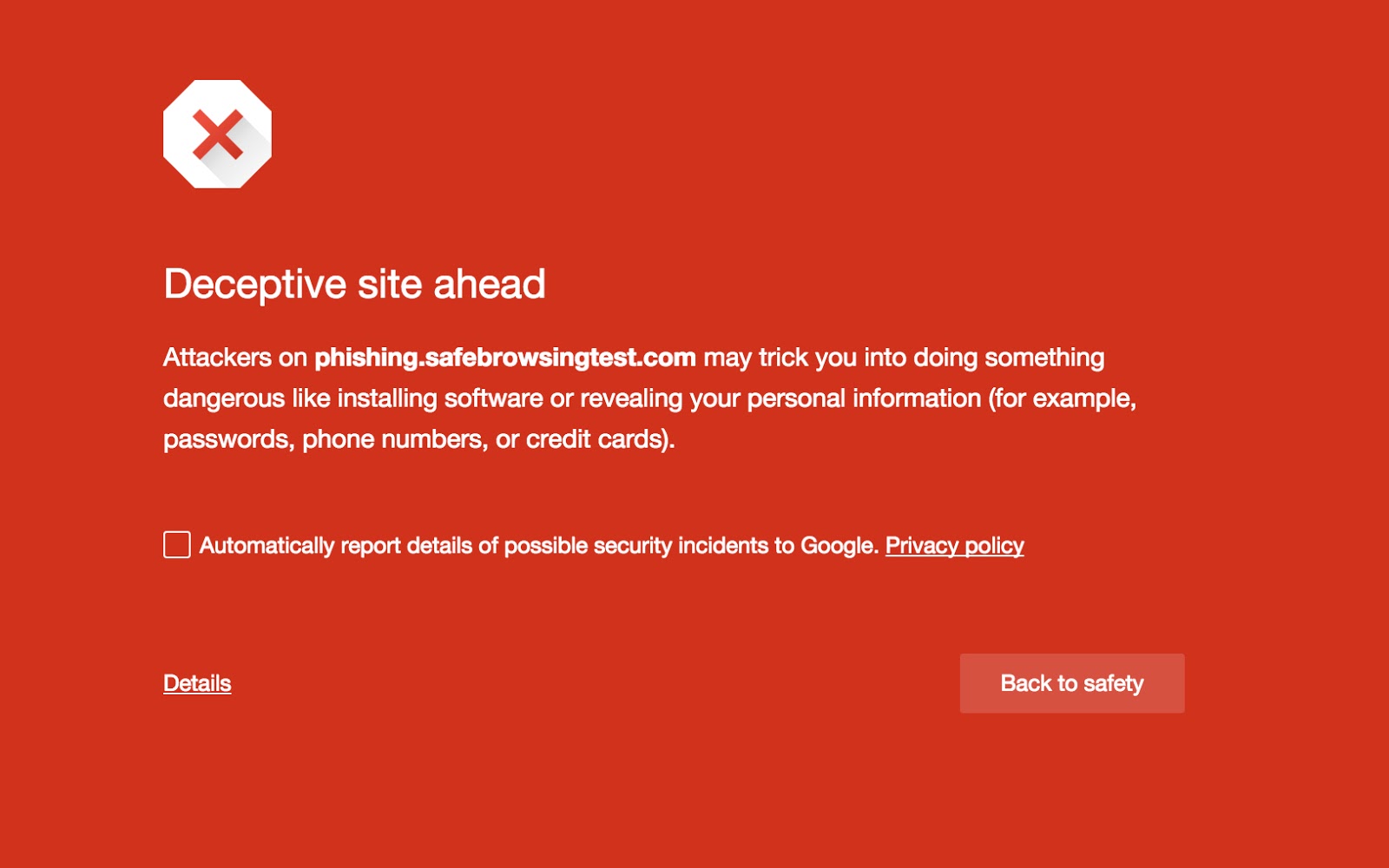
Google also announced it would take another step to secure users last week by broadening the Safe Browsing mechanism in its browser to include social engineering scams. To crack down on attackers who’ve been using more deceptive attack vectors, going forward, the browser will notify users if they’ve stumbled across a suspicious-looking site. If Google identifies a site that contains what the company deems social engineering content, it will warn users in a notification similar to its malware and phishing notifications.
The move is mostly to combat attacks that convince users they need to do something they don’t – like downloading a new version of Chrome, calling an expensive tech support line, or entering their password into a bogus version of Gmail.