A malware campaign utilizing bogus popups that alert users to a missing web-font is targeting Google Chrome and Firefox browser users. The popups contain a malicious JavaScript file that initiates the download of either the NetSupport Manager remote access tool (RAT) or Locky ransomware.
The campaigns were spotted by Brad Duncan with both the SANS Internet Storm Center and Palo Alto Networks’ Unit 42. He said the attacks relate to similar malware campaigns, dubbed EITest, that date back to December 2016.
In all cases victims are lured to a booby-trapped website that generates a bogus popup message informing the user the webpage they are trying to view cannot display correctly because the browser is missing the correct “HoeflerText” font (see below).
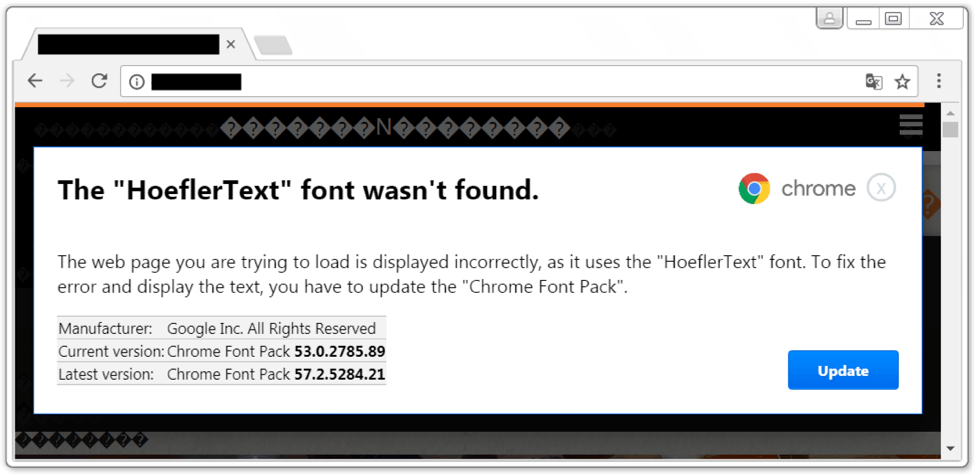 The message then prompts the user to fix the error. “These notifications also had an ‘update’ button. When I clicked it, I received a JavaScript file named Win.JSFontlib09.js. That JavaScript file is designed to download and install Locky ransomware,” Duncan wrote.
The message then prompts the user to fix the error. “These notifications also had an ‘update’ button. When I clicked it, I received a JavaScript file named Win.JSFontlib09.js. That JavaScript file is designed to download and install Locky ransomware,” Duncan wrote.
In another case, he said a Chrome HoeflerText font update delivers the file “Font_Chrome.exe” file. When executed, it retrieves follow-up malware that installs a NetSupport Manager RAT, according to researchers.
“This is significant, because it indicates a potential shift in the motives of this adversary,” Duncan wrote. “It’s yet to be determined why EITest HoeflerText popups changed from pushing ransomware to pushing a RAT. Ransomware is still a serious threat, and it remains the largest category of malware we see on a daily basis from mass-distribution campaigns.”
He theorizes RATs are becoming more popular with threat actors behind the campaign because they give attackers more capabilities on infected PCs and are more flexible than single-purpose ransomware.
Driving traffic to those malicious webpages are a number of spam campaigns.
“In recent days, I’ve noticed multiple waves of malspam every weekday. It gets a bit boring after a while, but as 2017-08-31 came to a close, I noticed a different technique from this malspam,” Duncan said.
He said the malicious spam had links to fake Dropbox pages. “If you viewed the pages in Chrome or Firefox, they showed a fake notification stating you don’t have the HoeflerText font. These fake notifications had an “update” button that returned a malicious JavaScript (.js) file.”
Duncan said using Internet Explorer or Microsoft Edge on booby-trapped webpages did not trigger the HoeflerText’ popup. Rather, “victims who use Microsoft Internet Explorer as their web browser will get a fake anti-virus alert with a phone number for a tech support scam.”
Emails were botnet-based and originated from various IP addresses around the world and spoof the Dropbox no-reply@dropbox.com email address, according to the research.
A sample subject line read: “Please verify your email address”. The body of the message also states, “We just need to verify your email address before your sign up is complete.” A “verify your email” button masks the URL address that links to the malicious site that triggers the EITest HoeflerText popups.
“Users should be aware of this ongoing threat. Be suspicious of popup messages in Google Chrome that state: The ‘HoeflerText’ font wasn’t found. Since this is a RAT, infected users will probably not notice any change in their day-to-day computer use. If the NetSupport Manager RAT is found on your Windows host, it is probably related to a malware infection,” Duncan said.










