Insecure backend databases and mobile apps are making for a dangerous combination, exposing an estimated 280 million records that include a treasure-trove of private user data. According to a report by Appthority, more than 1,000 apps it looked at on mobile devices leaked personally identifiable information that included passwords, location, VPN PINs, emails and phone numbers.
Appthority Mobile Threat Team called the vulnerability HospitalGown and said the culprit behind the threat are misconfigured backend storage platforms including Elasticsearch, Redis, MongoDB and MySQL.
“HospitalGown is a vulnerability to data exposure caused, not by any code in the app, but by the app developers’ failure to properly secure the backend servers with which the app communicates,” wrote the authors of the report released Wednesday.
According to Seth Hardy, director of security research, the problem is a byproduct of insecure database instillations that made headlines in February. That’s when misconfigured and insecure MongoDB, Hadoop and CouchDB installations became popular extortion targets for hackers who were scanning for vulnerable servers to attack.
The weak link in the chain when it comes to HospitalGown are the insecure servers that apps connect to, Hardy said. During the course of Appthority’s investigation, it found 21,000 open Elasticsearch servers, revealing more than 43 terabytes of exposed data.
In one scenario, the attacker looks for vulnerabilities in the space between the vendor’s mobile application and the app’s server side components, according to researchers. “The servers for most mobile applications are cloud based and accessible via the Internet, this allows a bad actor to skip the long and potentially many-layered ‘compromise’ stage of an attack, accessing company data directly from a database that is impossible for the enterprise to see or secure,” they wrote.
Researchers said vulnerable mobile apps it found ran the gamut, from office productivity, enterprise access management, games, dating to travel, flight and hotel applications. Any personal identifiable data a user shared with the app was vulnerable to possible exfiltration by a hacker.
“These servers were accessible from the Internet, lacked any means of authentication to prevent unwanted access to the data they contained, and failed to secure transport of data, including PII, using HTTPS: conventions,” according to the report. While this is a strictly a data security issue, Appthority said, attacks can quickly escalate and personal information could easily be leveraged in a spear phishing attack or brute force attack.
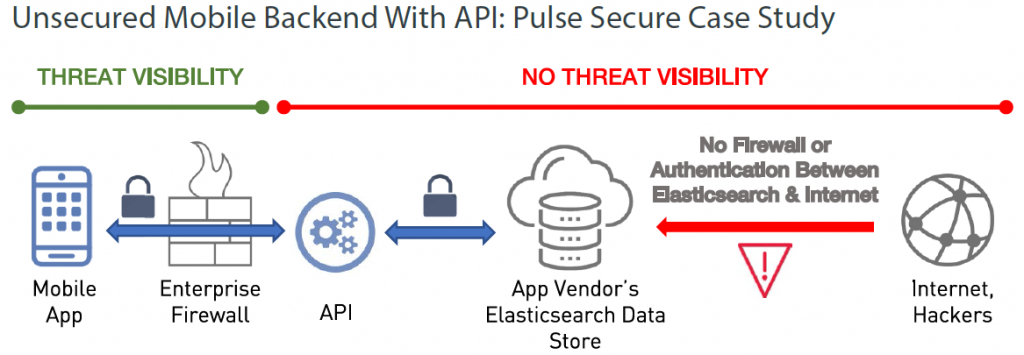
In its report, AppThority showed how a mobile VPN app called Pulse Workspace, used by enterprises, government agencies and service providers, leaked data. While Pulse Workspace created an API to secure front-end Elasticsearch access, the backend, and all of the app’s data records, were exposed and leaked Pulse customer data. AppThority notified Pulse Workspace and its customers of the vulnerability, which have since been fixed.
Appthority is careful to point out that of the platforms it examined – Elasticsearch, Redis, MongoDB, and MySQL – each had plugins to allow for proper public exposure on the internet. “Best practices on secure data stores is just not being adopted in too many cases,” Hardy said.
Elasticsearch, for example, has a bevy of security and data protection capabilities, such as being able to encrypt all the data that’s on the platform.
Increasing the risk of HospitalGown type-attacks is that fact that many apps Appthority looked at seemed benign in terms of shared user data. But, increasingly apps have advertising components that collect personal identifiable data that can be mined by hackers for phishing or ransomware attacks.
App developers and system administrators need to know where their data is stored and make sure it is secured, Hardy told Threatpost. Appthority also recommends:
“Contact any vendors for which your enterprise uses a mobile app. Ask them for a letter from their legal department that confirms their app’s backend is secured following best practices for the backend platform. Request that they limit the amount of personal information or site credentials stored on backend databases to the minimum needed for app functionality, and protect the data via encryption.”